The latest generations of Intel processors, including Xeon chips, and AMD's older microarchitectures on Linux are vulnerable to new speculative execution attacks that bypass existing ‘Spectre’ mitigations.
The vulnerabilities impact Intel's 12th, 13th, and 14th chip generations for consumers and the 5th and 6th generation of Xeon processors for servers, along with AMD's Zen 1, Zen 1+, and Zen 2 processors.
The attacks undermine the Indirect Branch Predictor Barrier (IBPB) on x86 processors, a core defense mechanism against speculative execution attacks.
Speculative execution is a performance optimization feature on modern CPUs that executes instructions before knowing if they are needed by future tasks, thus speeding up the process when the prediction is correct. Instructions executed based on the misprediction are called transient and are squashed.
This mechanism has been a source of side-channel risks, such as Spectre, because the speculation process calls sensitive data that could be retrieved from the CPU cache.
New Spectre-like attacks
ETH Zurich researchers Johannes Wikner and Kaveh Razavi explain that despite the multi-year mitigation effort to contain Spectre-like attacks, there have been numerous variants that bypass existing defenses.
Their contribution is a cross-process attack (on Intel) and PB-inception attack (on AMD) that allows hijacking speculative return targets even after IBPB has been applied, thus bypassing current protections and leaking sensitive information.
In the first case, the attack exploits a flaw in Intel’s microcode where the IBPB doesn’t fully invalidate return predictions after a context switch.
The attacker manipulates the speculative execution of return instructions, allowing stale predictions to leak sensitive information, like the hash of the root password, from a suid process.
On AMD processors, IBPB-on-entry in the Linux kernel is improperly applied, allowing the return predictor to retain stale predictions even after IBPB.
The attacker mistrains the return predictor before IBPB is triggered, hijacking it to leak privileged kernel memory after the barrier.
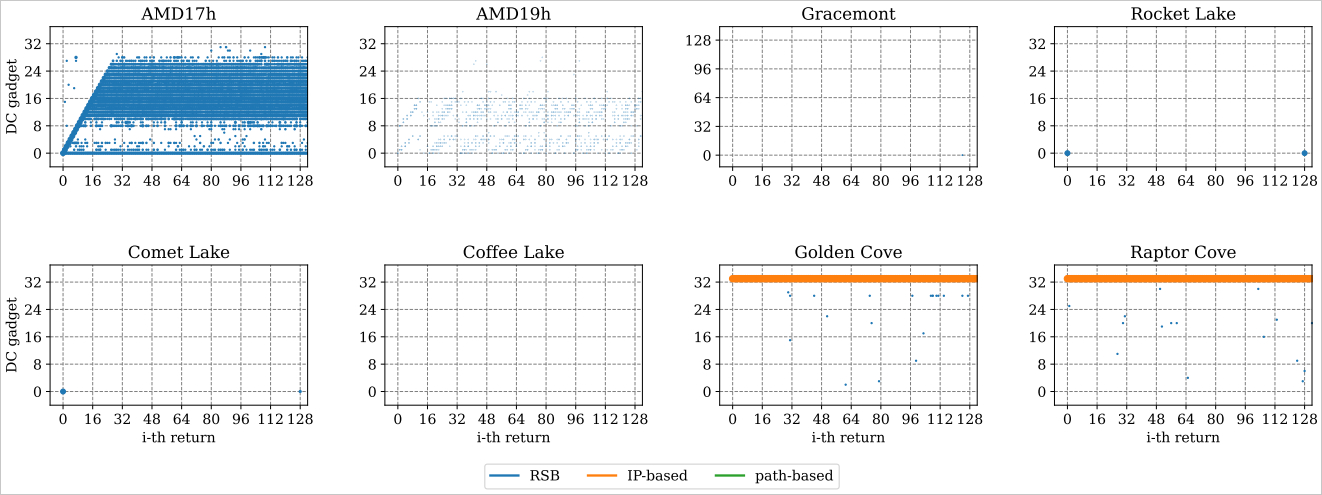
Source: ETH Zurich
Response and mitigations
The researchers informed both Intel and AMD of these issues in June 2024.
Intel responded saying that they had already discovered the issue internally and assigned it the CVE-2023-38575 identifier.
The company released in March a microcode fix available through a firmware update but the researchers note that the code has not reached all operating systems, Ubuntu being among them.
AMD also confirmed the vulnerability and said that the flaw had already been documented and tracked as CVE-2022-23824. It is worth noting that AMD’s advisory includes Zen 3 products as beeing affected, which are not listed in ETH Zurich’s paper.
However, AMD classifies the issue as a software bug, not a hardware flaw. The older architectures affected and the fact that AMD learned about the bug a long time ago may explain the company's decision not to issue corrective microcode.
Although the two CPU vendors knew about the Spectre bypass, the companies marked them in the advisories as having a potential impact. With their work, the ETH Zurich researchers were able to demonstrate that the attack works even on Linux 6.5, which comes with IBPB-on-entry defenses that are considered the strongest against Spctre exploitation.
The ETH Zurich team is working with Linux kernel maintainers to develop a patch for AMD processors, which will be available here when ready.
RIP Matrix | Farewell my friend ![]()
Hope you enjoyed this news post.
Thank you for appreciating my time and effort posting news every day for many years.
2023: Over 5,800 news posts | 2024 (till end of September): 4,292 news posts


3175x175(CURRENT).thumb.jpg.b05acc060982b36f5891ba728e6d953c.jpg)
Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.