By Susan Bradley (AKA 'The Microsoft Patch Lady')
I’ve been tracking some side effects that Microsoft has yet to acknowledge.
With Patch Tuesday just around the corner, it’s a good idea to put your favorite deferral solution in place. Some issues I’ve been following for several months are finally fixed in the August security updates, but we’re learning about this only through hints in preview releases.
Set your phasers on stun: I’m raising the MS-DEFCON level to 2.
Highlights
- Ensure that you have deferred updates using your preferred method.
- For business patchers, we’ve still not been given any guidance about how to deal with CVE-2023-32019. See below.
To defer updates, head to Settings | Update & Security | Windows Update | Advanced Options. Scroll down and choose the date through which you want to defer updates.
Most of the issues I’m tracking won’t be seen by consumers, only businesses. Many of them are in Windows 11 22H2. So even though I’ve approved 22H2 for everyone but gamers (my approval based primarily on the near impossibility of purchasing anything but 22H2), there are still some issues that businesses will find annoying. For the most part, these are described in Microsoft’s support post KB5028254 (OS Build 22621.2070) Preview. Here are two examples.
This update addresses an issue that affects certain display and audio devices. They are missing after your system resumes from sleep.
Sleep has been a slightly annoying issue with various versions of Windows, and 11 22H2 is no different. It appears that Microsoft is once again trying to quash the remaining bugs.
This update addresses an issue that affects virtual private networks (VPN). There might be excessive Address Resolution Protocol (ARP) requests to the network gateway. This occurs when the VPN is on a wireless mesh network that uses an aggressive throttling algorithm. Because of this, network performance is poor.
What’s interesting about this bug is that it specifically calls out MESH technology as causing a side effect unique to that platform. Note that I’m still hearing reports that users are seeing some issues with LT2P with IPSec. Again, bugs with that platform are still being quashed.
If you are like most consumer or home users, you don’t often look for or install firmware updates. But if your PC has an AMD processor, read on. A new vulnerability (CVE-2023-20593) impacting AMD’s line of Zen 2 processors — including the Ryzen 5 3600 — has been discovered that can be exploited to steal sensitive data such as passwords and encryption keys. AMD posted Cross-Process Information Leak, which provides details and an estimated timeline for firmware patch releases. The key thing to remember is that the attacker does not need physical access to exploit this bug — even JavaScript code on a website can potentially nail you.
Lately, I’ve seen several reports (including on my dad’s PC) about a search result from Google that led to a scam website pretending to be a Microsoft security notification (Figure 1). It isn’t.
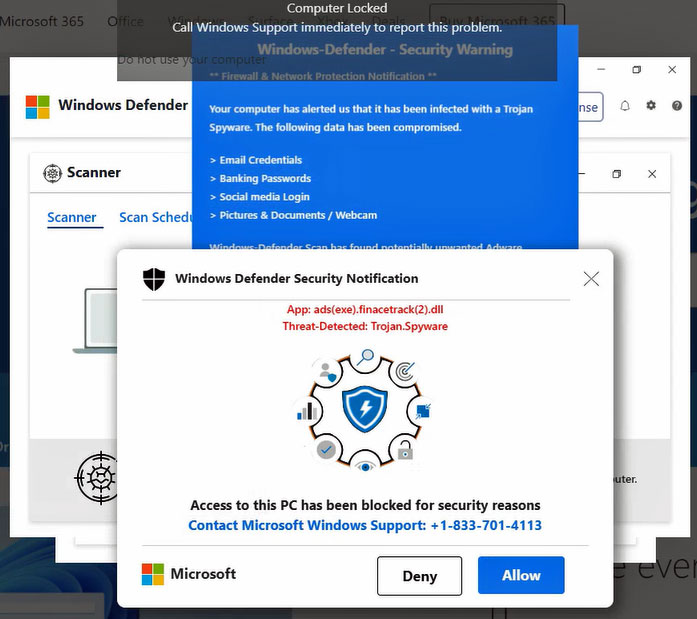
Figure 1. A fake Microsoft security alert, which is a scam. That’s not a Microsoft support number.
Let there be no doubt in your mind that the phone number on the screen is not a Microsoft number, and clicking any of those buttons would be a very bad thing. No matter how scary these alerts seem, just remember that it’s easy to “fix” the issue simply by closing the browser. But this is a showcase reminder that scam websites remain prevalent, with their only goal being trickery.
The key to remember is that although these look like Windows dialog boxes, they are not. They are simply images and buttons from a website. Always be ready to close a browser should you come across anything that resembles the image above.
We are now in August and still do not have a clue about when Microsoft will be enforcing CVE-2023-32019. Worse, I have no idea what side effects I might see once we’ve applied the registry fixes explained by Microsoft in KB5028407: How to manage the vulnerability associated with CVE-2023-32019. I find it inexcusable and disturbing that no details have been posted. Fortunately for us, it appears that there have been no active attacks and that the problem can be complex to trigger.
Update: Just after completing this alert, I became aware of further details. I created a post with additional information in the forums: CVE-2023-32019 – a bit more info from the researcher.
Be aware of the upcoming changes that may be impacting various Microsoft 365 settings. Some of them are introduced by patches, but others are enforcement changes coming to Microsoft 365. Remember: July brought Netlogon RPC entering the enforcement phase and Kerberos PAC changes beginning its Initial Enforcement. The second phase for Boot Manager revocation also began. For those of you still on Kaizala, be aware you should be migrating to Teams, as Kaizala is now end of life. More information can be found in a Microsoft Ticking Timebombs post at Reddit.
Resources
- Susan’s Master Patch List
- The MS-DEFCON System explained
- BlockAPatch – tools to help you hide or block updates
- Steve Gibson’s excellent InControl to manage feature releases



3175x175(CURRENT).thumb.jpg.b05acc060982b36f5891ba728e6d953c.jpg)
Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.