If you haven't patched CVE-2022-22954 yet, now would be an excellent time to do so.
Hackers have been exploiting a now-patched vulnerability in VMware Workspace ONE Access in campaigns to install various ransomware and cryptocurrency miners, a researcher at security firm Fortinet said on Thursday.
CVE-2022-22954 is a remote code execution vulnerability in VMware Workspace ONE Access that carries a severity rating of 9.8 out of a possible 10. VMware disclosed and patched the vulnerability on April 6. Within 48 hours, hackers reverse-engineered the update and developed a working exploit that they then used to compromise servers that had yet to install the fix. VMware Workspace ONE access helps administrators configure a suite of apps employees need in their work environments.
In August, researchers at Fortiguard Labs saw a sudden spike in exploit attempts and a major shift in tactics. Whereas before the hackers installed payloads that harvested passwords and collected other data, the new surge brought something else—specifically, ransomware known as RAR1ransom, a cryptocurrency miner known as GuardMiner, and Mirai, software that corrals Linux devices into a massive botnet for use in distributed denial-of-service attacks.
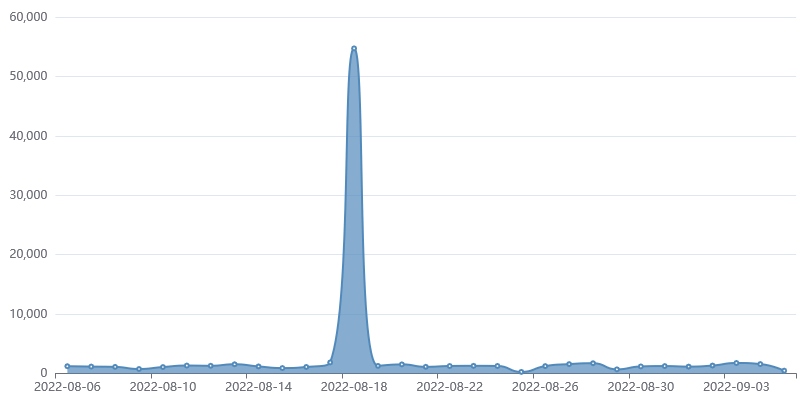
“Although the critical vulnerability CVE-2022-22954 is already patched in April, there are still multiple malware campaigns trying to exploit it,” Fortiguard Labs researcher Cara Lin wrote. Attackers, she added, were using it to inject a payload and achieve remote code execution on servers running the product.
The Mirai sample Lin saw getting installed was downloaded from http[:]//107[.]189[.]8[.]21/pedalcheta/cutie[.]x86_64 and relied on a command and control server at “cnc[.]goodpackets[.]cc. Besides delivering junk traffic used in DDoSes, the sample also attempted to infect other devices by guessing the administrative password they used. After decoding strings in the code, Lin found the following list of credentials the malware used:
|
hikvision |
1234 |
win1dows |
S2fGqNFs |
|
root |
tsgoingon |
newsheen |
12345 |
|
default |
solokey |
neworange88888888 |
guest |
|
bin |
user |
neworang |
system |
|
059AnkJ |
telnetadmin |
tlJwpbo6 |
iwkb |
|
141388 |
123456 |
20150602 |
00000000 |
|
adaptec |
20080826 |
vstarcam2015 |
v2mprt |
|
Administrator |
1001chin |
vhd1206 |
support |
|
NULL |
xc3511 |
QwestM0dem |
7ujMko0admin |
|
bbsd-client |
vizxv |
fidel123 |
dvr2580222 |
|
par0t |
hg2x0 |
samsung |
t0talc0ntr0l4! |
|
cablecom |
hunt5759 |
epicrouter |
zlxx |
|
pointofsale |
nflection |
admin@mimifi |
xmhdipc |
|
icatch99 |
password |
daemon |
netopia |
|
3com |
DOCSIS_APP |
hagpolm1 |
klv123 |
|
OxhlwSG8 |
In what appears to be a separate campaign, attackers also exploited CVE-2022-22954 to download a payload from 67[.]205[.]145[.]142. The payload included seven files:
- phpupdate.exe: Xmrig Monero mining software
- config.json: Configuration file for mining pools
- networkmanager.exe: Executable used to scan and spread infection
- phpguard.exe: Executable used for guardian Xmrig miner to keep running
- init.ps1: Script file itself to sustain persistence via creating scheduled task
- clean.bat: Script file to remove other cryptominers on the compromised host
- encrypt.exe: RAR1 ransomware
In the event RAR1ransom has never been installed before, the payload would first run the encrypt.exe executable file. The file drops the legitimate WinRAR data compression executable in a temporary Windows folder. The ransomware then uses WinRAR to compress user data into password-protected files.
The payload would then start the GuardMiner attack. GuardMiner is a cross-platform mining Trojan for the Monero currency. It has been active since 2020.
The attacks underscore the importance of installing security updates in a timely manner. Anyone who has yet to install VMware’s April 6 patch should do so at once.
- Karlston and alf9872000
-

 2
2




Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.