Kaspersky has released a new virus removal tool named KVRT for the Linux platform, allowing users to scan their systems and remove malware and other known threats for free.
The security firm notes that despite the common misconception that Linux systems are intrinsically secure from threats, there has been a constant supply of "in the wild" examples that prove otherwise, most recently, the XZ Utils backdoor.
Kaspersky's new tool isn't a real-time threat protection tool but a standalone scanner that can detect malware, adware, legitimate programs abused for malicious purposes, and other known threats and offers to clean them.
Copies of malicious files that are deleted or disinfected are stored in a quarantine directory at '/var/opt/KVRT2024_Data/Quarantine' (for root users) in a non-harmful form.
The application uses a frequently updated antivirus database to scan the entire system for matches, but users need to download a new copy each time for the latest definitions.
"Our application can scan system memory, startup objects, boot sectors, and all files in the operating system for known malware. It scans files of all formats — including archived ones," says Kaspersky.
One thing to note is that KVRT only supports 64-bit systems and requires an active internet connection to work.
Kaspersky has tested the tool on popular Linux distributions and confirmed it works on Red Hat Enterprise Linux, CentOS, Linux Mint, Ubuntu, SUSE, openSUSE, and Debian, among others.
Even if your distribution isn't on the list of supported systems, there's a good chance that KVRT will work without problems, so it wouldn't hurt to attempt to run a scan, Kaspersky says.
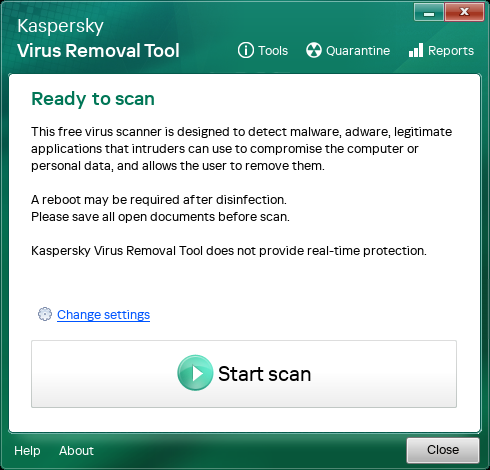
Using KVRT
KVRT can be downloaded from here, and once downloaded, the user needs to make the file executable and run it as root for maximum functionality.
KVRT can be executed both in a graphical user interface (GUI) or the terminal, as a command-line tool. So, it's also usable in lower init runlevels (down to 3) where people might be stuck following a malware infection.
If regular users execute the scanner, it won't have the required permissions to scan all directories and partitions where threats could be hiding.
During initialization, the scanner unpacks some necessary files into a temporary directory at '/tmp/<random_character_sequence,' but those are wiped once it's closed.
Kaspersky has provided detailed instructions on how to set up the binary for execution both via the GUI and the console on this webpage.
BleepingComputer has not tested the effectiveness, nor can it guarantee the safety of KVRT, so use the tool at your own risk.
Hope you enjoyed this news post.
Sincere thank you for your Feedback and Likes.
- aum
-

 1
1



3175x175(CURRENT).thumb.jpg.b05acc060982b36f5891ba728e6d953c.jpg)
Recommended Comments
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.