Security researchers have released NoFilter, a tool that abuses the Windows Filtering Platform to elevate a user's privileges to increases privileges to SYSTEM, the highest permission level on Windows.
The utility is helpful in post-exploitation scenarios where an attacker needs to execute malicious code with higher permissions or to move laterally on a victim network as another user already logged into the infected device.
Access token duplication
Microsoft defines the Windows Filtering Platform (WFP) as “a set of API and system services that provide a platform for creating network filtering applications.”
Developers can use the WFP API to create code that can filter or modify network data before it reaches the destination, capabilities seen in network monitoring tools, intrusion detection systems, or firewalls.
Researchers at cybersecurity company Deep Instinct developed three new attacks to elevate privileges on a Windows machine without leaving too much evidence and without being detected by numerous security products.
The first method allows the use of WFP to duplicate access tokens, the pieces of code that identify users and their permissions in the security context of threads and processes.
When a thread executes a privileged task, security identifiers verify if the associated token has the required level of access.
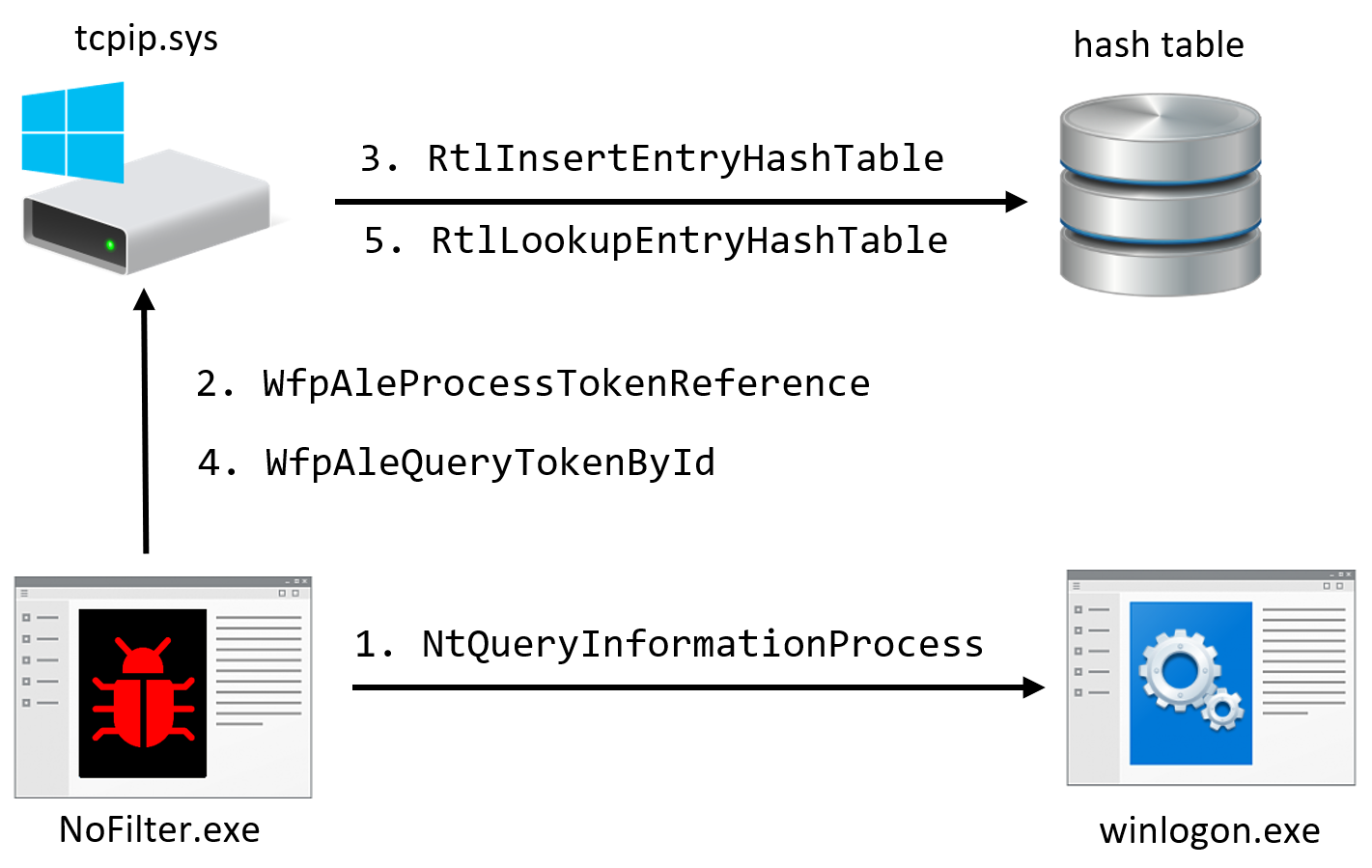
Ron Ben Yizhak, security researcher at Deep Instinct, explains that calling the NtQueryInformationProcess function allows getting the handle table with all the tokens a process holds.
“The handles to those tokens can be duplicated for another process to escalate to SYSTEM,” Yizhak notes in a technical blog post.
The researcher explains that an important driver in Windows operating system called tcpip.sys has several functions that could be invoked by device IO requests to WPF ALE (Application Layer Enforcement) kernel-mode layers for stateful filtering.
“Device IO request is sent to call WfpAleProcessTokenReference. It will attach to the address space of the service, duplicate the token of the service that belongs to SYSTEM, and will store it in the hash table” - Ron Ben Yizhak
The NoFilter tool abuses WPF in this way to duplicate a token and thus achieve privilege escalation.
By avoiding the call to DuplicateHandle, the researcher says, increases stealth and many endpoint detection and response solutions will likely miss the malicious action.
Getting SYSTEM and admin access token
A second technique involves triggering an IPSec connection and abusing the Print Spooler service to insert a SYSTEM token into the table.
Using the RpcOpenPrinter function retrieves -handle for a printer by name. By changing the name to “\\127.0.0.1,” the service connects to the local host.
Following the RPC call, multiple device IO requests to WfpAleQueryTokenById are necessary to retrieve a SYSTEM token.
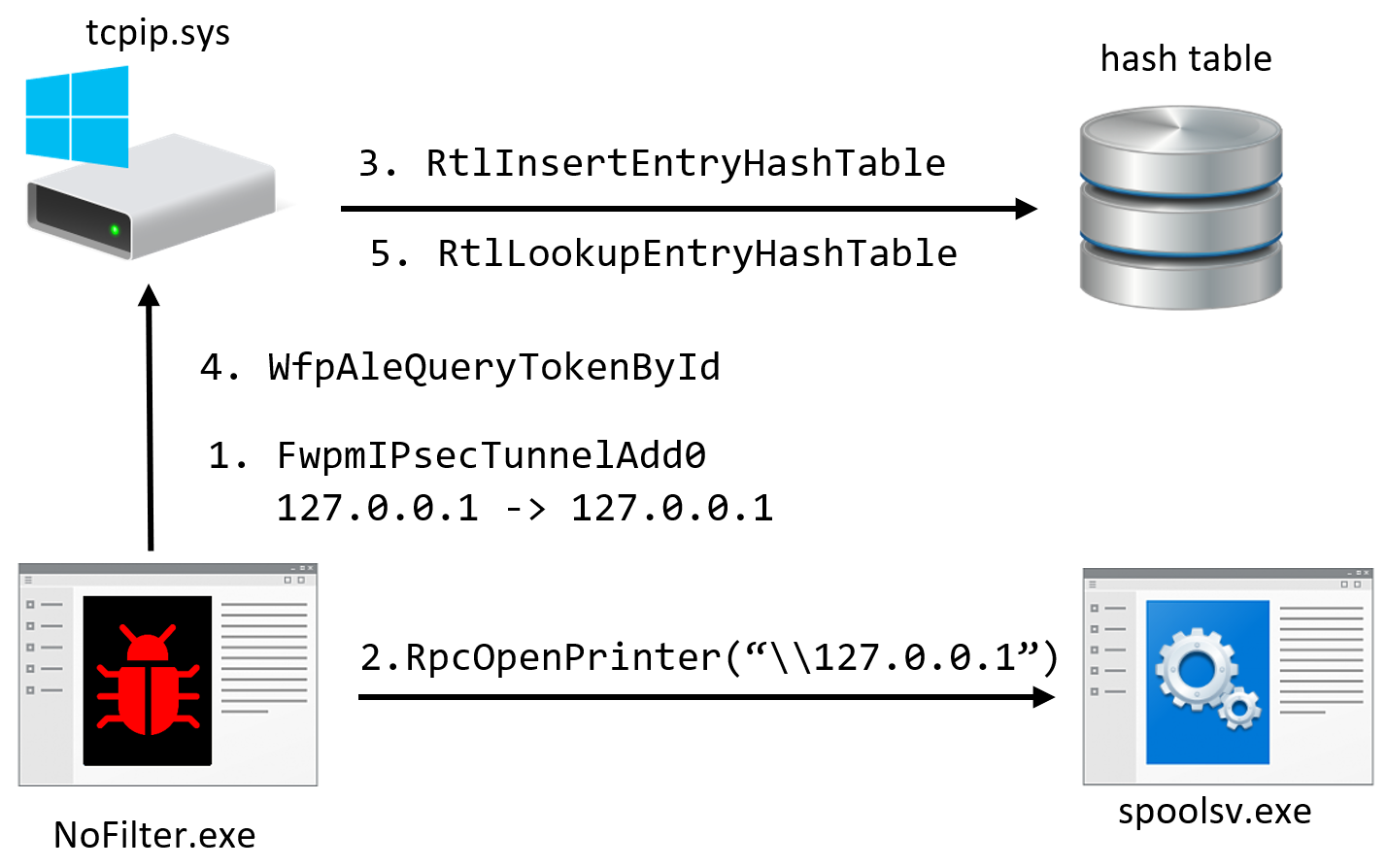
Yizhak says that this method is stealthier than the first one because configuring an IPSec policy is an action typically done by legitimate privileged users like network administrators.
“Also, the policy doesn’t alter the communication; no service should be affected by it and EDR solutions monitoring network activity will most likely ignore connections to the local host.”
A third technique described in Yizhak’s post allows obtaining the token of another user logged into the compromised system for lateral movement purposes.
The researcher says that it is possible to launch a process with the permissions of a logged-in user if the access token can be added to the hash table.
He looked for Remote Procedural Call (RPC) servers running as the logged-in user and ran a script to find processes that run as the domain admin and expose an RPC interface.
To obtain the token and launch an arbitrary process with the permissions of a logged user, the researcher abused the OneSyncSvc service and SyncController.dll, which are new components in the world of offensive tools.
Detection advice
Hackers and penetration testers are likely to adopt the three techniques since reporting them to Microsoft Security Response Center resulted in the company saying that the behavior was as intended. This typically means that there won’t be a fix or mitigation.
However, despite being stealthier than other methods, Deep Instinct provides a few ways to detect the three attacks and recommends looking for the following events:
- Configuring new IPSec policies that don’t match the known network configuration.
- RPC calls to Spooler / OneSyncSvc while an IPSec policy is active.
- Brute force the LUID of a token via multiple calls to WfpAleQueryTokenById.
- Device IO request to the device WfpAle by processes other than the BFE service.
Yizhak presented the three new techniques at the DEF CON hacker conference earlier this month. Complete technical details are available in Deep Instinct’s post.
- Ha91
-

 1
1



3175x175(CURRENT).thumb.jpg.b05acc060982b36f5891ba728e6d953c.jpg)
Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.