The Australian Federal Police (AFP) have announced today that a 24-year-old woman from Melbourne, arrested in 2019 for her role in large-scale, cyber-enabled identity theft crimes, was sentenced to five years and six months in prison.
The woman pleaded guilty to her crimes on November 26, 2021.
According to the AFT, she was part of an international crime syndicate engaged in "large-scale and sophisticated cybercrimes," stealing at least $3.3 million and laundering another $2.5 million.
In addition to these figures, the criminals attempted to steal $7.5 million from their victims.
The AFP arrested the woman when she was 21 at the Melbourne Airport as part of an investigation codenamed "Operation Birks," and executed search warrants in her residence.
Further investigations aided by files found on seized devices revealed that the suspect was purchasing stolen identities of real individuals on the dark web, used fraudulently registered SIM cards, and spoofed email accounts to perform 'identity takeover.'
The crooks then used these identities to open over 60 bank accounts across various Australian financial institutions and then stole money from the victims' superannuation (Australian pension program a company creates for the benefit of its employees) and stock trading accounts.
For this operation, the gang used phishing websites hosted on typosquatted domains that were promoted via malvertising to ensure higher ranking in Google Search results.
"The offender worked with others to create a cloned website that mimicked the legitimate website of a superannuation fund, using a domain name that was almost identical to the legitimate site," explains the AFP report.
Online advertisements were used to promote the cloned website to bring it to the top of the search engine. The intention was to harvest members' usernames and passwords when they visited the cloned website ('phishing'). The stolen member information was used to gain unauthorized access to member accounts. - AFP
After withdrawing the money from the fraudulent bank accounts, the woman sent them to a contact in Hong Kong who purchased assets that are more difficult to trace (e.g. luxury products) that were resold.
Ultimately, portions of the laundered amounts were sent back to Australia in cryptocurrency, to minimize the chances of leaving a money trace.
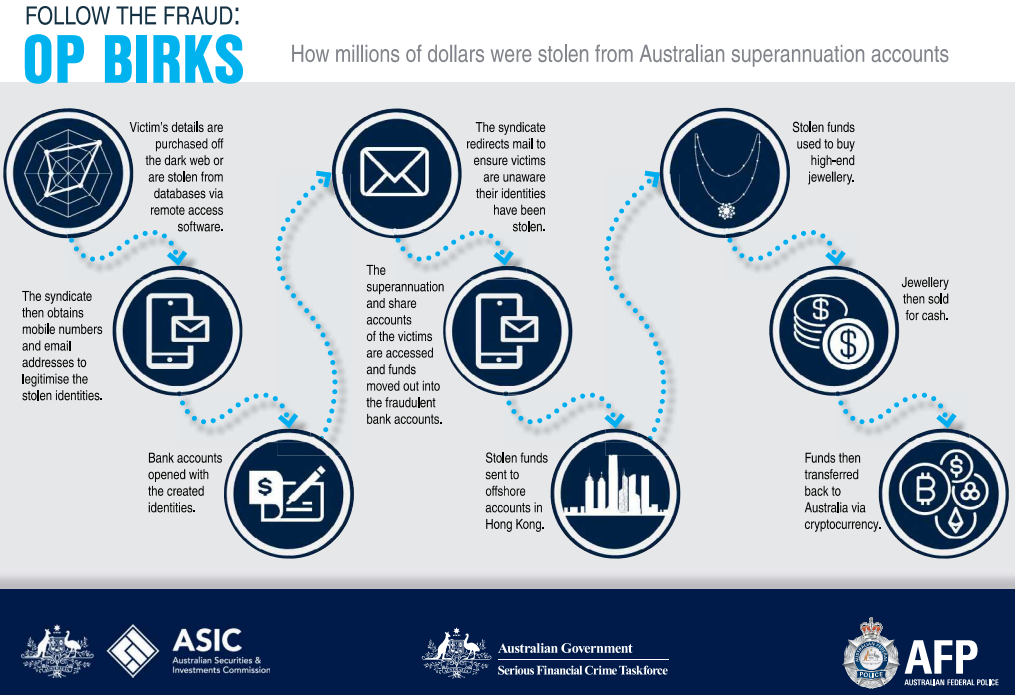
Operation Birks infographic (AFP)
As the AFP highlights in the report, most of the victims of these crimes had not realized that their identities had been stolen and sold on the dark web, so they had no way to defend against the fraud.




Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.