On the first day of Pwn2Own Vancouver 2024, contestants demoed Windows 11, Tesla, and Ubuntu Linux zero-day vulnerabilities and exploit chains to win $732,500 and a Tesla Model 3 car.
The competition started with Haboob SA's Abdul Aziz Hariri using an Adobe Reader exploit that combined an API restriction bypass and a command injection bug to gain code execution on macOS to earn $50,000.
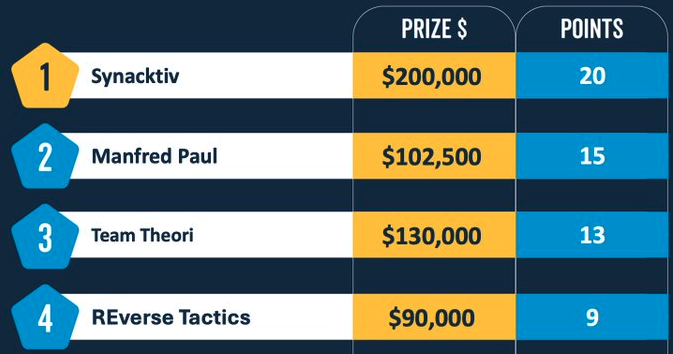
Synacktiv won the Tesla Model 3 and $200,000 after hacking the Tesla ECU with Vehicle (VEH) CAN BUS Control in under 30 seconds using an integer overflow.
Theori security researchers Gwangun Jung and Junoh Lee earned $130,000 after escaping a VMware Workstation VM to gain code execution as SYSTEM on the host Windows OS using a chain targeting an uninitialized variable bug, a UAF weakness, and a heap-based buffer overflow.
Reverse Tactics' Bruno PUJOS and Corentin BAYET collected $90,000 by exploiting two Oracle VirtualBox bugs and a Windows UAF to escape the VM and elevate privileges to SYSTEM.
The first day of the contest ended with Manfred Paul hacking the Apple Safari, Google Chrome, and Microsoft Edge web browsers, exploiting three zero-day vulnerabilities and winning $102,500.
Other attempts from the first day of Pwn2Own include:
- DEVCORE Research Team earned a $30,000 award after escalating privileges to SYSTEM on a fully patched Windows 11 system using an exploit that targeted two bugs, including a TOCTAU race condition. They were also awarded $10,000 for demoing an already-known Ubuntu Linux local privilege escalation (LPE) exploit.
- The KAIST Hacking Lab's Seunghyun Lee hacked the Google Chrome web browser using a Use-After-Free (UAF) vulnerability to collect $60,000.
- Kyle Zeng from ASU SEFCOM demoed another LPE exploit targeting Ubuntu Linux via a race condition to earn $20,000.
- Cody Gallagher also won $20,000 for an Oracle VirtualBox out-of-bounds (OOB) write zero-day vulnerability.
- Viettel Cyber Security's Dungdm also hacked Oracle's VirtualBox using a two-bug exploit chain for $20,000.
After the zero-days are demoed at Pwn2Own, vendors have 90 days to create and release security patches for all reported flaws before Trend Micro's Zero Day Initiative discloses them publicly.
Throughout Pwn2Own Vancouver 2024, security researchers will target fully patched products in the web browser, cloud-native/container, virtualization, enterprise applications, server, local escalation of privilege (EoP), enterprise communications, and automotive categories.
On the second day, Pwn2Own competitors will attempt to exploit zero-day bugs in Windows 11, VMware Workstation, Oracle VirtualBox, Mozilla Firefox, Ubuntu Desktop, Google Chrome, Docker Desktop, and Microsoft Edge.
After the two days of the hacking competition, the hackers can earn over $1,300,000, including a Tesla Model 3 car. The top award for hacking a Tesla is now $150,000, and the car itself.
Competitors can win a maximum award of $500,000 and a Tesla Model 3 car for an exploit that gives complete remote control with unconfined root when targeting the Tesla Autopilot.
Using a Windows kernel vulnerability, they can also get a $300,000 award for a successful Hyper-V Client guest-to-host escape and a privilege escalation on the host OS.
During last year's Vancouver Pwn2Own, won by Team Synacktiv, hackers earned $1,035,000 and a Tesla car for 27 zero-days (and several bug collisions) in Windows 11, Microsoft Teams, Microsoft SharePoint, macOS, Ubuntu Desktop, VMware Workstation, Oracle VirtualBox, and Tesla's Model 3.
Synacktiv also hacked the Tesla Modem and Infotainment System during the first edition of Pwn2Own Automotive in January, getting root permissions on a Tesla Modem by chaining three zero-days and demoing an Infotainment System sandbox escape via a two zero-day exploit chain.



3175x175(CURRENT).thumb.jpg.b05acc060982b36f5891ba728e6d953c.jpg)
Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.