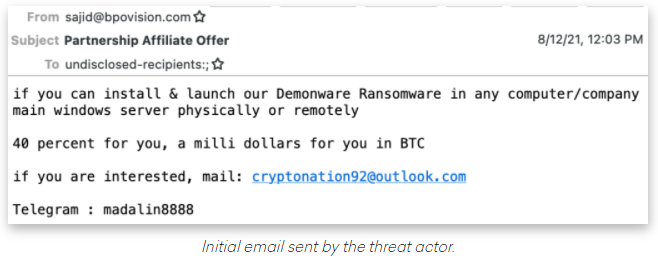
Criminal hackers will try almost anything to get inside a profitable enterprise and secure a million-dollar payday from a ransomware infection. Apparently now that includes emailing employees directly and asking them to unleash the malware inside their employer’s network in exchange for a percentage of any ransom amount paid by the victim company.
Crane Hassold, director of threat intelligence at Abnormal Security, described what happened after he adopted a fake persona and responded to the proposal in the screenshot above. It offered to pay him 40 percent of a million-dollar ransom demand if he agreed to launch their malware inside his employer’s network.
This particular scammer was fairly chatty, and over the course of five days it emerged that Hassold’s correspondent was forced to change up his initial approach in planning to deploy the DemonWare ransomware strain, which is freely available on GitHub.
“According to this actor, he had originally intended to send his targets—all senior-level executives—phishing emails to compromise their accounts, but after that was unsuccessful, he pivoted to this ransomware pretext,” Hassold wrote.
Abnormal Security documented how it tied the email back to a young man in Nigeria who acknowledged he was trying to save up money to help fund a new social network he is building called Sociogram.
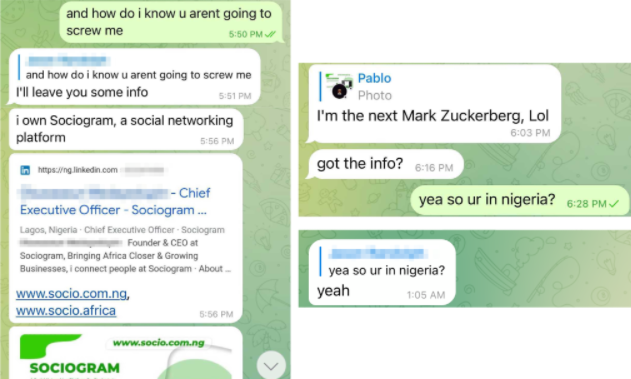
This attacker’s approach may seem fairly amateur, but it would be a mistake to dismiss the threat from West African cybercriminals dabbling in ransomware. While multi-million dollar ransomware payments are hogging the headlines, by far the biggest financial losses tied to cybercrime each year stem from so-called Business Email Compromise (BEC) or CEO Scams, in which crooks mainly based in Africa and Southeast Asia will spoof communications from executives at the target firm in a bid to initiate unauthorized international wire transfers.
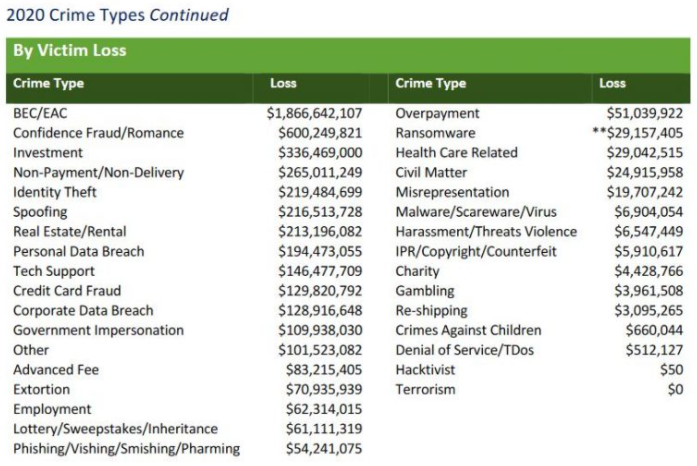
According to the latest figures (PDF) released by the FBI Internet Crime Complaint Center (IC3), the reported losses from BEC scams continue to dwarf other cybercrime loss categories, increasing to $1.86 billion in 2020.
“Knowing the actor is Nigerian really brings the entire story full circle and provides some notable context to the tactics used in the initial email we identified,” Hassold wrote. “For decades, West African scammers, primarily located in Nigeria, have perfected the use of social engineering in cybercrime activity.”
“While the most common cyber attack we see from Nigerian actors (and most damaging attack globally) is business email compromise (BEC), it makes sense that a Nigerian actor would fall back on using similar social engineering techniques, even when attempting to successfully deploy a more technically sophisticated attack like ransomware,” Hassold concluded.
DON’T QUIT YOUR DAY JOB
Cybercriminals trolling for disgruntled employees is hardly a new development. Big companies have long been worried about the very real threat of disgruntled employees creating identities on darknet sites and then offering to trash their employer’s network for a fee (for more on that, see my 2016 story, Rise of the Darknet Stokes Fear of the Insider).
Indeed, perhaps this enterprising Nigerian scammer is just keeping up with current trends. Several established ransomware affiliate gangs that have recently rebranded under new banners seem to have done away with the affiliate model in favor of just buying illicit access to corporate networks.
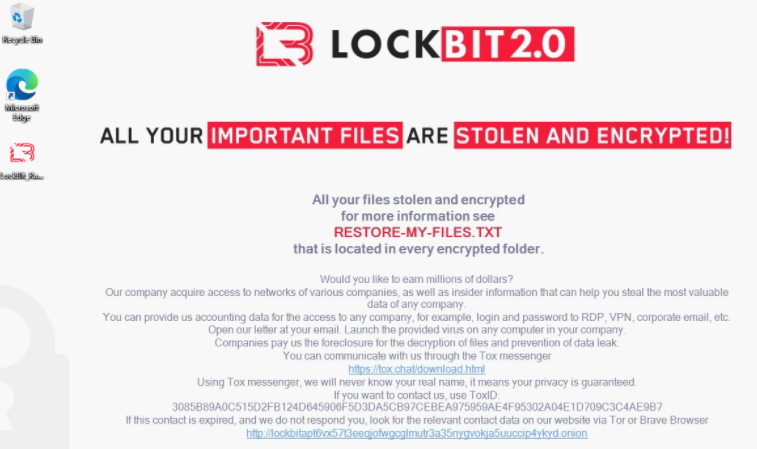
For example, the Lockbit 2.0 ransomware-as-a-service gang actually includes a solicitation for insiders in the desktop wallpaper left behind on systems encrypted with the malware.
“Would you like to earn millions of dollars? Our company acquires access to networks of various companies, as well as insider information that can help you steal the most valuable data of any company,” LockBit’s unusual ad reads. “You can provide us accounting data for the access to any company, for example, login and password to RDP, VPN, corporate email, etc. Open our letter at your email. Launch the provided virus on any computer in your company. Companies pay us the foreclosure for the decryption of files and prevention of data leak.”
Likewise, the newly formed DarkMatter ransomware gang kicked off its presence on the cybercrime forums with the unassuming thread, “Buying/monetizing your access to corporate networks.” The rest of the post reads:
We are looking for access to corporate networks in the following countries:
– the USA
– Canada
– Australia
– the UK
All lines of business except for:
– Healthcare
– Government entities.
Requirements:
– Revenue according to ZoomInfo: over 100 million.
– Number of hosts: 500 to 15,000.
– We do not accept networks that anybody else has already tried to work on.
Two options of cooperation:
– We buy networks: 3 to 100k.
– We monetize them (subject to negotiation on a case-by-case basis).
How we work:
You select an option of cooperation. -> You provide access to the network. -> We check it. -> We take it or not (depending on whether it meets the requirements).
- Karlston
-

 1
1


Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.