Telegram fixed a zero-day vulnerability in its Windows desktop application that could be used to bypass security warnings and automatically launch Python scripts.
Over the past few days, rumors have been circulating on X and hacking forums about an alleged remote code execution vulnerability in Telegram for Windows.
While some of these posts claimed it was a zero-click flaw, the videos demonstrating the alleged security warning bypass and RCE vulnerability clearly show someone clicking on shared media to launch the Windows calculator.
Telegram quickly disputed these claims, stating that they "can't confirm that such a vulnerability exists" and that the video is likely a hoax.
However, the next day, a proof of concept exploit was shared on the XSS hacking forum explaining that a typo in the source code for Telegram for Windows could be exploited to send Python .pyzw files that bypass security warnings when clicked.
This caused the file to automatically be executed by Python without a warning from Telegram like it does for other executables, and was supposed to do for this file if it wasn't for a typo.
To make matters worse, the proof of concept exploit disguised the Python file as a shared video, along with a thumbnail, that could be used to trick users into clicking on the fake video to watch it.
In a statement to BleepingComputer, Telegram rightfully disputes that the bug was a zero-click flaw but confirmed they fixed the "issue" in Telegram for Windows to prevent Python scripts from automatically launching when clicked. This was a server-side fix, which we explain in the next section
"Rumors about the existence of zero-click vulnerabilities in Telegram Desktop are inaccurate. Some "experts" recommended to "disable automatic downloads" on Telegram — there were no issues which could have been triggered by automatic downloads.
However, on Telegram Desktop, there was an issue that required the user to CLICK on a malicious file while having the Python interpreter installed on their computer. Contrary to earlier reports, this was not a zero-click vulnerability and it could affect only a tiny fraction of our user base: less than 0.01% of our users have Python installed and use the relevant version of Telegram for Desktop.
A server-side fix has been applied to ensure that even this issue no longer reproduces, so all versions of Telegram Desktop (including all older ones) no longer have this issue."
❖ Telegram
BleepingComputer asked Telegram how they know what software is installed on user's Windows devices, as this type of data is not mentioned in their Privacy Policy.
The Telegram vulnerability
The Telegram Desktop client keeps track of a list of file extensions associated with risky files, such as executable files.
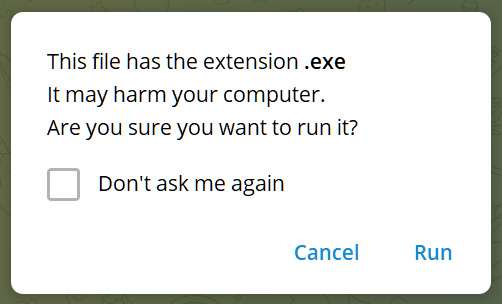
When someone sends one of these file types in Telegram, and a user clicks on the file, instead of automatically launching in the associated program in Windows, Telegram first displays the following security warning.
"This file has the extension .exe. It may harm your computer. Are you sure you want to run it?," reads the Telegram warning.
However, unknown file types shared in Telegram will automatically be launched in Windows, letting the operating system decide what program to use.
When Python for Windows is installed, it will associate the .pyzw file extension with the Python executable, causing Python to execute the scripts automatically when the file is double-clicked.
The .pyzw extension is for Python zipapps, which are self-contained Python programs contained within ZIP archives.
The Telegram developers were aware that these types of executables should be considered risky and added it to the list of executable file extensions.
Unfortunately, when they added the extension, they made a typo, entering the extension as 'pywz' rather than the correct spelling of 'pyzw'.
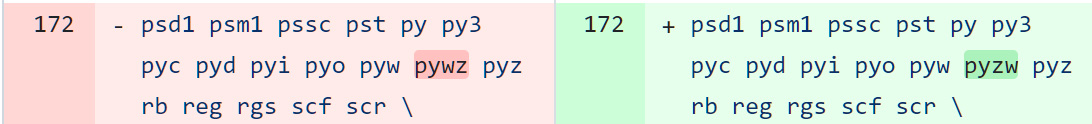
Therefore, when those files were sent over Telegram and clicked on, they were automatically launched by Python if it was installed in Windows.
This effectively allows attackers to bypass security warnings and remotely execute code on a target's Windows device if they can trick them into opening the file.
To masquerade the file, researchers devised using a Telegram bot to send the file with a mime type of 'video/mp4,' causing Telegram to display the file as a shared video.
If a user clicks on the video to watch it, the script will automatically be launched through Python for Windows.
BleepingComputer tested this exploit with cybersecurity researcher AabyssZG, who also shared demonstrations on X.
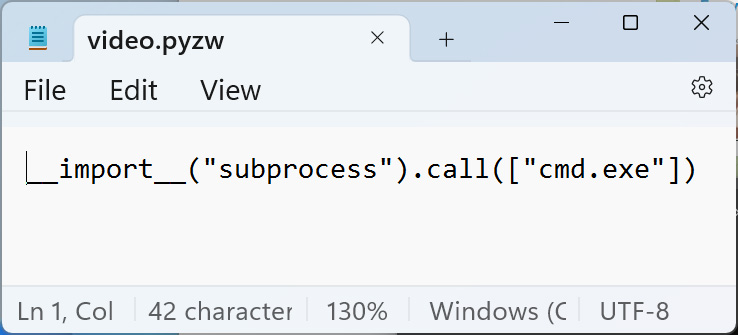
Using an older version of Telegram, BleepingComputer received 'video.pywz' file from the researcher disguised as a mp4 video. This file simply contains Python code to open a command prompt, as shown below.
However, as you can see below, when you click on the video to watch it, Python automatically executes the script, which opens the command prompt. Note that we redacted the video thumbnail as it's slightly NSFW.
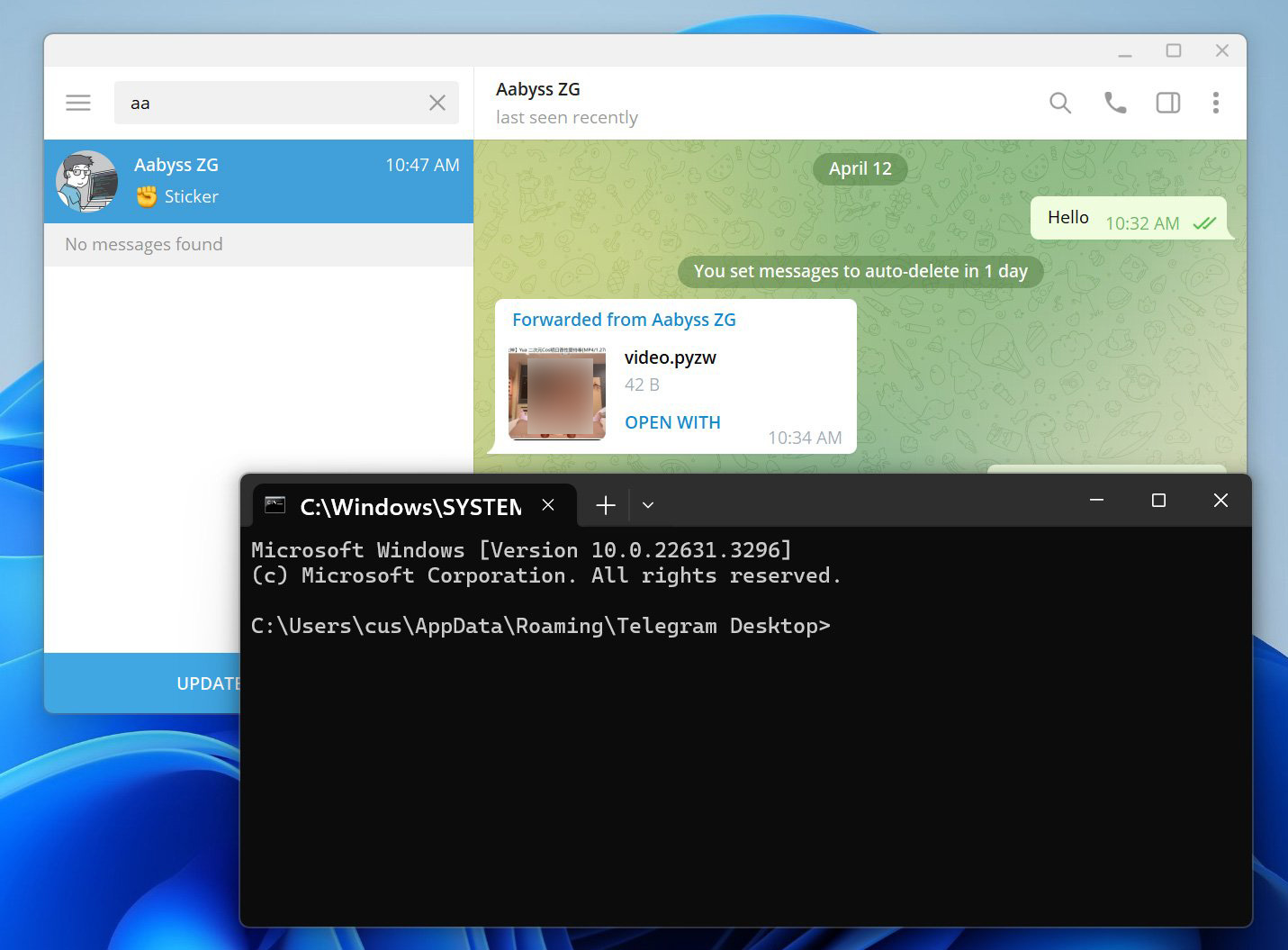
The bug was reported to Telegram on April 10th, and they fixed it by correcting the extension spelling in the 'data_document_resolver.cpp' source code file.
However, this fix does not appear to be live as of yet, as the warnings do not appear when you click on the file to launch it.
Instead, Telegram utilized a server-side fix that appends the .untrusted extension to pyzq files, that when clicked, will cause Windows to ask what program you wish to use to open it, rather than automatically launching in Python.
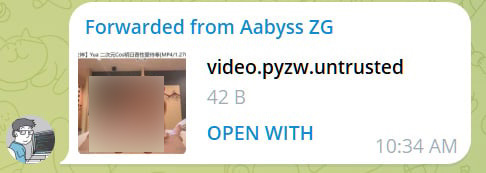
Future versions of the Telegram Desktop app should include the security warning message rather than appending the ".untrusted" extension, adding a bit more security to the process.



3175x175(CURRENT).thumb.jpg.b05acc060982b36f5891ba728e6d953c.jpg)
Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.