With the recent security breaches involving LastPass and Norton Password Manager, it's understandable that people are wary about keeping their passwords in the cloud. That's why there's been a rise in the popularity of password management solutions that store passwords locally, like KeePass, which is free and open-source.
However, there's a potential flaw in KeePass that's recently been uncovered, which could allow an attacker to get their hands on all your locally stored passwords using a basic tool like Notepad. Although the creator of KeePass hasn't commented directly on this issue, it's still a concern for those who place a high value on the security of their password information.
How KeePass works
KeePass is highly customizable, surpassing all other password managers. The customization is done through a system of triggers, conditions, and actions. Triggers can be simple events like launching the program, opening a database, or shutting down the program, or more advanced events like time-based triggers or custom button triggers. Triggers can also be set to activate only when specific conditions are met, such as the presence of a particular file or the availability of a remote host.
The majority of actions in KeePass relate to internal operations like importing/exporting the password database or syncing it with a backup file. But triggers can also execute command lines or launch URLs, which is highly desirable for hackers. The KeePass website provides examples of useful triggers, such as backing up the database, exporting it to a secondary format, and syncing it with cloud storage.
How to abuse the trigger system
In January 2023, security expert Alex Hernandez revealed a potential attack on KeePass, where the trigger system could be abused to extract a plain text version of all passwords stored in the database. The National Institute of Standards and Technology took the report seriously and added it to their vulnerability database under the identifier CVE-2023-24055. However, KeePass disputes these findings.
Hernandez shared the code for this attack on Github, which can be reviewed by those with technical knowledge. In short, the attack involves editing the KeePass configuration file to create an action that triggers when the database is saved. This causes KeePass to export the password database to a plain text file without requiring the master password. Another trigger then uploads this exported file to a server waiting to receive it. All that is required to carry out this attack is the ability to edit the KeePass configuration file, which can be done either by accessing an unlocked computer and using a text editor or by using a remote access Trojan to do it remotely.
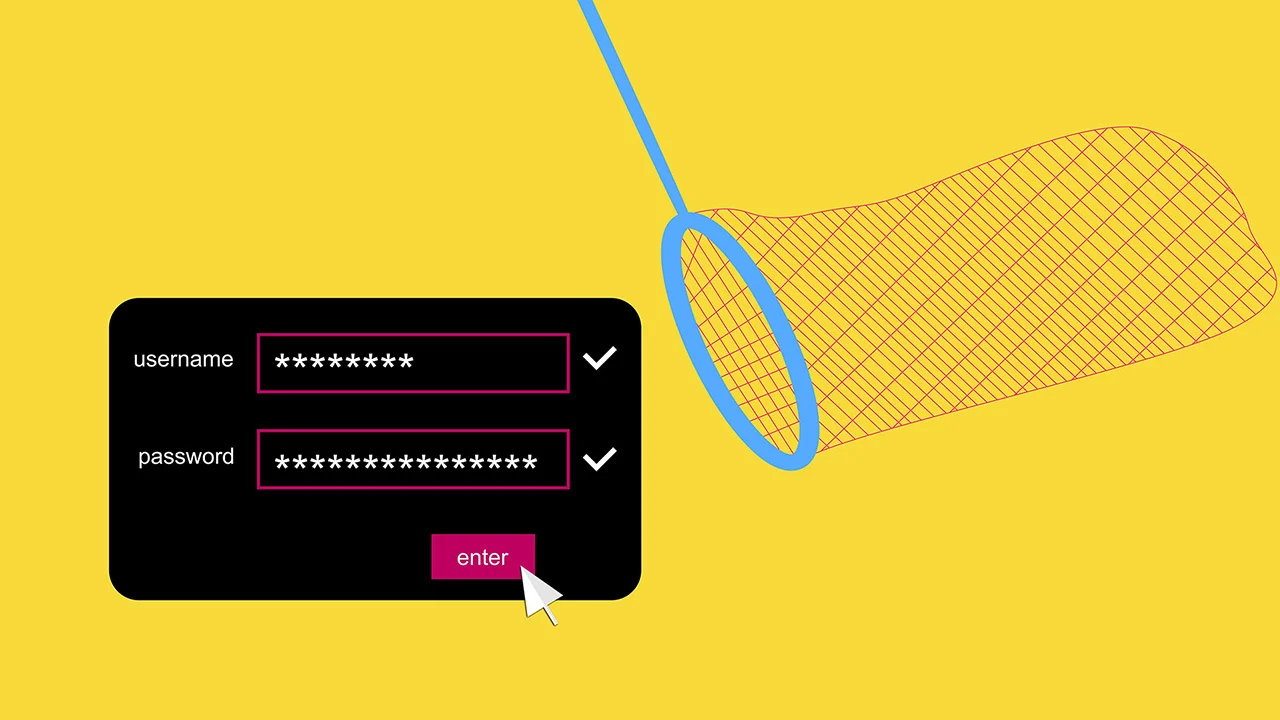
Security devs should assume that a system is compromised
Despite the report from Hernandez about a potential attack on KeePass, the creator and founder of KeePass, Dominik Reichl, brushed off the supposed vulnerability. He argued that anyone with enough privilege to edit the configuration file can cause even more damage and dismissed the need for a change in KeePass. He stated that KeePass cannot guarantee security in an insecure environment.
However, in today's security landscape, the idea is to assume that the system is already compromised and find ways to maintain security. This approach, known as Zero Trust, is central to many modern security practices, including cloud-based password managers that authenticate users without actually knowing their passwords.
Trusting KeePass means trusting third-party plug-ins
Local-only storage has been a popular feature of KeePass, but it comes with some trade-offs. While it's great that KeePass stores your passwords solely on your PC, manual syncing with another installation can be tedious. However, KeePass does have plug-ins that make syncing easier, but using them means trusting a third party to handle your data securely. This puts your passwords at risk, just like with cloud-based password managers. Although basic cloud storage services have security features, they're not as robust as dedicated password storage in the cloud.
Keep in mind, local storage doesn't mean you can't sync securely. For example, the now-defunct MyKi used to store passwords on mobile devices and sync them through relay servers without storing them on the servers. Unfortunately, MyKi shut down after being acquired by JumpCloud. To sum it up, KeePass does offer local storage, but if you want easy syncing, you're exposing yourself to more security risks.

Should you still trust KeePass?
So nothing really happened in January with KeePass. There was no attack or data breach. The researcher just pointed out an existing vulnerability that has been around for years. The cool customization options in KeePass that people love can also make it vulnerable if not used carefully.
If you still want to use KeePass, be sure to take some precautions, like keeping good antivirus software and a strong password for your Windows account. If you need to step away from your desk, lock your computer to protect your passwords. However, if you want to sync your passwords automatically, you'll have to trust the author of the sync plugin and rely on the security of your cloud storage provider. This means your passwords could be exposed if either the plugin or the cloud storage provider is not secure.




Recommended Comments
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.