There is a 0-day vulnerability for Windows, called InstallerFileTakeOver, which Microsoft has yet to address. The vulnerability was discovered by Abdelhamid Naceri, a security researcher, who discovered two other 0-day vulnerabilities in Windows this year already.
We mentioned the vulnerability in late November 2021 already here on this site. The issue was unpatched back then and Microsoft has yet to release a security update that addresses the vulnerability.
Micro-patching company 0Patch released a free patch for the issue this week that is available to all users. The micropatch that 0Patch released is available for the following operating systems:
- Windows 10 version 1709 to 21H1.
- Windows 7 ESU
- Windows Server 2012, 2012 R2, 2016, 2019.
- Windows Server 2008 R2 ESU
0Patch notes that non-ESU Windows 7 and Windows Server 2012 installations are not affected by the vulnerability. Windows Server 2022 and Windows 11 are likely also affected, but not officially supported by the company yet (hence no patch). Windows 8.1 was not analyzed because of low interest in the particular version of Windows.
The vulnerability takes advantage of rollback files that Windows Installer creates during installation. It stores files that are deleted or modified during the installation process, to allow rollbacks. The rollback file is created in system directories and then moved to a temp folder in the user's directory.
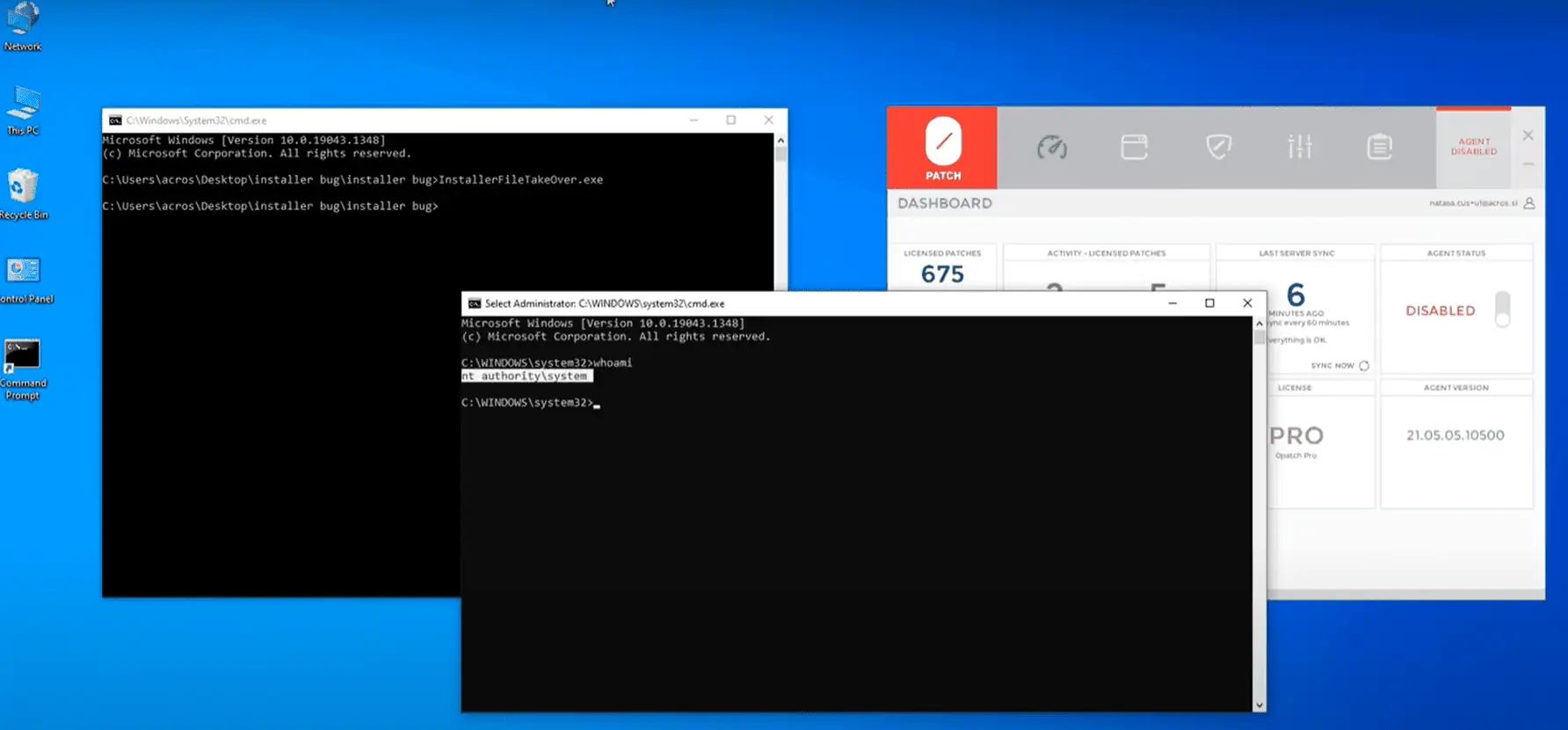
Naceri discovered that a symbolic link can be placed in the location, so that the RBF file is moved to another location. The symbolic link points to a file on the system that is then made accessible to the user, provided that Local System has write access to it.
Since Windows Installer is running as Local System, any file writable by Local System can be overwritten and made writable by the local user.
The micropatch that 0Patch has created checks if the destination for the rollback file operation contains junctions or links. The operation is blocked if that is the case, or allowed otherwise.
Patching systems with 0Patch micropatches requires a free account at 0Patch Central and the installation and registration of 0Patch Agent from the company. The patch is applied automatically, a reboot is not required.
Here is a demo video that 0Patch published on YouTube:
Here is the video of our micropatch in action. Without the micropatch, exploit works and a command line window is launched as Local System; with the micropatch, the code we correct in msi.dll determines that destination path contains a symbolic link, aborts the file move operation and triggers an "Exploit blocked" event.
Check out the 0Patch blog for additional details.
Now You: how do you handle unpatched vulnerabilities?
- Karlston
-

 1
1




Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.