The first UEFI bootkit specifically targeting Linux systems has been discovered, marking a shift in stealthy and hard-to-remove bootkit threats that previously focused on Windows.
Named 'Bootkitty,' the Linux malware is a proof-of-concept that works only on some Ubuntu versions and configurations rather than a fully fledged threat deployed in actual attacks.
Bootkits are malware designed to infect a computer's boot process, loading before the operating system and allowing it to gain control over a system at a very low level.
The advantage of this practice is that bootkits can evade security tools running at the operating system level and modify system components or inject malicious code without risking detection.
ESET researchers who discovered Bootkitty warn that its existence is a significant evolution in the UEFI bootkit threats space despite the current real-world implications.
A Linux bootkit in the making
ESET discovered Bootkitty after examining a suspicious file (bootkit.efi) uploaded to VirusTotal in November 2024.
Upon analysis, ESET confirmed that this was the first case of a Linux UEFI bootkit to bypass kernel signature verification and preload malicious components during the system boot process.
Bootkitty relies on a self-signed certificate, so it won't execute on systems with Secure Boot enabled and only targets certain Ubuntu distributions.
Additionally, hardcoded offsets and simplistic byte-pattern matching make it only usable on specific GRUB and kernel versions, so it's unsuitable for widespread deployment.
ESET also notes that the malware contains many unused functions and handles kernel-version compatibility poorly, often leading to system crashes.
Source: ESET
The malware's buggy nature and the fact that ESET's telemetry shows no signs of Bootkitty on live systems led the researchers to conclude that it is in early-stage development.
Bootkitty's capabilities
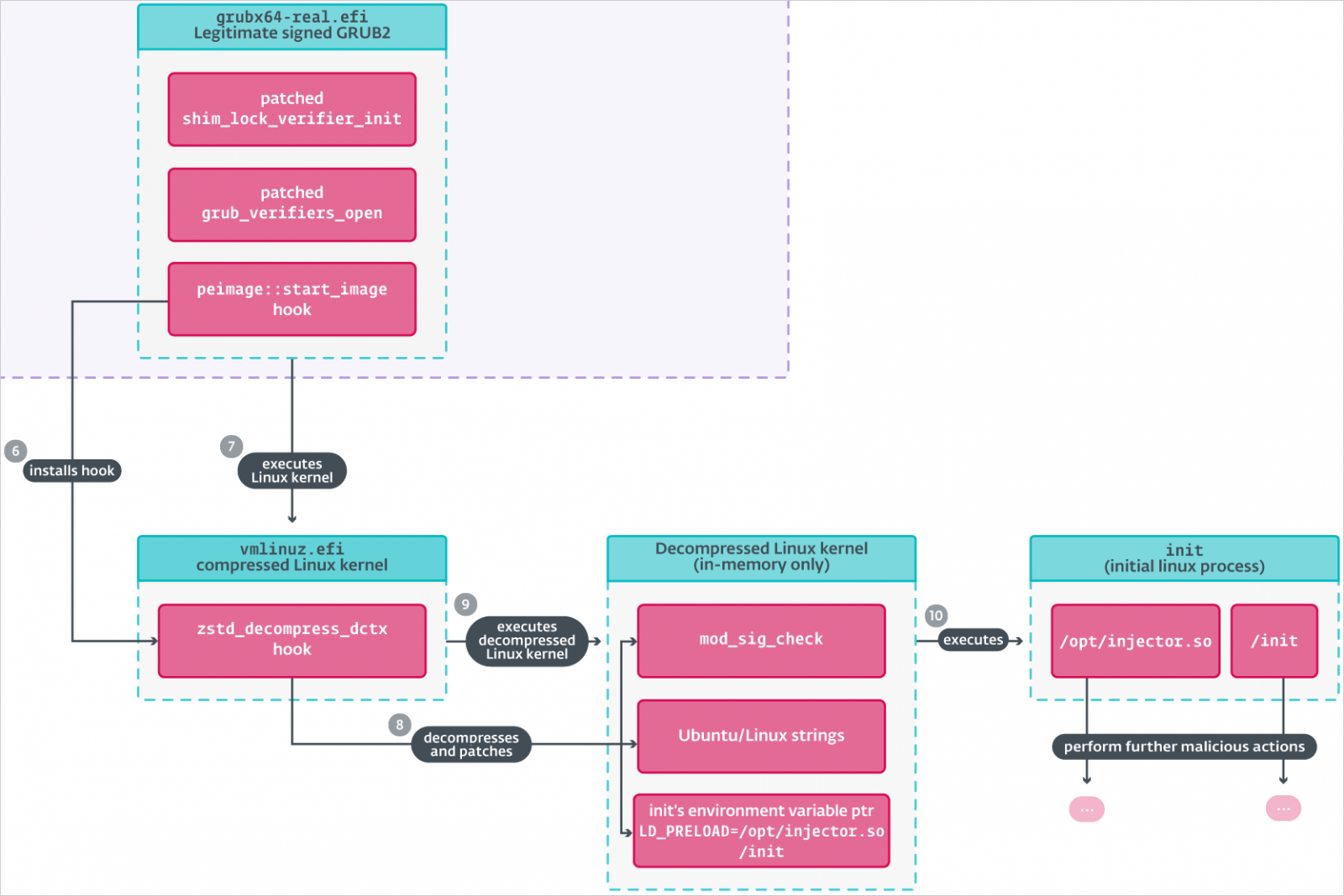
During boot, Bootkitty hooks UEFI security authentication protocols (EFI_SECURITY2_ARCH_PROTOCOL and EFI_SECURITY_ARCH_PROTOCOL) to bypass Secure Boot's integrity verification checks, ensuring the bootkit loads regardless of security policies.
Next, it hooks various GRUB functions like 'start_image' and 'grub_verifiers_open' to manipulate the bootloader's integrity checks for binaries, including the Linux kernel, turning off signature verification.
Bootkitty then intercepts the Linux kernel's decompression process and hooks the 'module_sig_check' function. This forces it to always return success during kernel module checks, allowing the malware to load malicious modules.
Also, it replaces the first environment variable with 'LD_PRELOAD=/opt/injector.so' so that the malicious library is injected into processes upon system launch.
Source: ESET
This whole process leaves behind several artifacts, some intended and others not, explains ESET, which is another indication of Bootkitty's lack of refinement.
The researchers also noted that the same user who uploaded Bootkitty onto VT also uploaded an unsigned kernel module named 'BCDropper,' but available evidence weakly links the two.
BCDropper drops an ELF file named 'BCObserver,' a kernel module with rootkit functionality that hides files, processes, and opens ports on the infected system.
The discovery of this type of malware illustrates how attackers are developing Linux malware that was previously isolated to Windows as the enterprise increasingly adopts Linux.
Indicators of compromise (IoCs) associated with Bootkitty have been shared on this GitHub repository.
Hope you enjoyed this news post.
Thank you for appreciating my time and effort posting news every day for many years.
2023: Over 5,800 news posts | 2024 (till end of October): 4,832 news posts
RIP Matrix | Farewell my friend ![]()
- phen0men4
-

 1
1


3175x175(CURRENT).thumb.jpg.b05acc060982b36f5891ba728e6d953c.jpg)
Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.