WordPress force installs Jetpack security update on 5 million sites
Automattic, the company behind the WordPress content management system, force deploys a security update on over five million websites running the Jetpack WordPress plug-in.
Jetpack is a remarkably popular WordPress plug-in that provides free security, performance, and website management features, including brute-force attack protection, site backups, secure logins, and malware scanning.
The plugin has more than 5 million active installations, and it is developed and maintained by Automattic, the company behind WordPress.
No in the wild exploitation
The vulnerability was found in the Carousel feature and its option to display comments for each image, with nguyenhg_vcs being the one credited for responsibly disclosing the security bug.
No other details are available regarding this security flaw to protect the sites that haven't yet been updated. However, we do know that Automattic addressed it with added authorization logic.
The announcement made by Automattic says the bug impacts all versions starting with the Jetpack 2.0 release and going back to November 2012.
The Jetpack development team added that it found no evidence that the vulnerability has been exploited in the wild.
"However, now that the update has been released, it is only a matter of time before someone tries to take advantage of this vulnerability," the developers warn.
Automattic is force installing patched versions on all websites running vulnerable Jetpack versions, with most sites already having been updated.
"To help you in this process, we worked with the WordPress.org Security Team to release patched versions of every version of Jetpack since 2.0," Automattic said. "Most websites have been or will soon be automatically updated to a secured version."
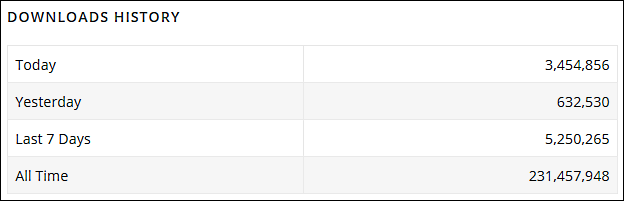
Currently, download stats available on the WordPress Plugins site confirm that the security updates have been pushed to most if not all exposed websites.
Forced updates used to patch critical bugs affecting millions
This is not the first time Automattic used the automated deployment of security updates to patch vulnerable plug-ins or WordPress installations.
WordPress lead developer Andrew Nacin stated in 2015 that the company had used automated updates only five times since its launch.
Samuel Wood, another WordPress developer, added in October 2020 that Automattic used the forced security updates feature to push "security releases for plugins many times" since WordPress 3.7 was released.
This hints at the fact that Automattic deploys forced updates to patch plug-ins used by millions of sites against critical security vulnerabilities.
For instance, in 2019, Jetpack received a critical security update to fix a bug in the way the plug-in processed embed code.
Another security update addressed an issue found during an internal audit of the Contact Form block in December 2018. A May 2016 critical security update patched a vulnerability in the way some Jetpack shortcodes were processed.
In related news, in 2018, threat actors also found a method to install backdoored plugins on WordPress websites using weakly protected WordPress.com accounts and Jetpack's remote management feature.
WordPress force installs Jetpack security update on 5 million sites
- aum
-

 1
1



3175x175(CURRENT).thumb.jpg.b05acc060982b36f5891ba728e6d953c.jpg)
Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.