A new Linux vulnerability known as 'Dirty Pipe' allows local users to gain root privileges through publicly available exploits.
Today, security researcher Max Kellermann responsibly disclosed the 'Dirty Pipe' vulnerability and stated that it affects Linux Kernel 5.8 and later versions, even on Android devices.
The vulnerability is tracked as CVE-2022-0847 and allows a non-privileged user to inject and overwrite data in read-only files, including SUID processes that run as root.
Kellerman discovered the bug after tracking down a bug that was corrupting web server access logs for one of his customers.
Kellerman states that the vulnerability is similar to the Dirty COW vulnerability (CVE-2016-5195) fixed in 2016.
Public exploits give root privileges
As part of the Dirty Pipe disclosure, Kellerman released a proof-of-concept (PoC) exploit that allows local users to inject their own data into sensitive read-only files, removing restrictions or modifying configurations to provide greater access than they usually would have.
For example, security researcher Phith0n illustrated how they could use the exploit to modify the /etc/passwd file so that the root user does not have a password. Once this change is made, the non-privileged user could simply execute the 'su root' command to gain access to the root account.
However, an updated exploit by security researcher BLASTY was also publicly released today that makes it even easier to gain root privileges by patching the /usr/bin/su command to drop a root shell at /tmp/sh and then executing the script.
Once executed, the user gains root privileges, as demonstrated by BleepingComputer below in Ubuntu 20.04.3 LTS running the 5.13.0-27-generic kernel.
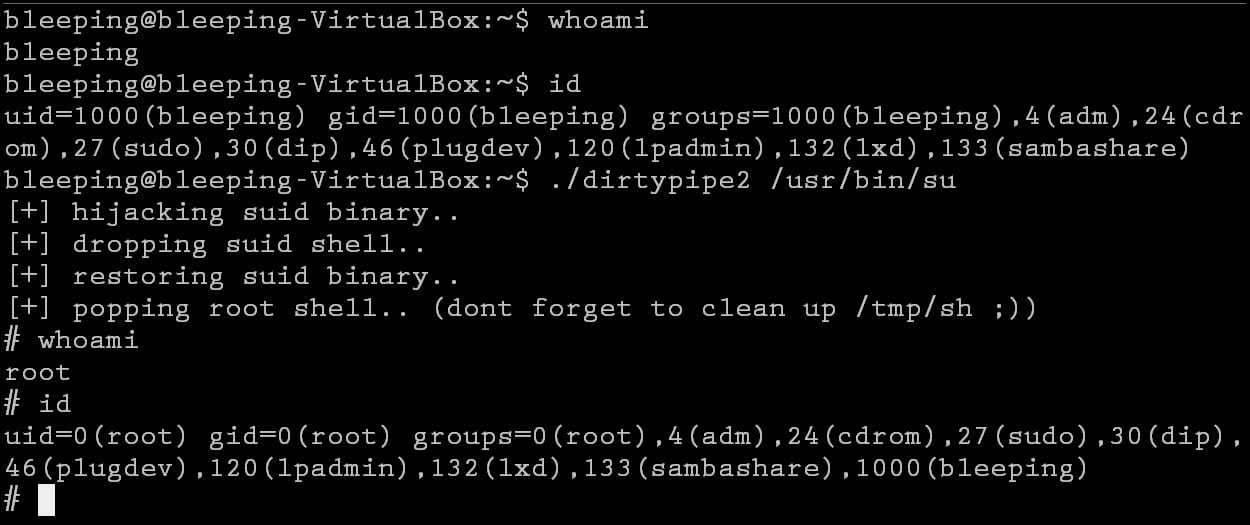
Source: BleepingComputer
The vulnerability was responsibly disclosed to various Linux maintainers starting on February 20th, 2022, including the Linux kernel security team and the Android Security Team.
While the bug has been fixed in Linux kernels 5.16.11, 5.15.25, and 5.10.102, many servers continue to run outdated kernels making the release of this exploit a significant issue to server administrators.
Furthermore, due to the ease of gaining root privileges using these exploits, it is only a matter of time before threat actors begin using the vulnerability when conducting attacks. The similar Dirty COW vulnerability was previously used by malware, even though it was harder to exploit.
This bug is especially concerning for web hosting providers who offer Linux shell access or universities that commonly provide shell access to multi-user Linux systems.
It has been a rough twelve months for Linux, with numerous high-profile privilege elevation vulnerabilities disclosed.
These include privilege elevation vulnerabilities in the Linux iSCSI subsystem, another kernel bug, the Extended Berkeley Packet Filter (eBPF), and Polkit's pkexec component.
New Linux bug gives root on all major distros, exploit released



3175x175(CURRENT).thumb.jpg.b05acc060982b36f5891ba728e6d953c.jpg)


Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.