After fierce blowback, Microsoft has outlined new fixes to Recall's security, but questions remain about whether people will opt to use it.
What you need to know
- Microsoft has detailed how it's improved Recall's security with encryption and Windows Hello authentication.
- Recall's data is now isolated in a VBS Enclave, meaning it's no longer readable by third-party apps and users.
- Snapshots will now automatically filter out sensitive information like passwords and credit card details.
- Recall never uploads data to the cloud, and can be uninstalled from the system if you don't want it.
Microsoft is finally ready to detail how it’s updating Windows Recall to ensure it’s a secure experience that can’t be easily hacked or tampered with. After the monumental failure that was Recall's original debut, the company is now confident that Recall is a safe experience that users should feel comfortable using.
Originally, Windows Recall was discovered to be storing data in an unencrypted state, making it ripe for third-party attackers to scrape sensitive information collected by the Recall process. Microsoft has now addressed this concern, moving to encrypting the data and ensuring the user is actively present to access it.
The company has published a detailed article detailing all the security improvements it’s making to Windows Recall, but it boils down to four key changes:
- Recall data is now stored in an encrypted state in isolation via a VBS Enclave
- Snapshots will now automatically filter out passwords, credit cards, and national IDs
- Access to Recall data requires Windows Hello authentication every time
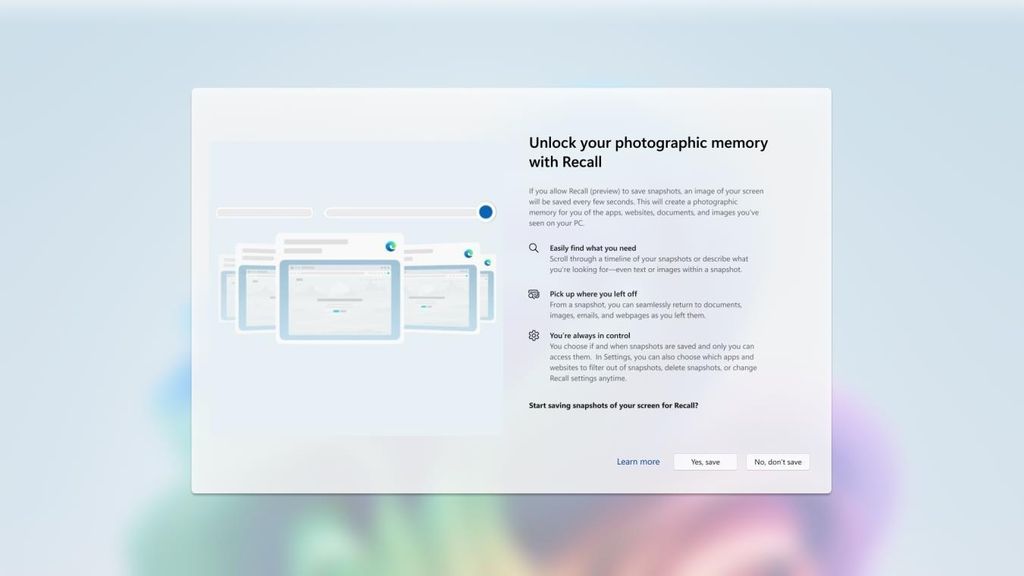
- Recall is optional, off by default, and can be uninstalled
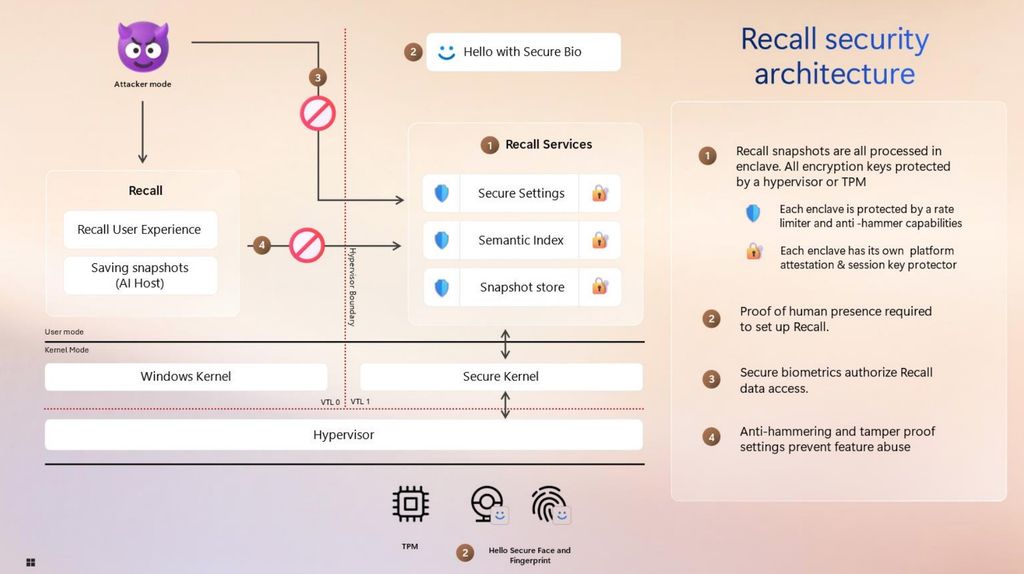
An attacker is unable to infiltrate Recall's services that handle snapshots and data.
(Image credit: Microsoft)
Recall is still Copilot+ PC exclusive and requires an NPU that can output at least 40 TOPS of power. This means most PCs won't even be eligible to use Recall. For the PCs that are, Microsoft has addressed the biggest concerns people had with Recall, including how it stores data locally on your device.
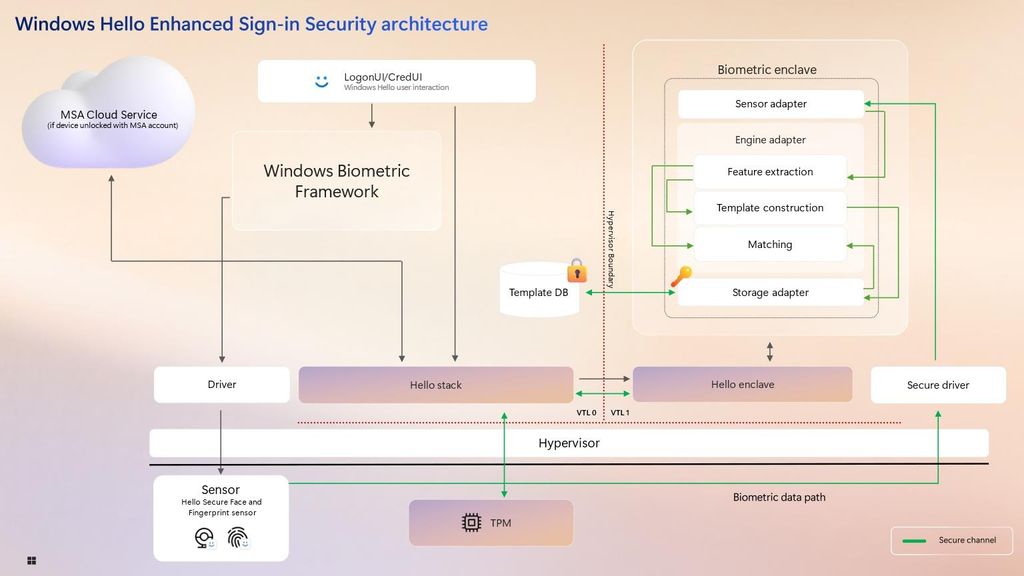
Now, any data that Recall collects is stored in an encrypted VBS Enclave, which is essentially a secure virtual machine that is isolated from the rest of the system, meaning the data stored inside it is inaccessible without a decryption key, which the Recall app provides when the user authenticates with Windows Hello.
"Anything sensitive is always encrypted and the keys for that are fully protected" said Microsoft VP of Enterprise and OS Security, David Weston, speaking with Windows Central. "All of the sensitive Recall processes, so screenshots, screenshot processing, vector database, are now in a VBS Enclave. We basically took Recall and put it in a virtual machine, so even administrative users are not able to interact in that VM or run any code or see any data."
This change alone is the biggest improvement to Recall, ensuring that the data it collects is safely stored on your device and inaccessible by anyone but you. Not even Microsoft can see the data stored by Recall in the VBS Enclave, even if it wanted to. Recall will also rate limit attempts to access encrypted data, so potential malware won’t be able to brute force entry through the Recall app itself.



3175x175(CURRENT).thumb.jpg.b05acc060982b36f5891ba728e6d953c.jpg)
Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.