Mozilla has just released a security update for its Firefox web browser that patches a critical security issue in all supported versions of the web browser.
The update is available for Firefox and Firefox ESR for desktop operating system, for Firefox Focus and for Firefox for Android.
The desktop version of Firefox is updated to version 118.0.1 to address the issue. Firefox ESR is updated to 115.3..1, and the two Android-based browsers are updated to version 118.1.0.
The security issue is the same that Google addressed in Chromium and Google Chrome yesterday.
CVE-2023-5217: Heap buffer overflow in libvpx, is a critical security issue in libvpx. Libvpx is a software video codec library developed by Google and the Alliance for Open Media. The free tool is open source and widely used in web browsers.
Mozilla notes on the security advisory website: "Specific handling of an attacker-controlled VP8 media stream could lead to a heap buffer overflow in the content process. We are aware of this issue being exploited in other products in the wild."
The issue is actively exploited in the wild, but it is unclear how widespread the attacks are. Mozilla reveals that the attack needs access to a VP8 media stream to be carried out.
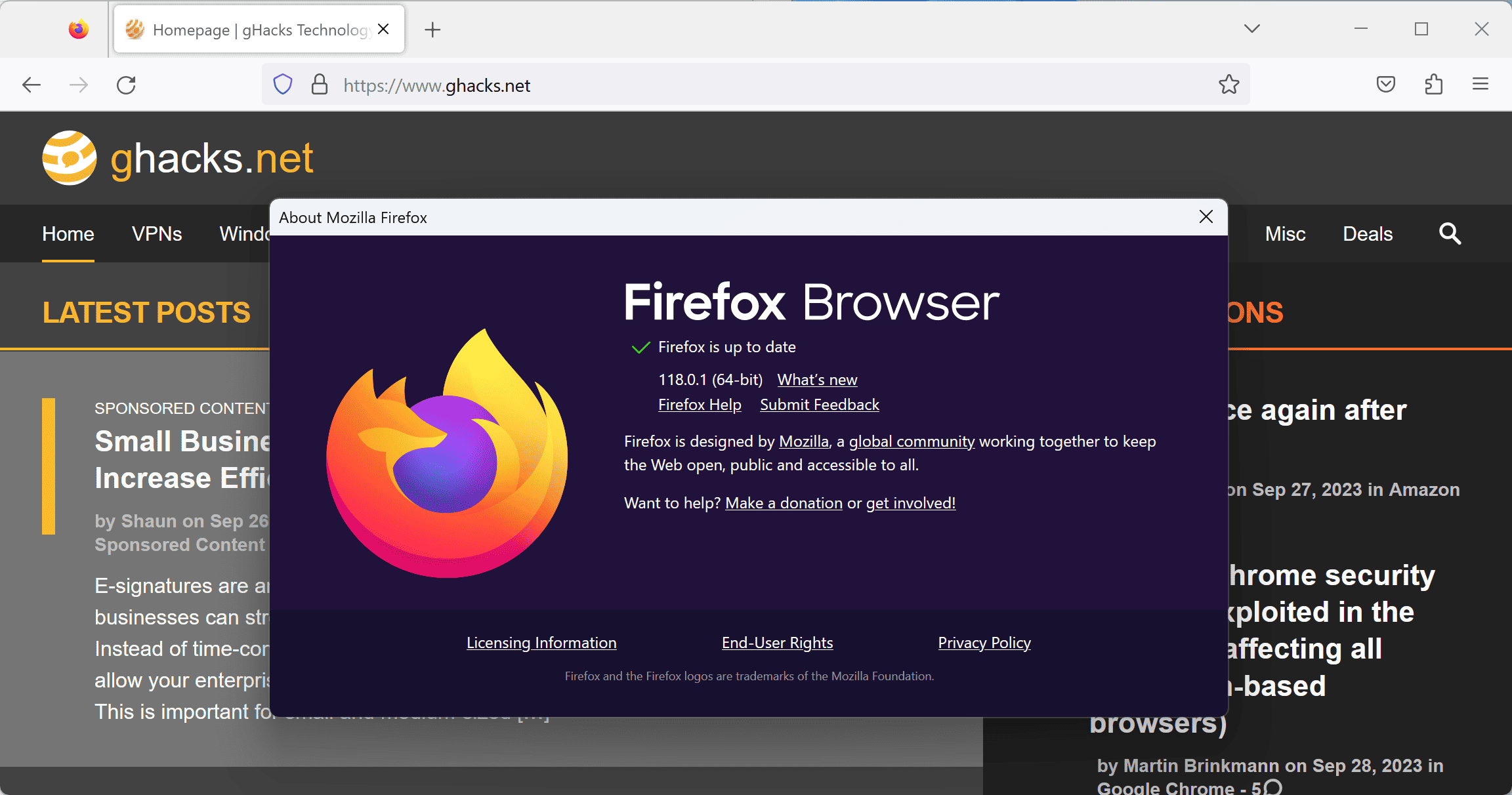
Firefox users should update their browser immediately to protect it from attacks. Desktop users may select Menu > Help > About Firefox to do so.
The popup that opens displays the installed version. Firefox runs an automatic check for updates whenever the popup is opened; it should pick up the new version to download and install it. A restart of the web browser is required to complete the installation. Another check of the "About" popup should display the new version and reassure users that their browser is no longer vulnerable to the attack.
Android users need to wait until the new version is pushed to their devices via Google Play.
- aum
-

 1
1



3175x175(CURRENT).thumb.jpg.b05acc060982b36f5891ba728e6d953c.jpg)
Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.