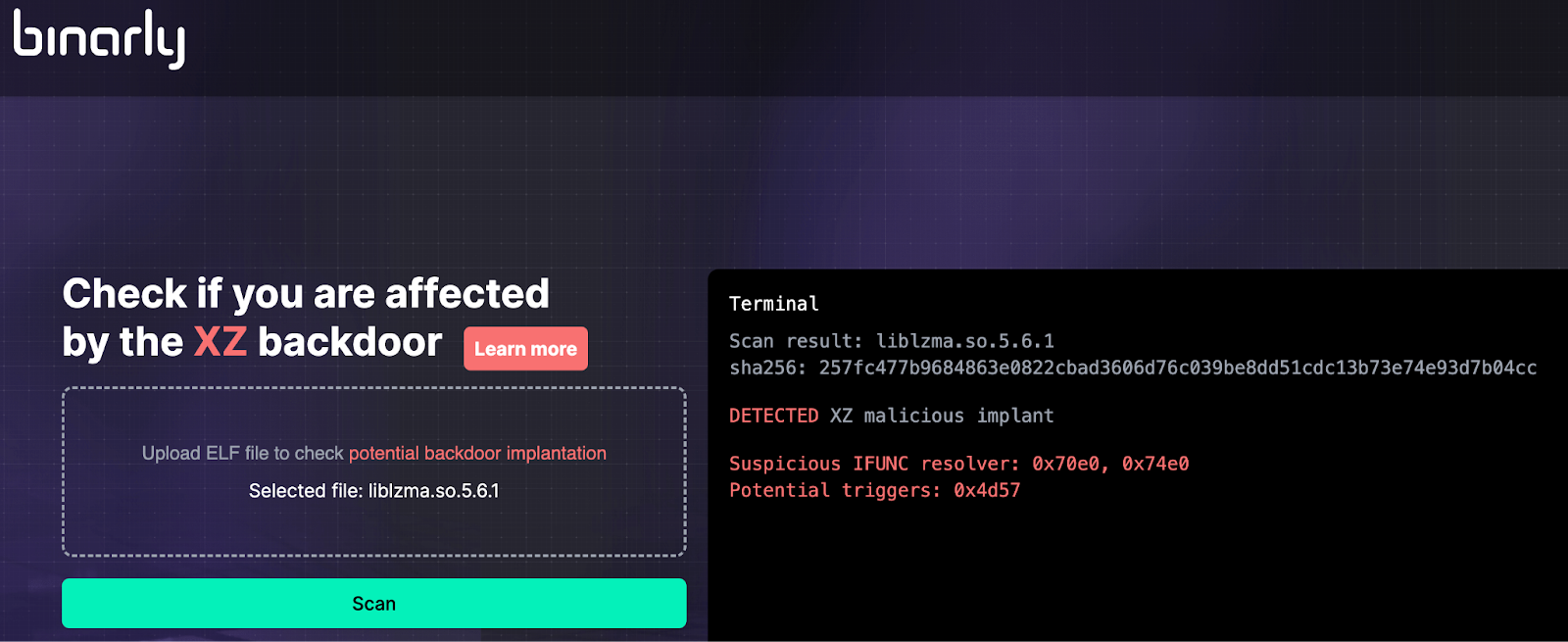
Firmware security firm Binarly has released a free online scanner to detect Linux executables impacted by the XZ Utils supply chain attack, tracked as CVE-2024-3094.
CVE-2024-3094 is a supply chain compromise in XZ Utils, a set of data compression tools and libraries used in many major Linux distributions.
Late last month, Microsoft engineer Andres Freud discovered the backdoor in the latest version of the XZ Utils package while investigating unusually slow SSH logins on Debian Sid, a rolling release of the Linux distribution.
The backdoor was introduced by a pseudonymous contributor to XZ version 5.6.0, which remained present in 5.6.1. However, only a few Linux distributions and versions following a "bleeding edge" upgrading approach were impacted, with most using an earlier, safe library version.
Following the discovery of the backdoor, a detection and remediation effort was started, with CISA proposing downgrading the XZ Utils 5.4.6 Stable and hunting for and reporting any malicious activity.
The XZ scanner
Binarly says the approach taken so far in the threat mitigation efforts relies on simple checks such as byte string matching, file hash blocklisting, and YARA rules, which could lead to false positives.
This approach can trigger significant alert fatigue and doesn't help detect similar backdoors on other projects.
To address this problem, Binarly developed a dedicated scanner that would work for the particular library and any file carrying the same backdoor.
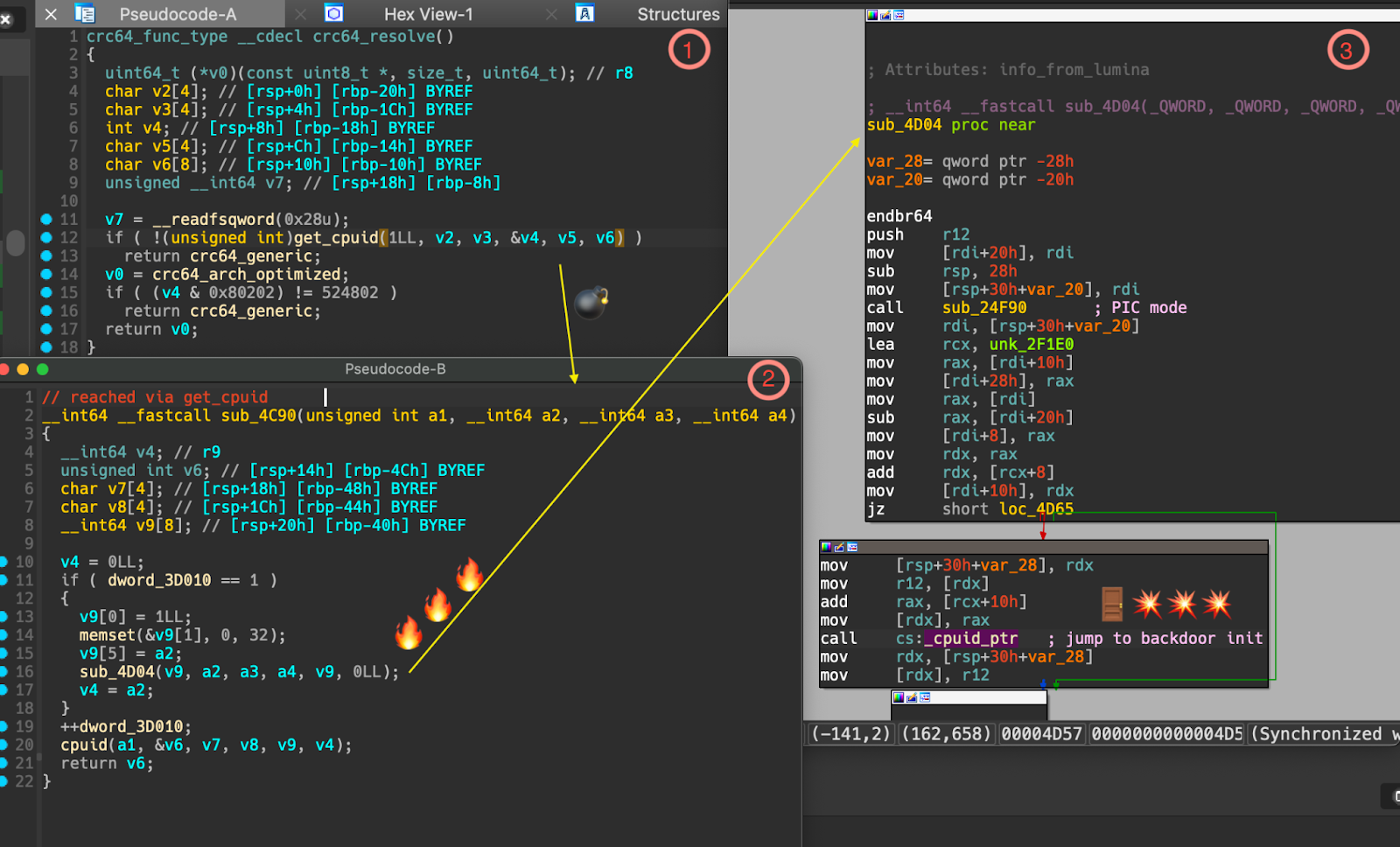
Binarly's detection method employs static analysis of binaries to identify tampering of transitions in GNU Indirect Function (IFUNC).
Specifically, the scanner examines the transitions marked as suspicious during the implantation of malicious IFUNC resolvers. The GCC compiler's IFUNC attribute allows developers to create multiple versions of the same function that are then selected at runtime based on various criteria, such as the processor type.
"One of the core techniques used by the XZ backdoor to gain initial control during execution is the GNU Indirect Function (ifunc) attribute for the GCC compiler to resolve indirect function calls in runtime," explains Binarly.
"The implanted backdoor code initially intercepts or hooks execution.
"It modifies ifunc calls to replace a check "is_arch_extension_supported" which should simply invoke "cpuid" to insert a call to "_get_cpuid" which is exported by the payload object file (i.e., liblzma_la-crc64-fast.o) and which calls malformed _get_cpuid() which is implanted into the code shown in the figure below."
The backdoor exploits this mechanism by modifying IFUNC calls to intercept or hook execution, resulting in the insertion of malicious code.
Binarly's scanner increases detection as it scans for various supply chain points beyond just the XZ Utils project, and the results are of much higher confidence.
"This detection is based on behavioral analysis and can detect any variants automatically if a similar backdoor is implanted somewhere else," Binarly's lead security researcher and CEO, Alex Matrosov, told BleepingComputer.
"Even after recompilation or code changes, we will detect it," Matrosov further told BleepingComputer.
The backdoor scanner is available online at xz.fail, where people can upload their binary files for unlimited free checks.
Update 4/2 - Binarly has made a free API available to accomodate bulk scans for those who need it.



3175x175(CURRENT).thumb.jpg.b05acc060982b36f5891ba728e6d953c.jpg)
Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.