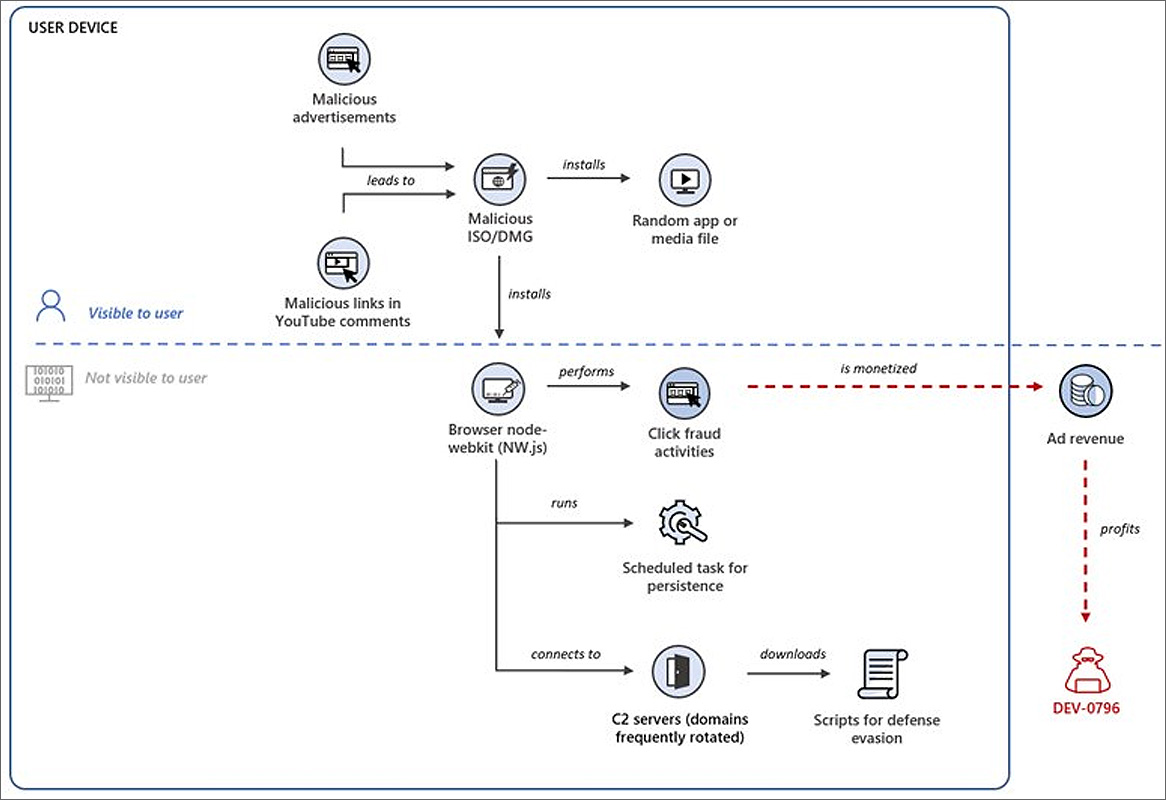
VMware and Microsoft are warning of an ongoing, widespread Chromeloader malware campaign that has evolved into a more dangerous threat, seen dropping malicious browser extensions, node-WebKit malware, and even ransomware in some cases.
Chromeloader infections surged in Q1 2022, with researchers at Red Canary warning about the dangers of the browser hijacker used for marketing affiliation and advertising fraud.
Back then, the malware infected Chrome with a malicious extension that redirected user traffic to advertising sites to perform click fraud and generate income for the threat actors.
A few months later, Palo Alto Network's Unit 42 noticed that Chromeloader was evolving into an info-stealer, attempting to snatch data stored on the browsers while retaining its adware functions.
On Friday evening, Microsoft warned about an "ongoing wide-ranging click fraud campaign" attributed to a threat actor tracked as DEV-0796 using Chromeloader to infect victims with various malware.
Today, analysts at VMware published a technical report describing different variants of Chromeloader that were used in August and this month, some of which are dropping much more potent payloads.
New variants dropping malware
The ChromeLoader malware is delivered in ISO files that are distributed through malicious ads, browser redirects, and YouTube video comments.
ISO files have become a popular method to distribute malware since Microsoft began blocking Office macros by default. Furthermore, when double-clicking on an ISO in Windows 10 and later, they are automatically mounted as a CDROM under a new drive letter, making them an efficient way to distribute multiple malware files at once.
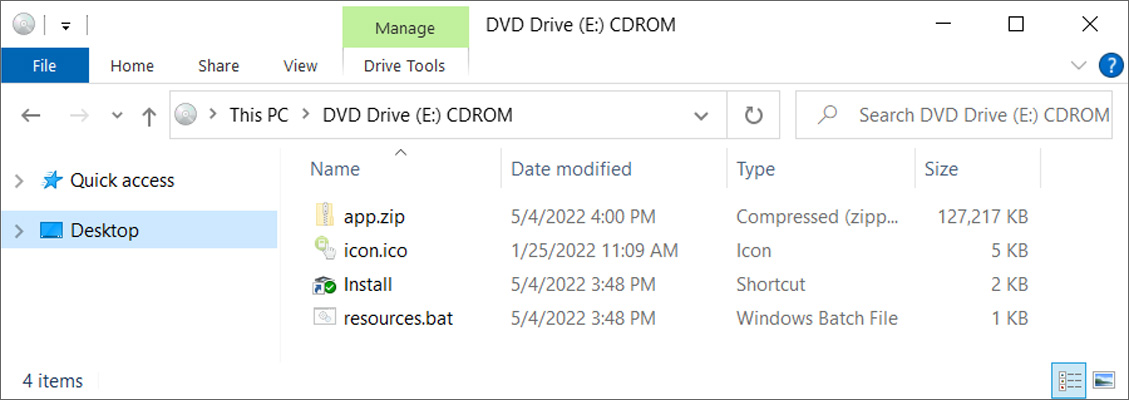
ChromeLoader ISOs commonly contain four files, a ZIP archive containing the malware, an ICON file, a batch file (commonly named Resources.bat) that installs the malware, and a Windows shortcut that launches the batch file.
As part of their research, VMware sampled at least ten Chromeloader variants since the start of the year, with the most interesting appearing after August.
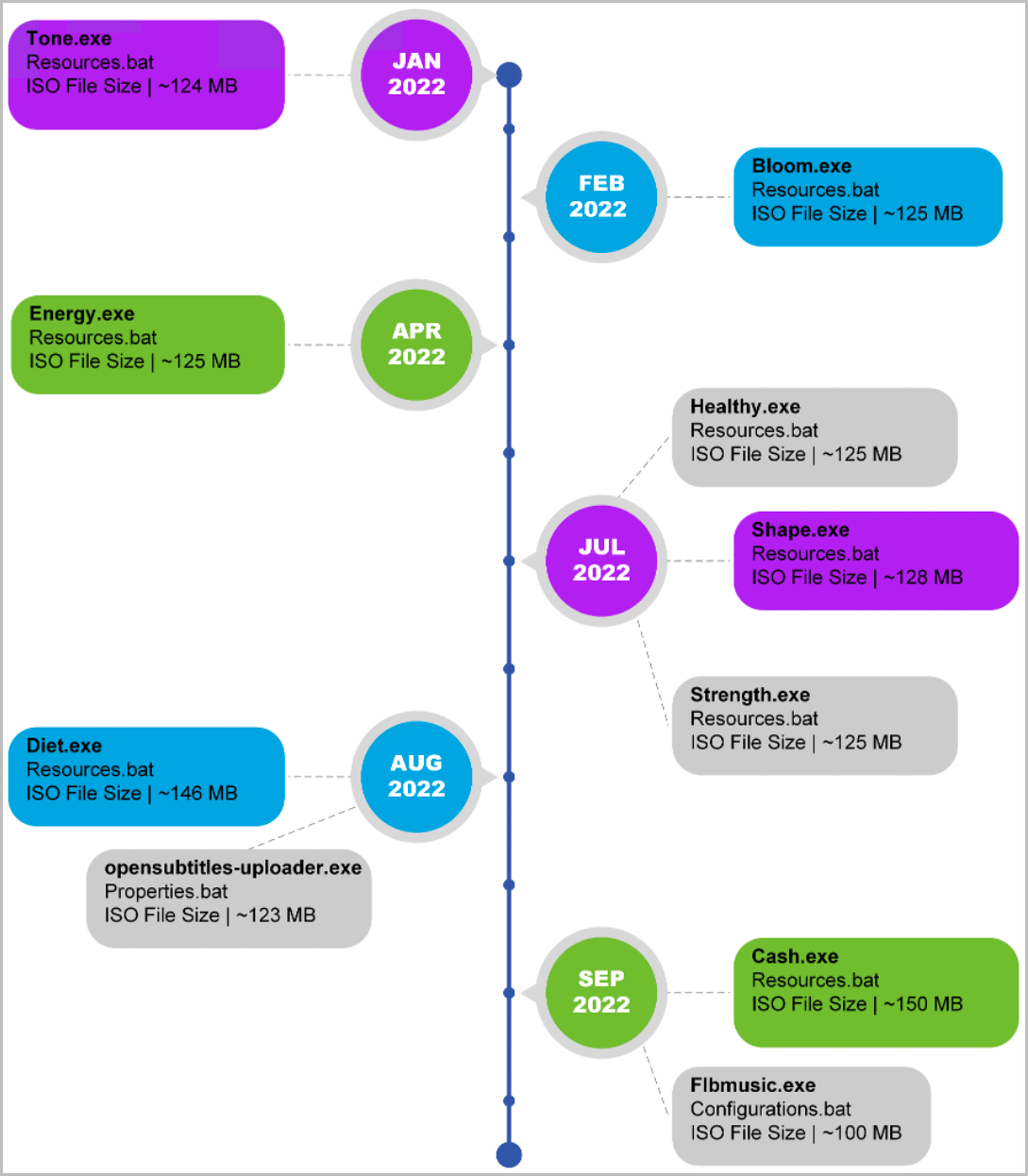
Timeline of Chromeloader evolution (VMware)
The first example is a program mimicking OpenSubtitles, a utility helping users locate subtitles for movies and TV shows. In this campaign, the threat actors moved away from their usual "Resources.bat" file and switched to one named "properties.bat," used to install the malware and establish persistence by adding Registry keys.
Another notable case is "Flbmusic.exe," mimicking the FLB Music player, featuring an Electron runtime and enabling the malware to load additional modules for network communication and port snooping.
For some variants, the attacks turned a bit destructive, extracting ZipBombs that overload the system with a massive unpacking operation.
"As recent as late August, ZipBombs have been seen being dropped onto infected systems. The ZipBomb is dropped with the initial infection in the archive the user downloads. The user must double-click for the ZipBomb to run. Once run, the malware destroys the user's system by overloading it with data," explains VMware's report.
Even more concerning, recent Chromeloader variants have been seen deploying the Enigma ransomware in an HTML file.
Enigma is an old ransomware strain using a JavaScript-based installer and an embedded executable so that it can be launched directly from the default browser.
After the encryption is complete, the ".enigma" filename extension is appended to the files, while the ransomware drops a "readme.txt" file containing instructions for the victims.
Adware is not to be ignored
Because adware doesn't create notable damage to victims' systems, besides eating up some bandwidth, it is usually a threat that is ignored or downplayed by analysts.
However, every software that nests into systems without being detected is a candidate for more significant trouble, as its authors may apply modifications that facilitate more aggressive monetization options.
While Chromeloader started as adware, it is a perfect example of how threat actors are experimenting with more potent payloads, exploring more profitable alternatives to advertising fraud.
Source: Bleeping Computer




Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.