Windows 10, iOS 15, Google Chrome, Apple Safari, Microsoft Exchange Server, and Ubuntu 20 were successfully broken into using original, never-before-seen exploits at the Tianfu Cup 2021, the fourth edition of the international cybersecurity contest held in the city of Chengdu, China.
Targets this year included Google Chrome running on Windows 10 21H1, Apple Safari running on Macbook Pro, Adobe PDF Reader, Docker CE, Ubuntu 20/CentOS 8, Microsoft Exchange Server 2019, Windows 10, VMware Workstation, VMware ESXi, Parallels Desktop, iPhone 13 Pro running iOS 15, domestic mobile phones running Android, QEMU VM, Synology DS220j DiskStation, and ASUS RT-AX56U router.
The Chinese version of Pwn2Own was started in 2018 in the wake of government regulation in the country that barred security researchers from participating in international hacking competitions because of national security concerns.
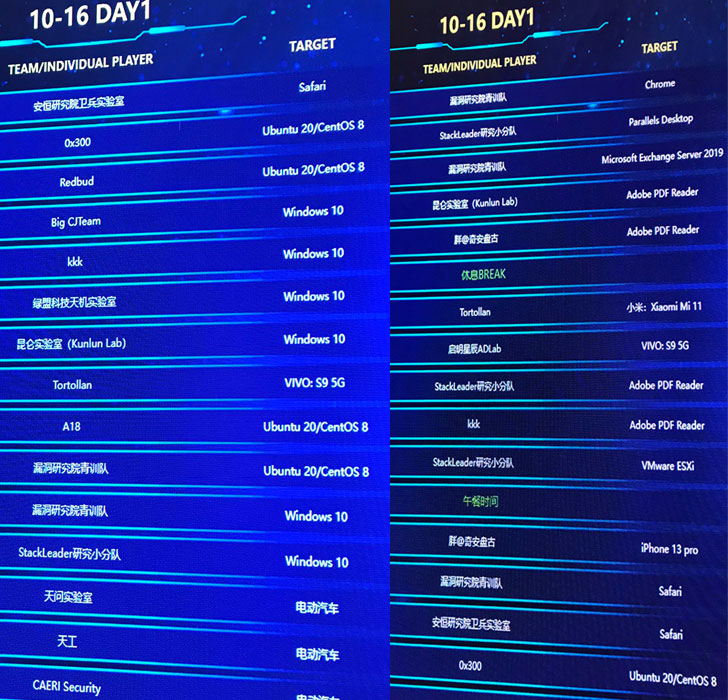
With the exception of Synology DS220j NAS, Xiaomi Mi 11 smartphone, and an unnamed Chinese electric vehicle, attacks were mounted successfully against every other target —
- Adobe PDF Reader
- Apple iPhone 13 Pro (running iOS 15)
- Apple Safari
- ASUS RT-AX56U
- Docker CE
- Google Chrome
- Microsoft Exchange Server
- Microsoft Windows 10
- Parallels Desktop
- QEMU VM
- Ubuntu 20/CentOS 8
- VMware ESXi
- VMWare Workstation
The two-day tournament, which took place over the weekend on October 16 and 17, saw security researchers winning 1.88 million in prize money, with Kunlun Lab taking the top spot ($654,500) for demonstrating successful exploits in iOS 15, including a remote code execution flaw in mobile Safari within 15 seconds. Researchers from the cybersecurity firm also pwned Google Chrome "to get Windows system kernel level privilege with only two bugs," Kunlun Lab's CEO @mj0011 tweeted.
Team PangU emerged second with a total haul of $522,500 for showing off a remote jailbreak in iPhone13 Pro running iOS 15, marking the first time the newly released iPhone model has been cracked at a public forum, while the Vulnerability Research Institute (VRI) came third with $392,500.
Details of the flaws have not been made public, but the companies are expected to release patches for the newly uncovered flaws in the upcoming weeks.
- Karlston
-

 1
1



Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.