Apple has released iOS 16.5.1, iPadOS 16.5.1, macOS 13.4.1 with security fixes for actively exploited vulnerabilities. It has also released an emergency update for older iPhones, Macs and iPads.
Apple patches actively exploited vulnerabilities in iOS, macOS, iPadOS and watchOS
The first of the 2 critical security issues was a kernel level bug. The issue, which has been tracked as CVE-2023-32434, could have allowed a malicious app to execute arbitrary code with kernel privileges. Apple says the problem affected iPhones and iPads that were running on older versions of operating systems that were released before iOS 15.7 and iPadOS 15.7.
The bug patched an integer overflow with improved input validation. The Cupertino company credited three security researchers from Kaspersky; Georgy Kucherin, Leonid Bezvershenko and Boris Larin for finding and reporting the bug to Apple. These zero-day exploits were revealed by the Russian cybersecurity firm's report on Operation Triangulation.
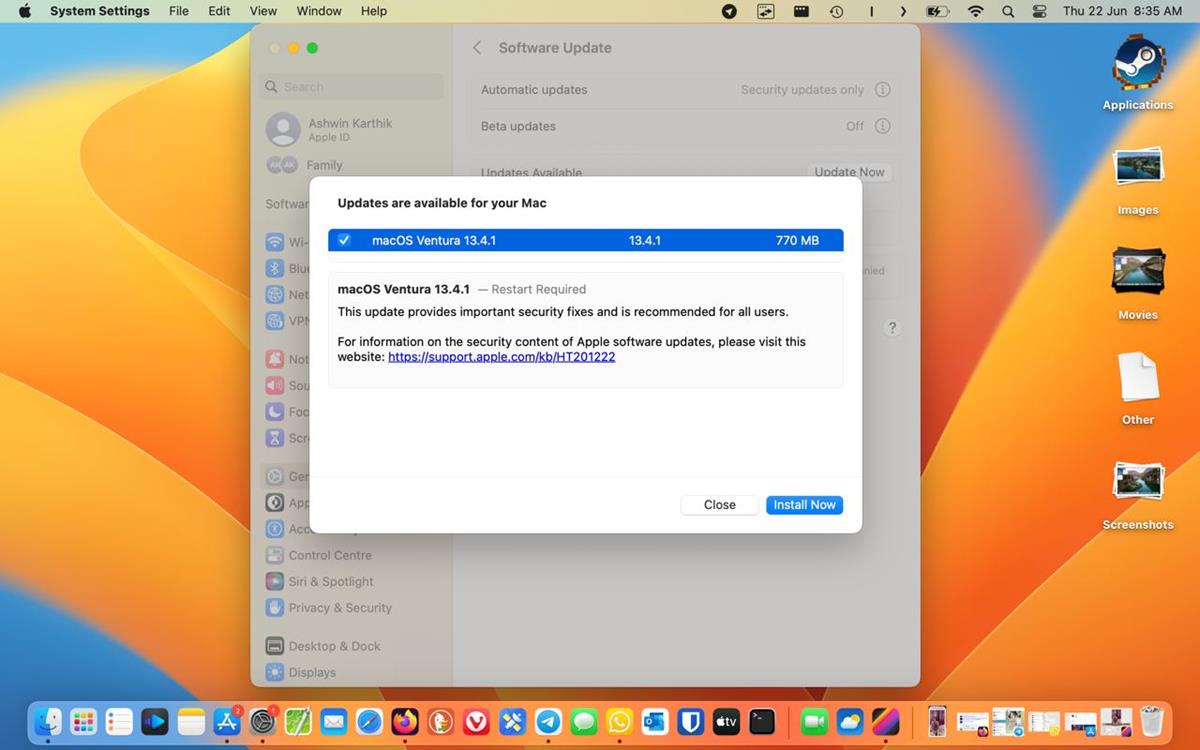
The other security issue is related to WebKit, the browser engine used by Safari and other apps. The bug tracked under CVE-2023-32439 was reported by an anonymous researcher. The release notes for the update indicate that the security issue could allow web pages with malware to execute arbitrary code, and that the type confusion issue was addressed with improved checks.
Apple has acknowledged that both issues may have been actively exploited in the wild. It is strange that Apple did not patch the security vulnerabilities via the Rapid Security Response system. It was designed for this very purpose, to quickly address bugs that may be exploited by hackers.
The above-mentioned fixes are included in macOS Ventura 13.4.1, iOS 16.5.1 (available for iPhone 8 and later), iPadOS 16.5.1 (iPad Pro (all models), iPad Air 3rd generation and later, iPad 5th generation and later, iPad mini 5th generation and later). The company says the kernel issue also impacted its Apple Watches, it has patched the vulnerability in watchOS 9.5.2 for the Apple Watch Series 4 and later, and watchOS 8.8.1 for the Apple Watch Series 3, Series 4, Series 5, Series 6, Series 7, and SE.
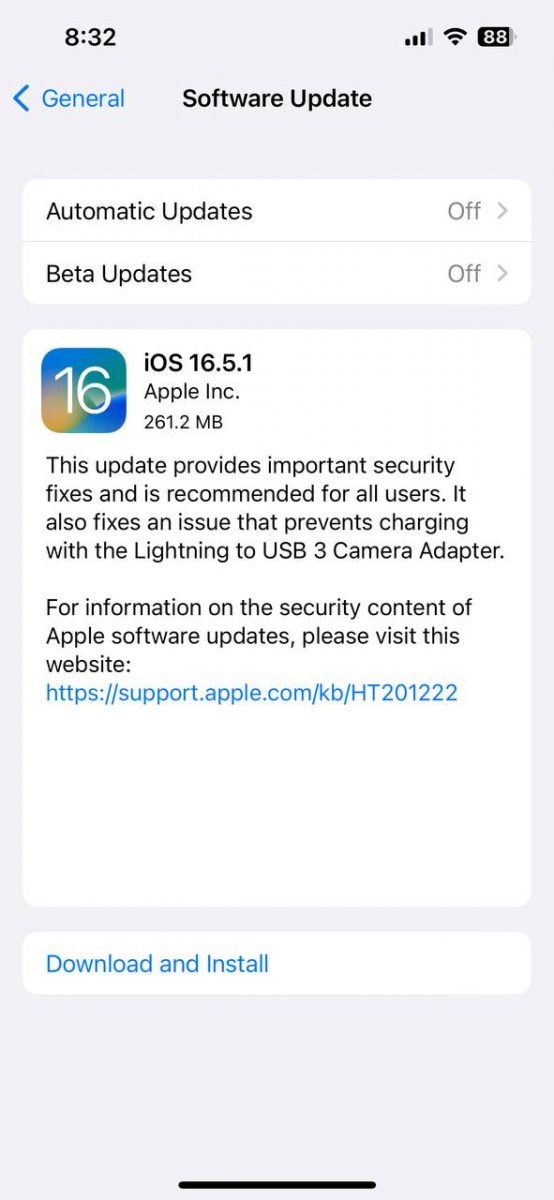
Remember the bug that prevented Apple's Lightning to USB 3 adapters from working in iOS 16.5? Apple has managed to fix the issue in iOS 16.5.1.
iOS 15.7.7, iPadOS 15.7.7, macOS Big Sur 11.7.8 and macOS Monterey 12.6.7 released
Apple has also released updates for older devices to address the above security issues. The new software update also ships with a third critical fix for another bug that the company says was also actively exploited by threat actors. This WebKit vulnerability is tracked as CVE-2023-32435, and was also discovered by the three experts from Kaspersky. Apple notes that the bug may allow processing web content to arbitrary code execution. The memory corruption issue was addressed with improved state management. The company has released the iOS 15.7.7 and iPadOS 15.7.7 updates for the following devices: iPhone 6s (all models), iPhone 7 (all models), iPhone SE (1st generation), iPad Air 2, iPad mini (4th generation), and iPod touch (7th generation).
The security fix for the kernel level issue mentioned earlier is also included in macOS Big Sur 11.7.8 and macOS Monterey 12.6.7, while the Safari 16.5.1 update ships with a patch for the other WebKit issue (CVE-2023-32439).



3175x175(CURRENT).thumb.jpg.b05acc060982b36f5891ba728e6d953c.jpg)
Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.