ASUS has apologized to its customers for a server-side security maintenance error that has caused a wide range of impacted router models to lose network connectivity.
The problem has been extensively reported on social media and discussion platforms since May 16, 2023, with people appearing puzzled by the simultaneous connectivity issues on multiple ASUS routers and others complaining about the lack of communication from the vendor's side.
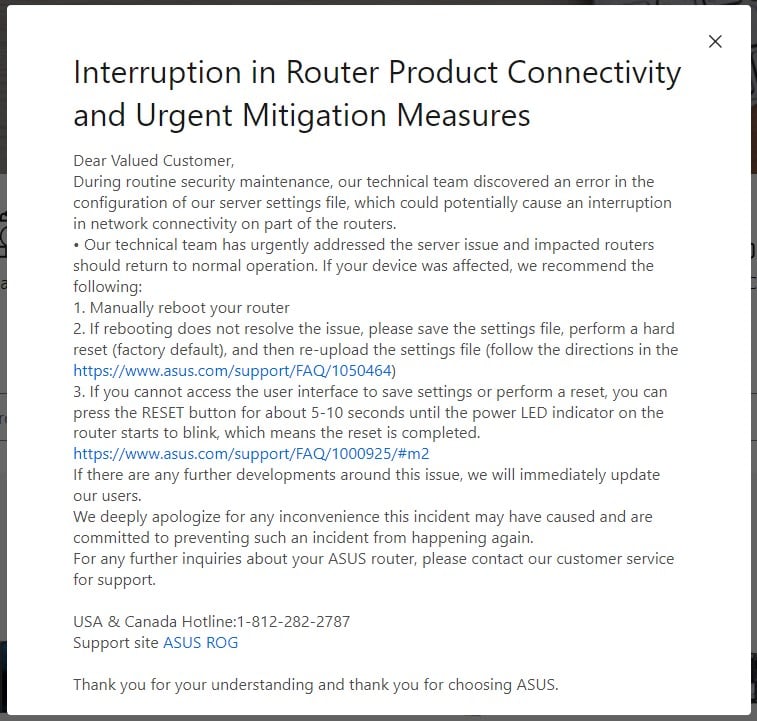
As the Taiwanese hardware maker explained in a statement published today and via a security bulletin, the problem was introduced by an error in the configuration of a server settings file.
"During routine security maintenance, our technical team discovered an error in the configuration of our server settings file, which could potentially cause an interruption in network connectivity on part of the routers," explains ASUS in a support bulletin.
While the company’s statement does not explicitly state what kind of error occurred and how exactly it impacted remote routers, a user on Reddit explained that the connectivity issues were caused by a corrupted definition file for ASD (ASUS AiProtection).
"Updating the firmware has pretty much universally fixed this, but so does simply resetting the router to factory defaults so long as it clears the NVRAM," explained the user on Reddit.
"In fact, any method that removes the offending file (/jffs/asd/chknvram20230516) will return the router to normal."
The ASD is a built-in security daemon supplied by Trend Micro, and it is used in a wide range of router models for real-time protection against emerging threats.
However, this component is updated regardless of whether the user has automatic security (firmware) updates enabled on their device or not.
Reportedly, the corrupted definition file for ASD was automatically pushed to all impacted routers, causing them to run out of filesystem space and memory and eventually crash.
Remediating the problem
ASUS says its technical team has addressed the server issue, so all impacted routers should return to normal operation now.
In some cases, though, users will have to manually reboot their devices to eliminate connectivity problems.
If that's still not enough, ASUS suggests performing a factory reset and re-uploading the settings file by following these step-by-step instructions.
For impacted users who cannot perform a reset, the vendor advises them to press and hold the RESET button on the device for 5-10 seconds until the power LED indicator starts blinking, which indicates a reset has been completed.
"We deeply apologize for any inconvenience this incident may have caused and are committed to preventing such an incident from happening again," concludes the vendor's statement.
Those who performed the recommended actions and still face problems are advised to contact ASUS support for additional help and guidance.
ASUS routers knocked offline worldwide by bad security update



3175x175(CURRENT).thumb.jpg.b05acc060982b36f5891ba728e6d953c.jpg)
Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.