
Microsoft's BitLocker encryption is one of the more readily available encryption solution which allows users to safely encrypt and protect data from threat actors. However, it looks like BitLocker is not as safe as people may think.
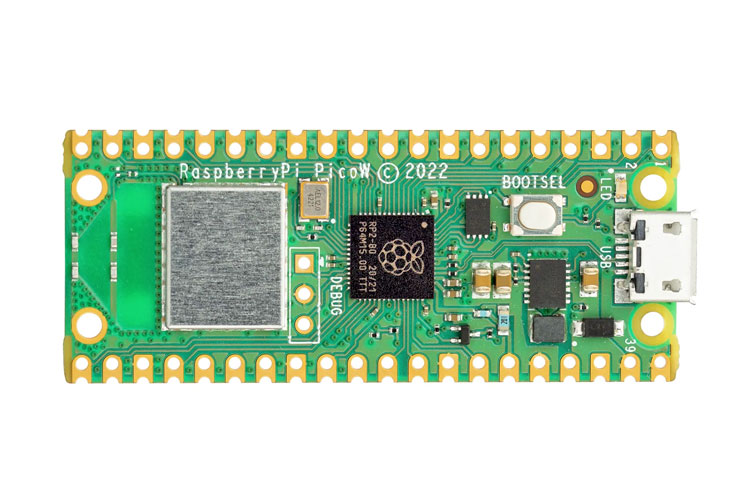
Earlier this week, YouTuber stacksmashing posted a video showing how he was able to intercept the BitLocker data and steal the encryption keys allowing him to decrypt data that was stored on the system. Not only that, but he achieved the results in 43 seconds using a Raspberry Pi Pico that probably costs less than $10.
To execute the attack, he took advantage of the Trusted Platform Module or TPM. In most computers and busiess laptops, TPM is located externally and uses LPC bus to send and receive data from the CPU. Microsoft's BitLocker relies on TPM to store critical data like Platform Configuration Registers and Volume Master Key.
When testing stacksmashing found that LPC bus communicates with CPU via communication lanes that are unencrypted on boot-up and can be tapped into in order to steal critical data. He executed the attack on an old Lenovo laptop that had an unused LPC connector on the motherboard next to the M.2 SSD slot. stacksmashing connected a Raspberry Pi Pico to the metal pins on the unused connector to capture the encryption keys on boot up. The Raspberry Pi was set to capture the binary 0s and 1s from TPM while the system was booting up, allowing him to piece together the Volume Master Key. Once done, he took out the encrypted drive and used dislocker with the Volume Master Key to decrypt the drive.
Microsoft does note that these attacks are possible but says it will require sophisticated tools and long physical access to the device. However, as shown in the video, someone prepared to execute an attack can do it in less than a minute.
There are, however, some caveats to this that needs to be kept in mind. This attack can only work with external TPM modules where CPU needs to get data from the module on the motherboard. Many new laptops and desktop CPUs now come with fTPM where the critical data is stored and managed inside the CPU itself. That said, Microsoft does recommend setting up a BitLocker PIN to stop these attacks but it is not easy to do so as you will require to setup a Group Policy to configure a PIN.


3175x175(CURRENT).thumb.jpg.b05acc060982b36f5891ba728e6d953c.jpg)
Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.