XLoader malware steals logins from macOS and Windows systems
A highly popular malware for stealing information from Windows systems has been modified into a new strain called XLoader, which can also target macOS systems.
XLoader is currently being offered on an underground forum as a botnet loader service that can “recover” passwords from web browsers and some email clients (Chrome, Firefox, Opera, Edge, IE, Outlook,Thunderbird, Foxmail).
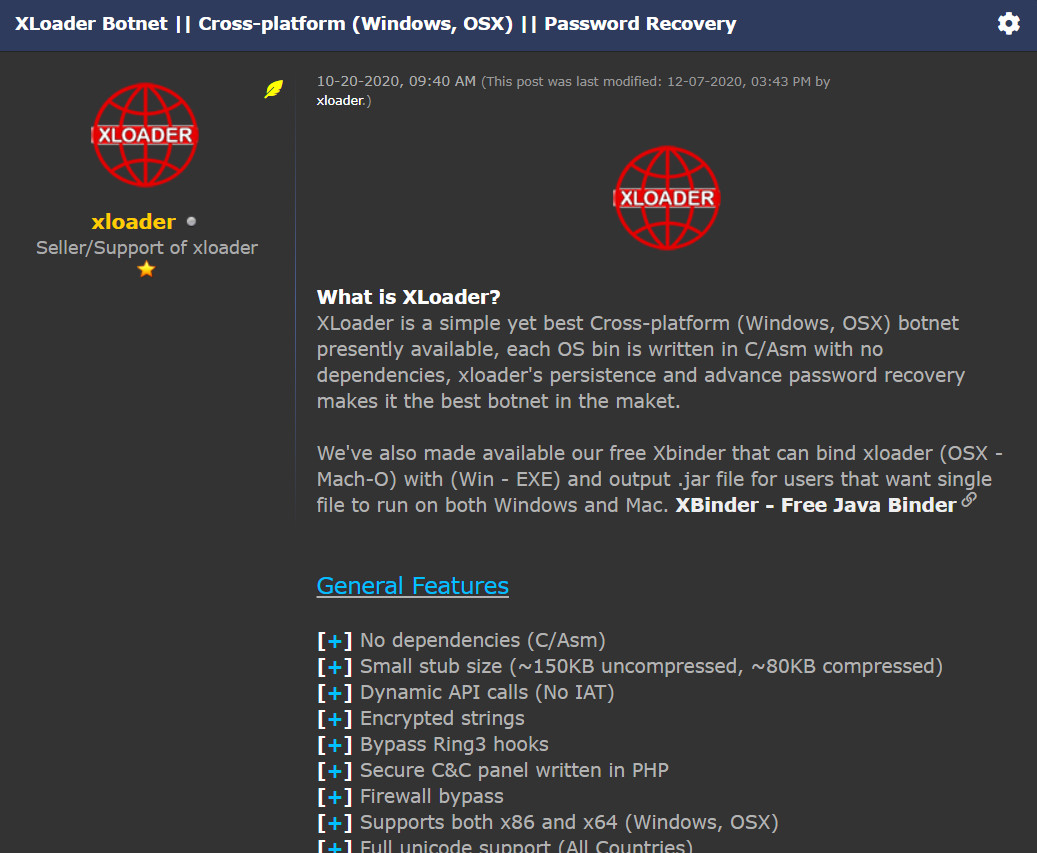
Derived from the Formbook info-stealer for Windows, XLoader emerged last February and has grown in popularity, advertised as a cross-platform (Windows and macOS) botnet with no dependencies.
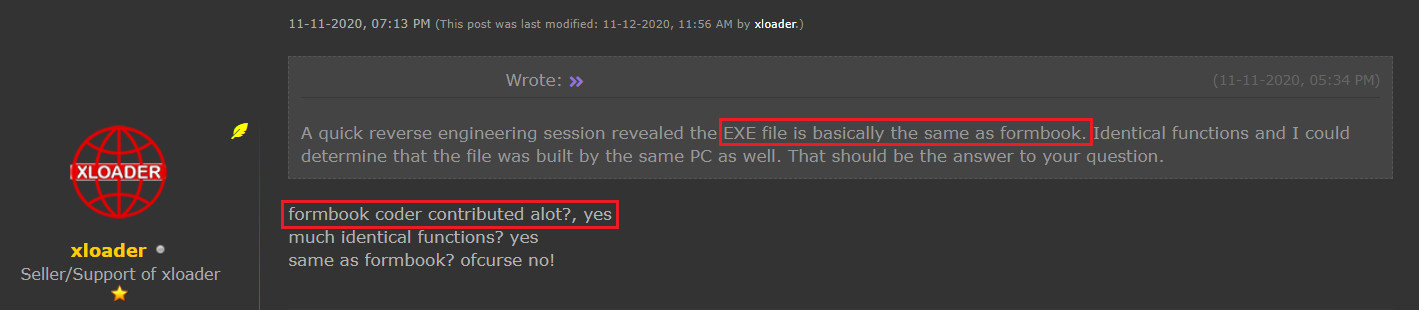
The connection between the two malware pieces was confirmed after a member of the community reverse-engineered XLoader and found that it had the same executable as Formbook.
The advertiser explained that Formbook’s developer contributed a lot to creating XLoader, and the two malware had similar functionality (steal login credentials, capture screenshots, log keystrokes, and execute malicious files).
Customers can rent the macOS malware version for $49 (one month) and get access to a server that the seller provides. By keeping a centralized command and control infrastructure, the authors can control how clients use the malware.
The Windows version is more expensive as the seller asks $59 for a one-month license and $129 for three months.
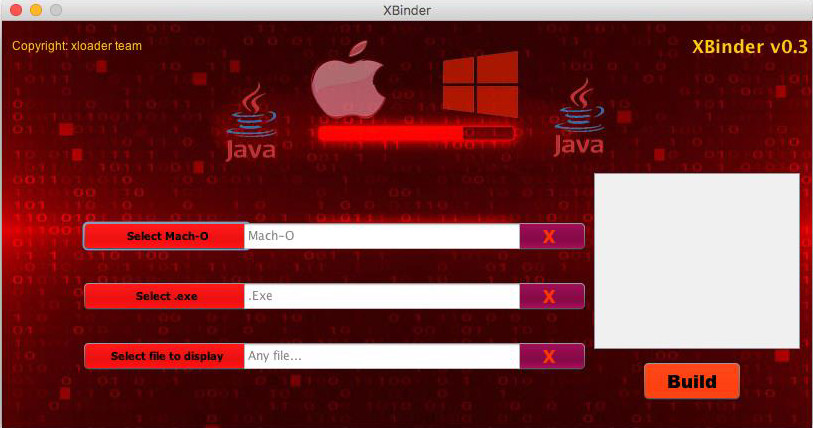
As mentioned in the advertisement, the makers of XLoader also provide a Java binder for free, which allows customers to create a standalone JAR file with the Mach-O and EXE binaries used by macOS and Windows.
Tracking XLoader 6-month activity up to June 1st, malware researchers at Check Point saw requests from 69 countries, indicating a significant spread across the globe, with more than half of the victims being in the United States.
Although Formbook is no longer advertised on underground forums, it continues to be a prevalent threat. It was part of at least 1,000 malware camapaigns over the past three years and according to AnyRun’s malware trends, the info-stealer takes fourth place over the past 12 months, after Emotet
If Formbook’s popularity is any indication, XLoader is likely to be more prevalent given that it targets the two most popular operating systems used by consumers.
Check Point researchers say that XLoader is stealthy enough to make it difficult for a regular, non-technical user to spot it.
They recommend using macOS’ Autorun to check the username in the OS and to look into the LaunchAgents folder [/Users/[username]/Library/LaunchAgents] and delete entries with suspicious filenames (random-looking name).
Yaniv Balmas, Head of Cyber Research at Check Point Software, says that XLoader is “is far more mature and sophisticated than its predecessors [i.e. Formbook].”
macOS’s growing popularity exposed it to unwanted attention from cybercriminals, who are now seeing the OS as an attractive target.
“While there might be a gap between Windows and MacOS malware, the gap is slowly closing over time. The truth is that MacOS malware is becoming bigger and more dangerous” - Yaniv Balmas
The researcher believes that more malware families will adapt and add macOS to the list of supported operating systems.
XLoader malware steals logins from macOS and Windows systems



3175x175(CURRENT).thumb.jpg.b05acc060982b36f5891ba728e6d953c.jpg)
Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.