A new WhatsApp phishing campaign impersonating WhatsApp's voice message feature has been discovered, attempting to spread information-stealing malware to at least 27,655 email addresses.
This phishing campaign aims to lead the recipient through a series of steps that will ultimately end with the installation of an information-stealing malware infection, opening the way to credential theft.
Information-stealing malware is aggressively distributed today via various means, with phishing remaining a primary channel for threat actors.
The information stolen by these special-purpose malware tools is predominately account credentials stored in browsers and applications but also targets cryptocurrency wallets, SSH keys, and even files stored on the computer.
WhatsApp voice messages as a lure
The new WhatsApp voice message phishing campaign was discovered by researchers at Armoblox, who are constantly on the lookout for new phishing threats.
For years, WhatsApp has had the ability to send voice messages to users in groups and private chats, with the feature receiving new enhancements last week.
A timely phishing attack pretends to be a notification from WhatsApp stating that they received a new private message. This email features an embedded “Play” button and audio clip duration and creation time details.
The sender, masquerading as a "Whatsapp Notifier" service, is using an email address belonging to the Center for Road Safety of the Moscow Region.
.jpg)
The phishing email impersonating WhatsApp (Armoblox)
Due to this being a genuine and legitimate entity, the messages aren't flagged or blocked by email security solutions, which typically is the biggest problem for phishing actors.
Armoblox believes this is a case of the hackers having somehow exploited the domain to promote their purpose, so the organization plays a role without knowledge.
If the recipient clicks on the "Play" button in the message body, they are redirected to a website that serves an allow/block prompt for installing a JS/Kryptic trojan.
To trick the victim into clicking on "Allow," the threat actors display a web page stating that you need to click 'Allow' to confirm you are not a robot. However, clicking these allow buttons will subscribe the user to browser notifications that send in-browser advertisements for scams, adult sites, and malware.
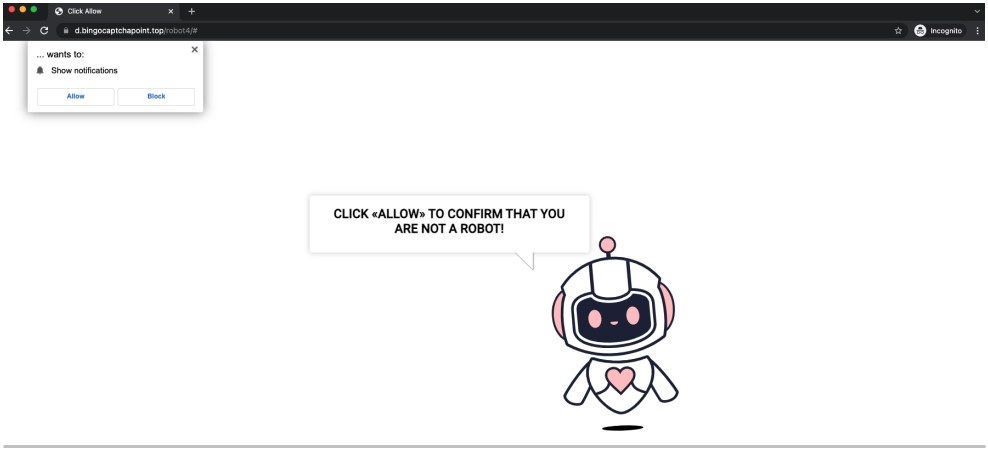
The website that installs the malware (Armoblox)
This simple trick can be very effective with people who are not consciously aware or thinking twice about their actions online.
Once the “allow” option is pressed, the browser will prompt the user to install the payload, which in this case is an information-stealing malware.
How to protect yourself
The fact that the emails in this campaign bypassed numerous secure email solutions makes it a particularly nasty case, but the clues that it was phishing were still abundant.
First, the email address has nothing to do with WhatsApp, and the same goes for the landing URL that requests the victims to click “Allow” to confirm they’re real. They are both obviously out of WhatsApp’s domain space.
Secondly, voice messages received on WhatsApp are downloaded automatically in the client app, so the IM company would never inform you about receiving one via email.
Thirdly, the phishing email features no WhatsApp logo, which is almost certainly to avoid having trouble with the VMC checks introduced by Gmail last year.
To protect yourself from phishing attempts, always take your time to look into potential signs of fraud when receiving messages that make surprising claims, and never jump into action.
If you need to check something, do it yourself through the official website or application, and never by following URLs or instructions provided in the message.
WhatsApp voice message phishing emails push info-stealing malware
- DKT27
-

 1
1



3175x175(CURRENT).thumb.jpg.b05acc060982b36f5891ba728e6d953c.jpg)
Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.