As many as 130 different ransomware families have been found to be active in 2020 and the first half of 2021, with Israel, South Korea, Vietnam, China, Singapore, India, Kazakhstan, Philippines, Iran, and the U.K. emerging as the most affected territories, a comprehensive analysis of 80 million ransomware-related samples has revealed.
Google's cybersecurity arm VirusTotal attributed a significant chunk of the activity to the GandCrab ransomware-as-a-service (RaaS) group (78.5%), followed by Babuk (7.61%), Cerber (3.11%), Matsnu (2.63%), Wannacry (2.41%), Congur (1.52%), Locky (1.29%), Teslacrypt (1.12%), Rkor (1.11%), and Reveon (0.70%).
"Attackers are using a range of approaches, including well-known botnet malware and other Remote Access Trojans (RATs) as vehicles to deliver their ransomware," VirusTotal Threat Intelligence Strategist Vicente Diaz said. "In most cases, they are using fresh or new ransomware samples for their campaigns."
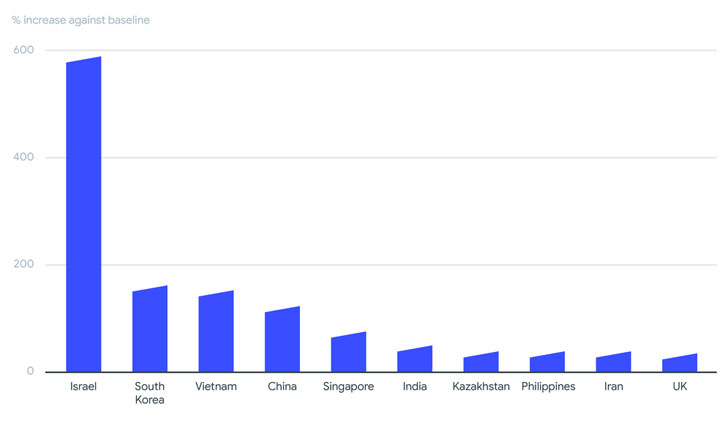
Some of the other key points uncovered in the study are as follows —
- GandCrab accounted for most of the ransomware activity in the first two quarters of 2020, with the Babuk ransomware family driving a surge of infections in July 2021.
- 95% of ransomware files detected were Windows-based executables or dynamic link libraries (DLLs), while 2% were Android-based.
- Around 5% of the analyzed samples were associated with exploits related to Windows elevation of privileges, SMB information disclosures, and remote execution.
- Emotet, Zbot, Dridex, Gozi, and Danabot were the primary malware artifacts used to distribute ransomware.
The findings come in the wake of a relentless wave of ransomware attacks aimed at critical infrastructure, with cybercriminal gangs aggressively pursuing victims in critical sectors, including pipeline operators and healthcare facilities, even as the landscape has witnessed a continuous shift wherein ransomware groups evolve, splinter, and reorganize under new names, or fall off the radar to evade scrutiny.
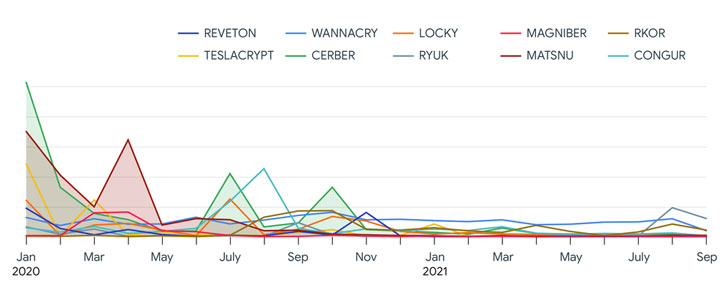
If anything, the explosion of new malware families has drawn new actors into participating in these lucrative schemes, turning ransomware into a profitable criminal business model.
"While big campaigns come and go, there is a constant baseline of ransomware activity of approximately 100 ransomware families that never stops," the report said. "In terms of ransomware distribution attackers don't appear to need exploits other than for privilege escalation and for malware spreading within internal networks."
- Kaos and Karlston
-

 2
2




Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.