Multiple information stealers for the macOS platform have demonstrated the capability to evade detection even when security companies follow and report about new variants frequently.
A report by SentinelOne highlights the problem through three notable malware examples that can evade macOS's built-in anti-malware system, XProtect.
XProtect works in the background while scanning downloaded files and apps for known malware signatures.
Despite Apple constantly updating the tool's malware database, SentinelOne says info-stealers bypass it almost instantly thanks to the quick response of the malware authors.
Evading XProtect
The first example in SentinelOne's report is KeySteal, a malware first documented in 2021, which has evolved significantly since then.
Currently, it is distributed as an Xcode-built Mach-O binary, named 'UnixProject' or 'ChatGPT,' and attempts to establish persistence and steal Keychain information.
Keychain is macOS's native password management system serving as a secure storage for credentials, private keys, certificates, and notes.
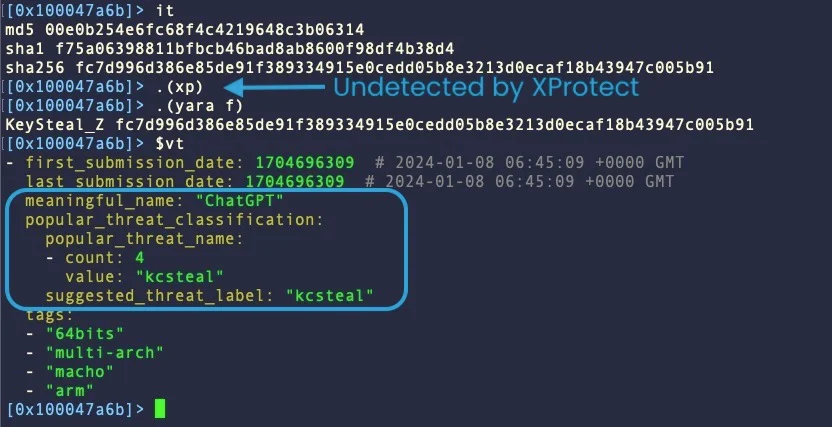
Apple last updated its signature for KeySteal in February 2023, but the malware has received enough changes since then to pass undetected by XProtect and most AV engines.
Its only current weakness is using hardcoded command and control (C2) addresses, but SentinelOne believes it's only a matter of time before KeySteal's creators implement a rotation mechanism.
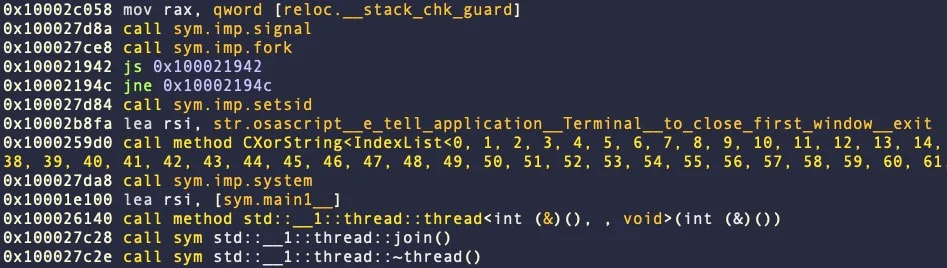
The next malware highlighted as an example of evasion is Atomic Stealer, first documented by SentinelOne in May 2023 as a new Go-based stealer and revisited by Malwarebytes in November 2023.
Apple last updated XProtect's signatures and detection rules this month, but SentinelOne reports already observing C++ variants that can evade detection.
The latest Atomic Stealer version has replaced code obfuscation with cleartext AppleScript that exposes its data-stealing logic, includes anti-VM checks, and prevents executing the Terminal alongside it.
The third example in the report is CherryPie, also known as 'Gary Stealer' or 'JaskaGo,' first seen in the wild on September 9, 2023.
The Go-based cross-platform malware features anti-analysis and virtual machine detection, Wails wrapping, ad hoc signatures, and a system that disables Gatekeeper using admin privileges.
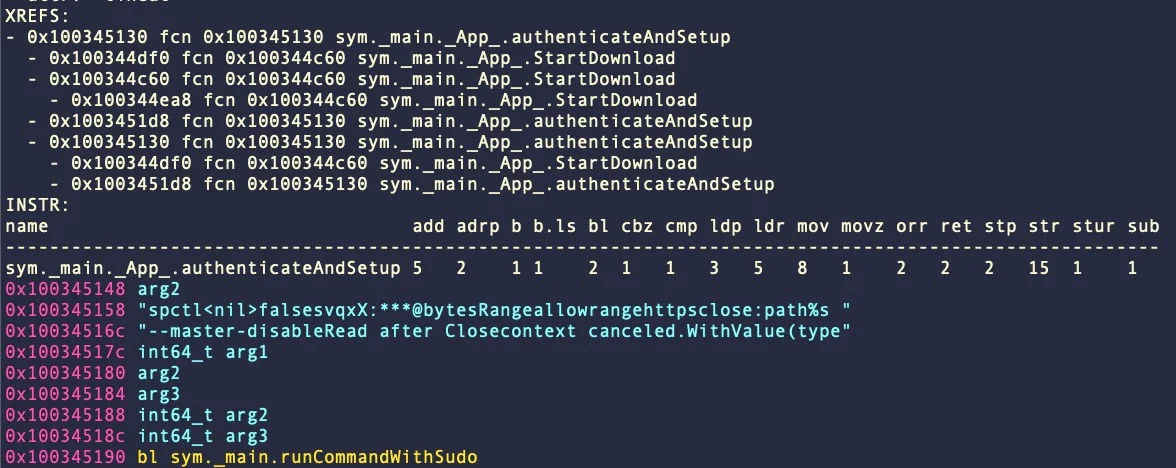
The good news is that Apple updated its XProtect signatures for CherryPie in early December 2023, which work really well even for newer iterations. However, malware detections do not fare as well on Virus Total.
It becomes clear from the above that the continual development of malware with the goal of evading detection makes this a risky game of whack-a-mole for users and operating system vendors alike.
Relying solely on static detection for security is inadequate and potentially risky. A more robust approach should incorporate antivirus software equipped with advanced dynamic or heuristic analysis capabilities.
Additionally, vigilant monitoring of network traffic, implementing firewalls, and consistently applying the latest security updates are essential components of a comprehensive cybersecurity strategy.



3175x175(CURRENT).thumb.jpg.b05acc060982b36f5891ba728e6d953c.jpg)
Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.