Watch Out! Zyxel Firewalls and VPNs Under Active Cyberattack
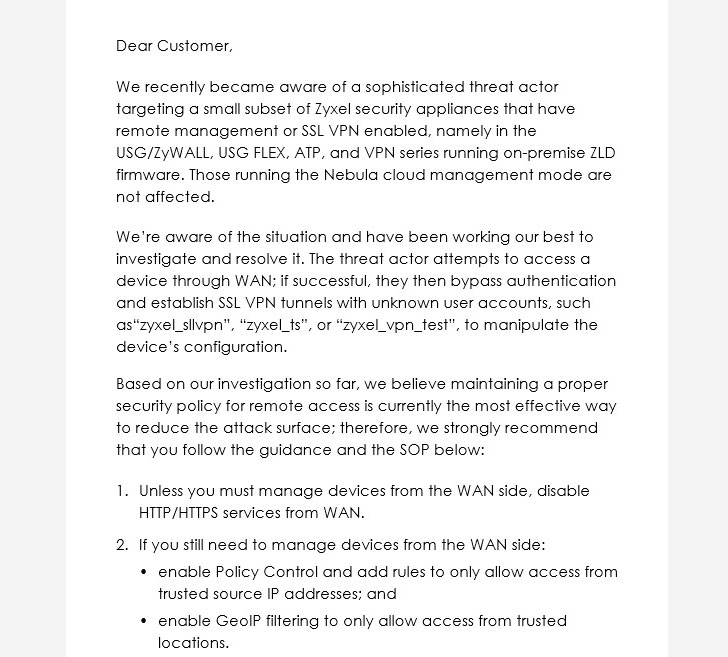
Taiwanese networking equipment company Zyxel is warning customers of an ongoing attack targeting a "small subset" of its security products such as firewall and VPN servers.
Attributing the attacks to a "sophisticated threat actor," the firm noted that the attacks single out appliances that have remote management or SSL VPN enabled, namely in the USG/ZyWALL, USG FLEX, ATP, and VPN series running on-premise ZLD firmware, implying that the targeted devices are publicly accessible over the internet.
"The threat actor attempts to access a device through WAN; if successful, they then bypass authentication and establish SSL VPN tunnels with unknown user accounts, such as 'zyxel_slIvpn', 'zyxel_ts', or 'zyxel_vpn_test', to manipulate the device's configuration," Zyxel said in an email message, which was shared on Twitter.
As of writing, it's not immediately known if the attacks are exploiting previously known vulnerabilities in Zyxel devices or if they leverage a zero-day flaw to breach the systems. Also unclear is the scale of the attack and the number of users affected.
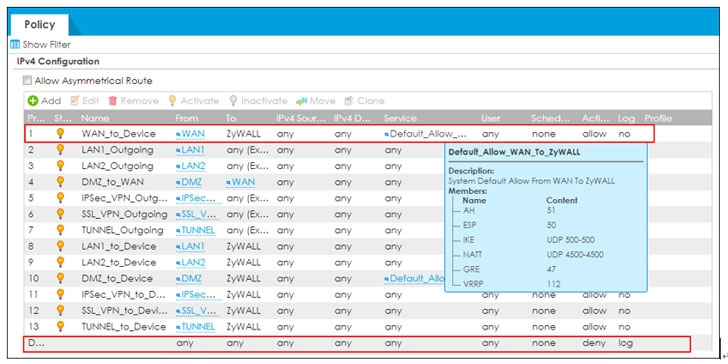
To reduce the attack surface, the company is recommending customers to disable HTTP/HTTPS services from the WAN and implement a list of restricted geo-IP to enable remote access only from trusted locations.
Earlier this year, Zyxel patched a critical vulnerability in its firmware to remove a hard-coded user account "zyfwp" (CVE-2020-29583) that could be abused by an attacker to login with administrative privileges and compromise the confidentiality, integrity, and availability of the device.
The development comes as enterprise VPNs and other network devices have become a top target of attackers in a series of campaigns aimed at finding new avenues into corporate networks, giving the threat actors the ability to laterally move across the network and gather sensitive intelligence for espionage and other financially-motivated operations.
- Karlston
-

 1
1




Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.