VirusTotal has published a cheat sheet to help researchers create queries leading to more specific results from the malware intelligence platform.
File search modifiers can assist with refining the output but the cheat sheet shows how they can be combined in real-world scenarios to find particular data.
More targeted searches
In a blog post on Monday, Google security engineer Alexey Firsh provides examples of how the cheat sheet can be used to find files connected to certain entities, groups of activities, documents, networks, and non-Windows malware samples.
Using a specific ‘entity’ search modifier, analysts can look for files according to IP addresses, domains, URLs, or files. The plan is to also include VirusTotal collections in this collection of modifiers.
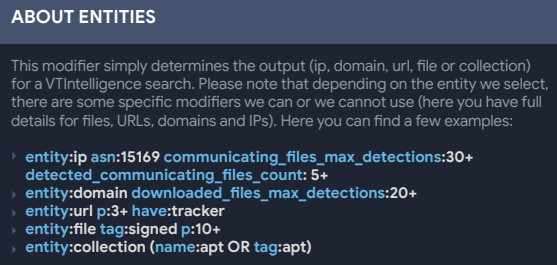
VirusTotal cheat sheet - modifiers for 'entity' search
To help researchers follow the tracks of a threat actor, Firsh notes that researchers can combine the name of the malware family or the campaign with the verdict of antivirus engines on VirusTotal.
This method is well-suited for detecting advanced attackers and would uncover related data in collections curated by various users of the VirusTotal platform.
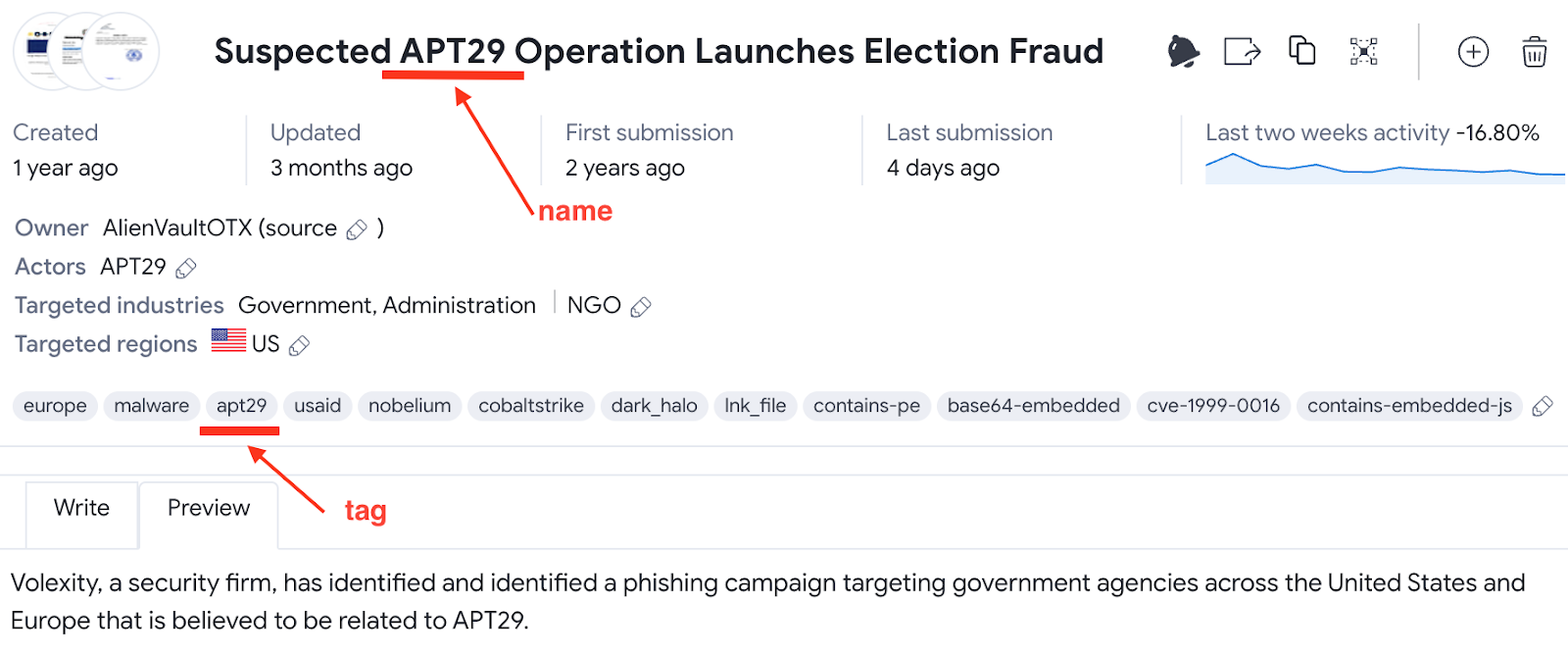 VirusTotal cheat sheet - finding specific group activities
VirusTotal cheat sheet - finding specific group activities
The search can be narrowed down or mixed with queries based on crowdsourced rules (YARA, IDS, Sigma).
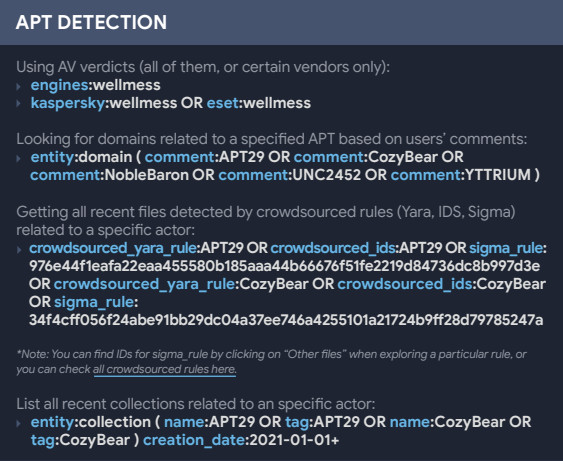
VirusTotal cheat sheet - detecting APT activity
VirusTotal’s cheat sheet covers examples of real-life cases where file search modifiers filter data signed by specific vendors and emails from a certain server that have an attachment or not.
Researchers can also use keywords that allow finding files for other operating systems than Windows, like Android, macOS, and Symbian.
For Android, the samples are processed using the open-source Androguard tool for looking inside the packages, including code strings, manifest entities, and certificate signatures.
A relatively new feature is looking for explicit package names. However, this works only with files indexed starting March 2022.
VirusTotal’s cheat sheet (PDF) is just three pages at the moment but it packs multiple categories of keyword combinations to find malicious or suspicious files.
It can also be a shortcut to link malware to operations from known and unknown actors or to uncover new and lurking threats.
VirusTotal plans to update the cheat sheet with fresh options that would make searching intelligence on the platform easier, quicker, and more targeted.
- Karlston
-

 1
1




Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.