Researchers have unearthed Linux malware that circulated in the wild for at least two years before being identified as a credential stealer that’s installed by the exploitation of recently patched vulnerabilities.
The newly identified malware is a Linux variant of NerbianRAT, a remote access Trojan first described in 2022 by researchers at security firm Proofpoint. Last Friday, Checkpoint Research revealed that the Linux version has existed since at least the same year, when it was uploaded to the VirusTotal malware identification site. Checkpoint went on to conclude that Magnet Goblin—the name the security firm uses to track the financially motivated threat actor using the malware—has installed it by exploiting “1-days,” which are recently patched vulnerabilities. Attackers in this scenario reverse engineer security updates, or copy associated proof-of-concept exploits, for use against devices that have yet to install the patches.
Checkpoint also identified MiniNerbian, a smaller version of NerbianRAT for Linux that’s used to backdoor servers running the Magento ecommerce server, primarily for use as command and control servers that devices infected by NerbianRAT connect to. Researchers elsewhere have reported encountering servers that appear to have been compromised with MiniNerbian, but Checkpoint Research appears to have been the first to identify the underlying binary.
“Magnet Goblin, whose campaigns appear to be financially motivated, has been quick to adopt 1-day vulnerabilities to deliver their custom Linux malware, NerbianRAT and MiniNerbian,” Checkpoint researchers wrote. “Those tools have operated under the radar as they mostly reside on edge-devices. This is part of an ongoing trend for threat actors to target areas which until now have been left unprotected.”
Checkpoint discovered the Linux malware while researching recent attacks that exploit critical vulnerabilities in Ivanti Secure Connect, which have been under mass exploitation since early January. In the past, Magnet Goblin has installed the malware by exploiting one-day vulnerabilities in Magento, Qlink Sense, and possibly Apache ActiveMQ.
In the course of its investigation into the Ivanti exploitation, Checkpoint found the Linux version of NerbianRAT on compromised servers that were under the control of Magnet Goblin. URLs included:
http://94.156.71[.]115/lxrt
http://91.92.240[.]113/aparche2
http://45.9.149[.]215/aparche2
The Linux variants connect back to the attacker-controlled IP 172.86.66[.]165.
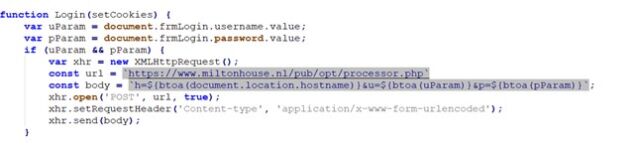
Besides deploying NerbianRAT, Magnet Goblin also installed a custom variant of malware tracked as WarpWire, a piece of stealer malware recently reported by security firm Mandiant. The variant Checkpoint encountered stole VPN credentials and sent them to a server at the domain miltonhouse[.]nl.
Checkpoint Research
NerbianRAT Windows featured robust code that took pains to hide itself and to prevent reverse engineering by rivals or researchers.
“Unlike its Windows equivalent, the Linux version barely has any protective measures,” Checkpoint said. “It is sloppily compiled with DWARF debugging information, which allows researchers to view, among other things, function names and global variable names.”
The report continued:
Upon its initial execution, the backdoor goes through a duplicate process check, which is carried out by allocating shared memory segments. If it succeeds, it forks itself, which is the only anti-debugging/anti-analysis trick embedded within the malware. Following this check, NerbianRAT begins the main initialization process.
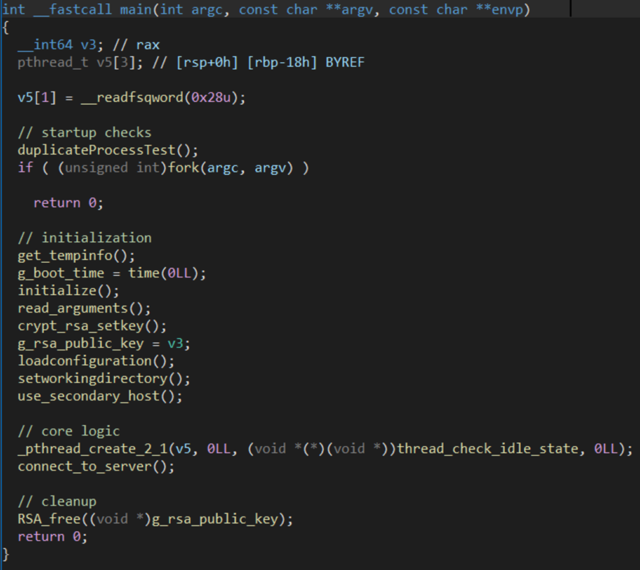
Figure 6 – NerbianRAT main function.
Checkpoint Research
Initialization
In its initialization, the malware follows several steps:
-
Collects basic information, including the current time, username, and machine name.
-
Generates a bot ID using a combination of the value of the file /etc/machine-id and the current process ID.
-
Loads a hardcoded IP address (172.86.66.165) into two global variables, the primary and secondary host.
-
Decrypts the global working directory variable and sets it as %TEMP%.
-
Searches for the file rgs_c.txt, reads its contents and tries to parse it as the following arguments: -pP port -h host
-
Loads a public RSA key that is later used to encrypt the network communication.
Configuration
Following its initialization, Nerbian continues to load its configuration from the file tmp/debconf.socket. It is encrypted in AES using a hard-coded key and 16 null bytes as the IV. The configuration itself contains a broad set of values, which demonstrates the threat actor’s efforts to customize the backdoor.
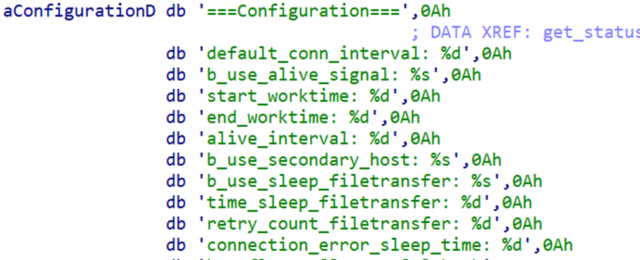
Figure 7 – NerbianRAT configuration variables.
Checkpoint Research
The NerbianRAT Linux variant configuration is similar to the Windows version. Much of the configuration is dedicated to the malware C2 mechanisms, determining the backdoors hours of activity, how often it reaches out to its C2 server, and similar functions. For example, the parameters start_worktime and end_worktime are used to determine the hours in which NerbianRAT attempts to connect to its C2 server.
After loading the config file, the working directory is enforced to /tmp/ and the global variable primary host is set based on the b_use_secondary_host config field type. It then proceeds to communicate with its C2.
Command and Control
Unlike the Windows variant, the Linux NerbianRAT utilizes raw TCP sockets, sending data blobs represented by structs back and forth in a custom protocol. This means that the C2 server logic is also rewritten so it can communicate with this version of the backdoor. AES encryption is used as the main encryption when communicating with the C2, although depending on the data transmitted, RSA can also be leveraged.
The bot runs in two possible states:
-
If the time is not during the working hours stated in the config, but the b_use_alive_signal field on the config is set, it continuously sends a ping to the C2 server containing the data collected earlier and some of the config fields.
-
If the time is during the working hours (calculated by converting the current time to UTC and then checking the hour field and comparing it to the config fields), it sends the C2 the same data mentioned above. If the server approves of that data, it sends a valid action for the backdoor to execute.
There are the conditions which must be met for the buffer received from the C2 server to be valid:
-
It should start with the magic 4r3f0 and then the AES encrypted buffer.
After decryption, the first 4 bytes of the buffer should contain the null-terminated string cmd.
If all of those conditions are met, the data is parsed and will result in one of the following actions:
|
Action ID
|
Action description
|
|
1
|
Continue requesting more actions.
|
|
4
|
Run a Linux command in a separate thread.
|
|
5
|
Send the last command result and clean up the result file. ** If a command is running it is stopped.
|
|
6
|
Run a Linux command immediately.
|
|
7
|
Do nothing / Idle command.
|
|
8
|
Change the connection interval global variable.
|
|
9
|
Update the start and end worktimes, then save the config file.
|
|
14
|
Send back the idle status timings string / the configuration / results of the last run Linux command.
|
|
15
|
Set a config variable, based on the name of the field and a value.
|
|
16
|
Update the gl_command_buffer global variable, used when executing commands from the C2.
|
Meanwhile, MiniNerbian is a simplified version of NerbianRAT that uses much of the same source code. At the same time, it’s a distinct piece of malware rather than a copy of NerbianRAT with certain parts excised.
“One of the main differences is the MiniNerbian communication method, which uses HTTP and passes data by sending POST requests to /dashboard/ endpoint. In contrast, NerbianRAT sends data over raw sockets,” Checkpoint said. MiniNerbian supports only three actions, as described in these functions:
-
system_cmd – A request command by the C2 is executed and returned to the server.
-
time_flag_change – The malware updates its internal time flag, with two possible returns to the C2 depending on the flag state:
-
Time flag has changed, Now it works for whole day..
-
Time flag has changed, Now it works only certain times everyday.... Similar to the Nerbian backdoor, this “mini” version also only is active at certain hours.
-
core_config_set – This allows the MiniNerbian backdoor config to be updated.
The report provides indicators of compromise that people can use to determine if they’ve been targeted in the campaign.




3175x175(CURRENT).thumb.jpg.b05acc060982b36f5891ba728e6d953c.jpg)



Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.