A Russian hacking group tracked as TA473, aka 'Winter Vivern,' has been actively exploiting vulnerabilities in unpatched Zimbra endpoints since February 2023 to steal the emails of NATO officials, governments, military personnel, and diplomats.
Two weeks ago, Sentinel Labs reported on a recent operation by 'Winter Vivern' using sites mimicking European agencies fighting cybercrime to spread malware that pretends to be a virus scanner.
Today, Proofpoint has published a new report on how the threat actor exploits CVE-2022-27926 on Zimbra Collaboration servers to access the communications of NATO-aligned organizations and persons.
Targeting Zimbra
Winter Vivern attacks begin with the threat actor scanning for unpatched webmail platforms using the Acunetix tool vulnerability scanner.
Next, the hackers send a phishing email from a compromised address, which is spoofed to appear as someone the target is familiar with or is somehow relevant to their organization.
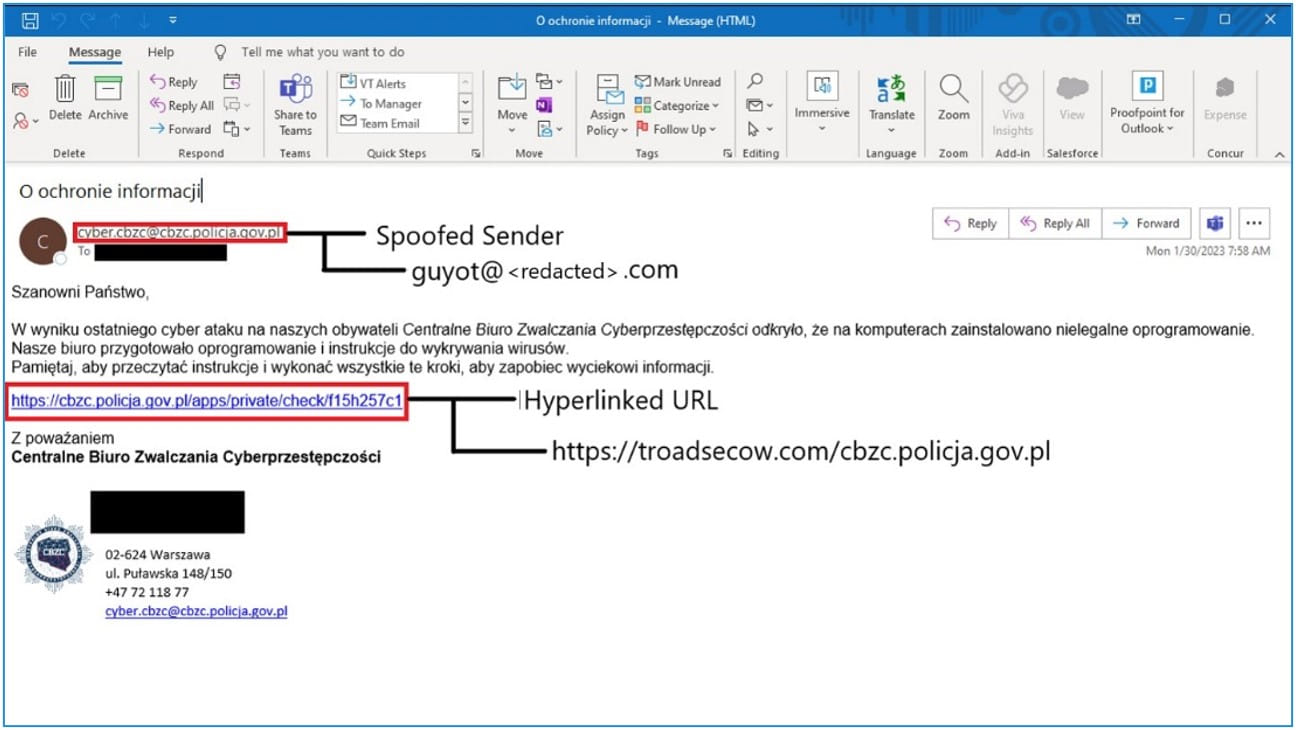
Email sent by Winter Vivern (Proofpoint)
The emails contain a link that exploits the CVE-2022-27926 in the target's compromised Zimbra infrastructure to inject other JavaScript payloads into the webpage.
These payloads are then used to to steal usernames, passwords, and tokens from cookies received from the compromised Zimbra endpoint. This information allows the threat actors to access the targets' email accounts freely.
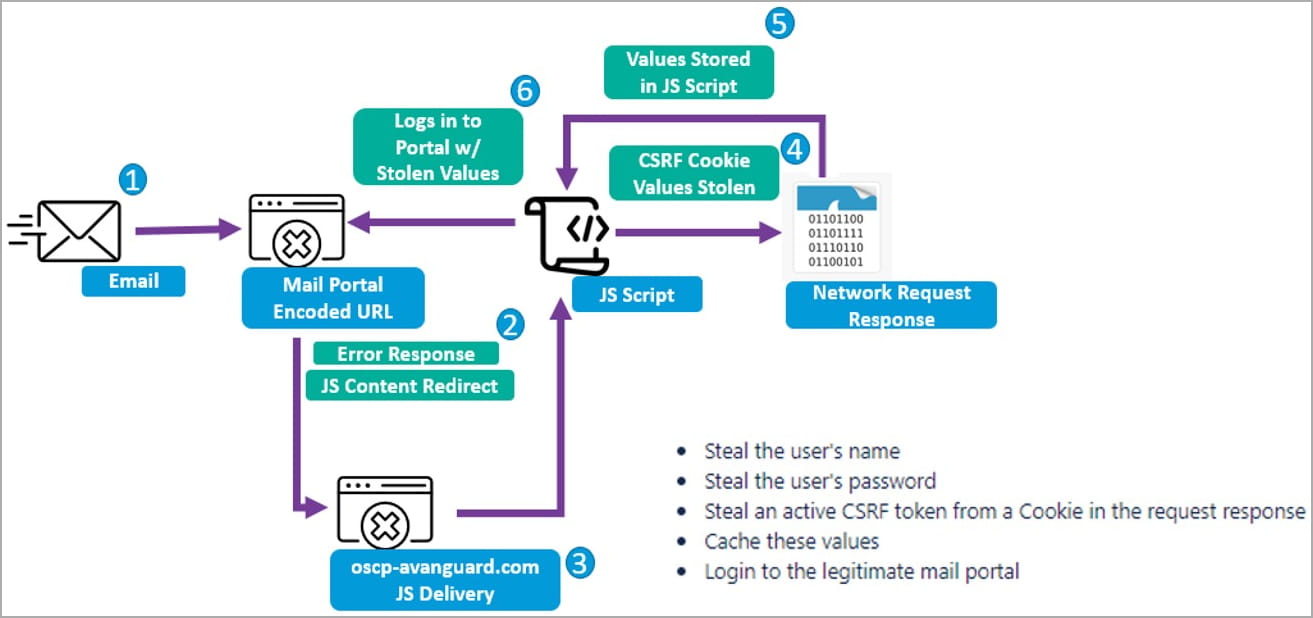
Complete attack chain (Proofpoint)
"These CSRF JavaScript code blocks are executed by the server that hosts a vulnerable webmail instance," explains Proofpoint in the reported.
"Further, this JavaScript replicates and relies on emulating the JavaScript of the native webmail portal to return key web request details that indicate the username, password, and CSRF token of targets."
"In some instances, researchers observed TA473 specifically targeting RoundCube webmail request tokens as well."
This detail demonstrates the diligence of the threat actors in pre-attack reconnaissance, figuring out which portal their target uses before crafting the phishing emails and setting the landing page function.
Apart from the three layers of base64 obfuscation applied on the malicious JavaScript to make analysis more complicated, 'Winter Vivern' also included parts of the legitimate JavaScript that runs in a native webmail portal, blending with normal operations and decreasing the likelihood of detection.
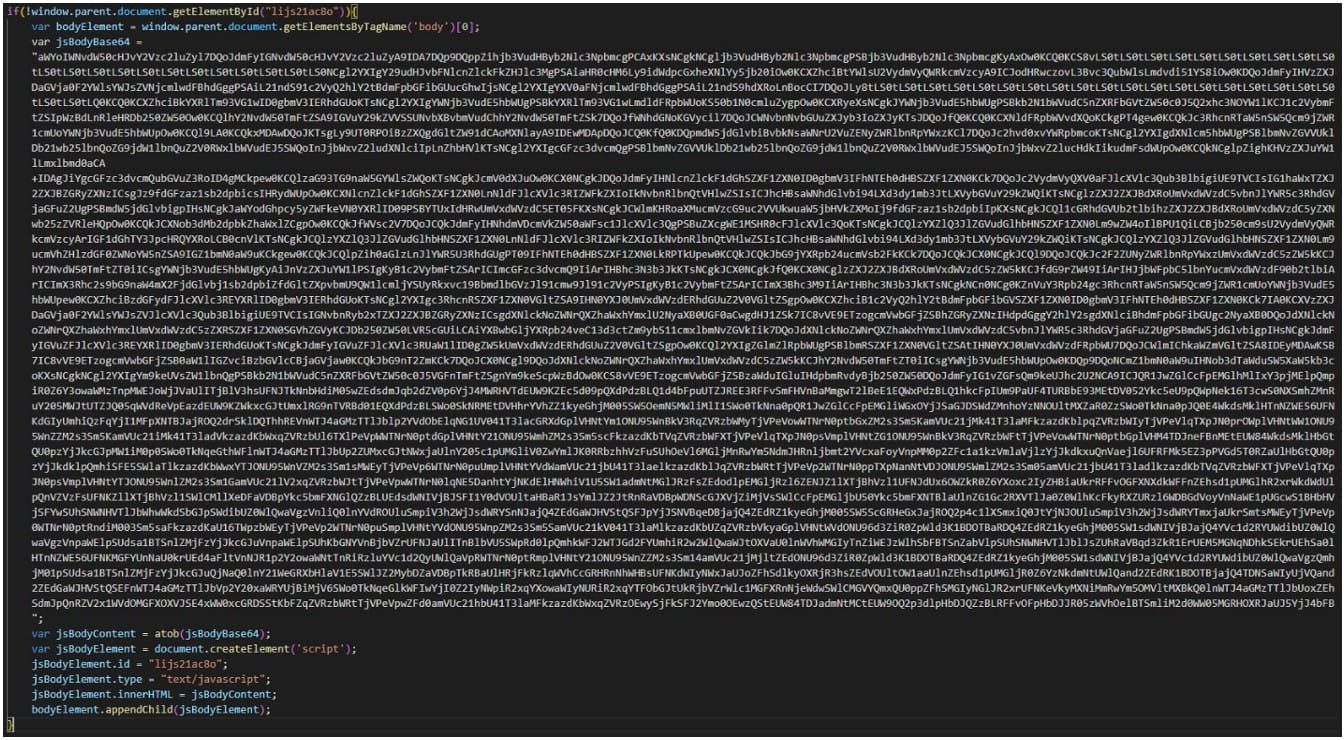
Obfuscated JavaScript (Proofpoint)
Finally, the threat actors can access sensitive information on the compromised webmails or maintain their hold to monitor communications over a period of time. Additionally, the hackers can use the breached accounts to carry out lateral phishing attacks and further their infiltration of the target organizations.
Despite researchers stating that 'Winter Vivern' is not particularly sophisticated, they follow an effective operational approach that works even against high-profile targets who fail to apply software patches quickly enough.
In this case, CVE-2022-27926 was fixed in Zimbra Collaboration 9.0.0 P24, released in April 2022.
Considering that the earliest attacks were observed in February 2023, the delay in applying the security update is measured to at least ten months.
- aum
-

 1
1




Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.