The Vice Society ransomware operation has switched to using a custom ransomware encrypt that implements a strong, hybrid encryption scheme based on NTRUEncrypt and ChaCha20-Poly1305.
According to cybersecurity firm SentinelOne, which discovered the new strain and named it "PolyVice," it's likely that Vice Society sourced it from a vendor who supplies similar tools to other ransomware groups.
Vice Society first appeared in the summer of 2021, when they began stealing data from corporate networks and encrypting devices. The threat actors would then perform double-extortion attacks, threatening to publish the data if a ransom is not paid.
Historically, Vice Society has used other ransomware operations' encryptors during attacks, including Zeppelin, Five Hands, and HelloKitty.
However, this appears to have changed, with Vice Society now using a new encryptor that is believed to be generated by a commodity ransomware builder.
New "PolyVice" encryptor
The new PolyVice strain, however, gives Vice Society attacks a unique signature, appending the ".ViceSociety" extension onto locked files and dropping ransom notes named 'AllYFilesAE'.
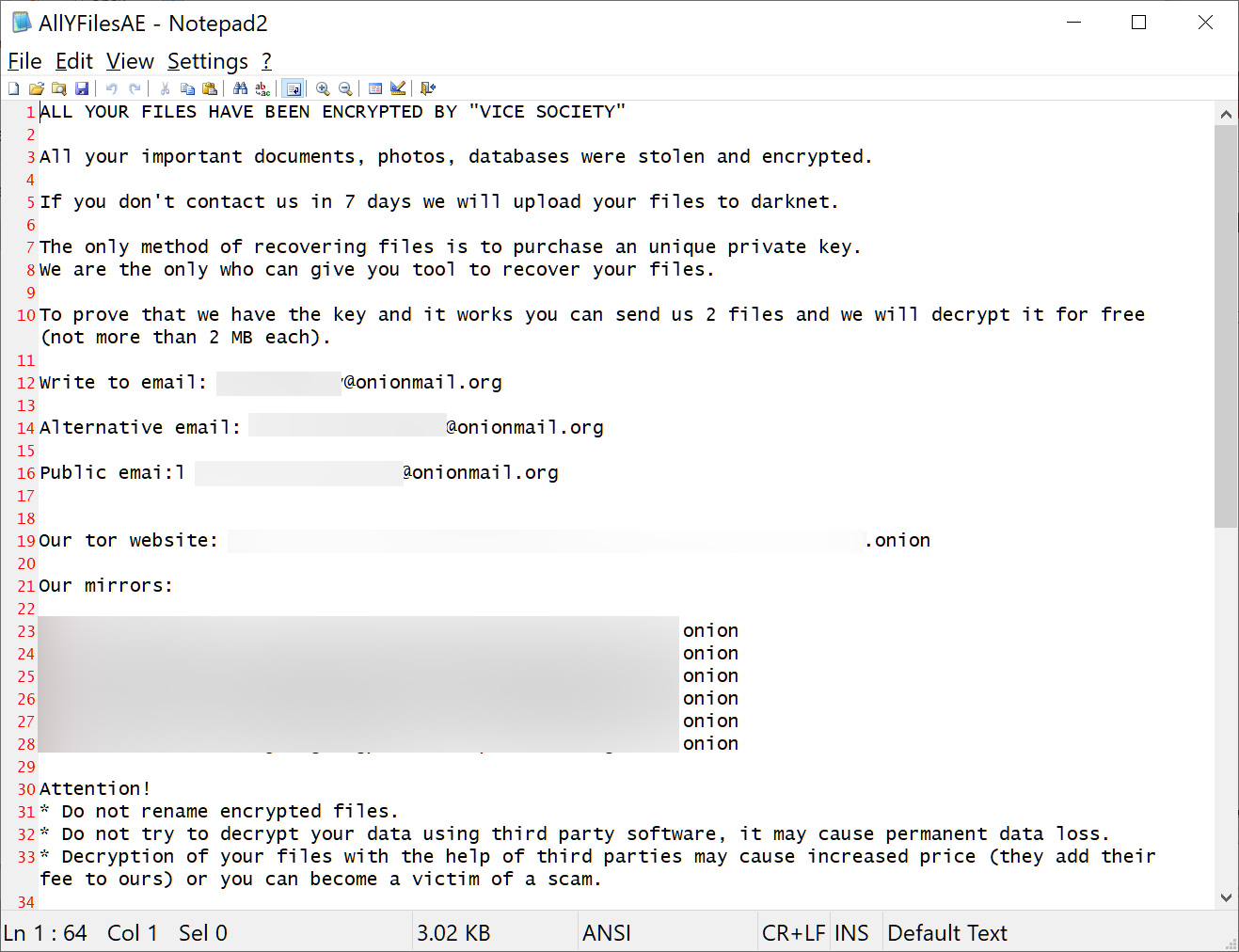
Vice Society ransom note
Source: BleepingComputer
The new variant was first seen in the wild on July 13, 2022, but it wasn't fully adopted by the group until much later.
SentinelOne's analysis reveals that PolyVice has extensive code similarities to Chilly ransomware and SunnyDay ransomware, with a 100% match on functions.
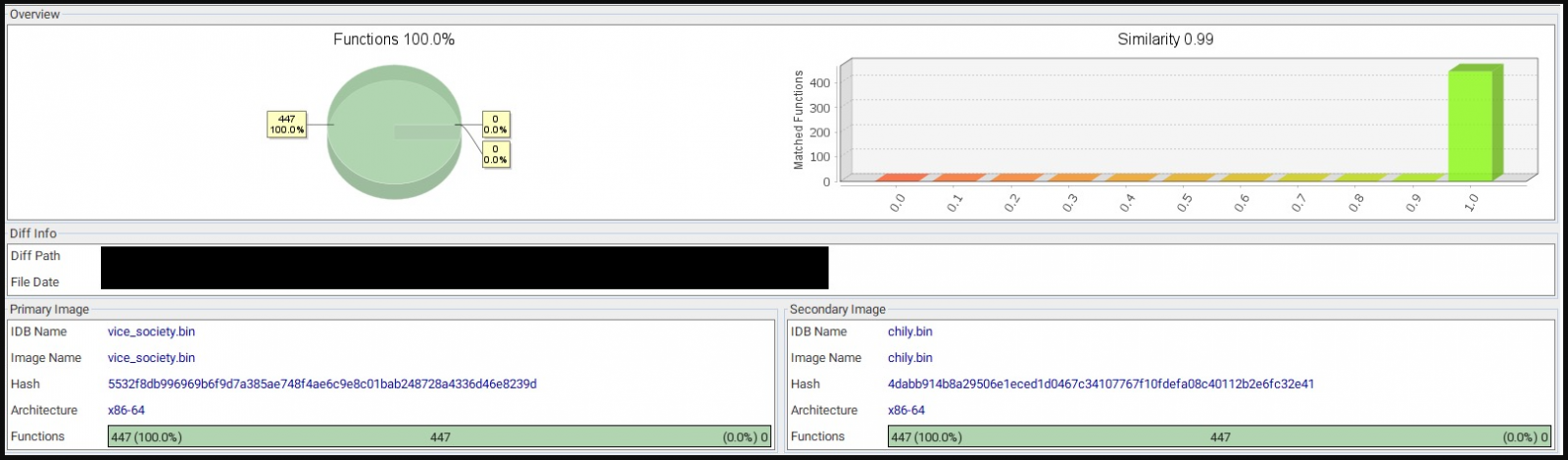
Similarity between Chilly and PolyVice (SentinelOne)
The differences lie in campaign-specific details like the file extension, ransom note name, hardcoded master key, wallpaper, etc., which supports the common vendor hypothesis.
"The code design suggests the ransomware developer provides a builder that enables buyers to independently generate any number of lockers/decryptors by binary patching a template payload," explains SentinelOne in the report.
"This allows buyers to customize their ransomware without revealing any source code. Unlike other known RaaS builders, buyers can generate branded payloads, enabling them to run their own RaaS programs."
Hybrid encryption
PolyVice uses a hybrid encryption scheme combining asymmetric encryption with the NTRUEncrypt algorithm and symmetric encryption with the ChaCha20-Poly1305 algorithm.
Upon launch, the payload imports a pre-generated 192-bit NTRU public key and then generates a random 112-bit NTRU private key pair on the compromised system, which is unique to each victim.
This pair is then used for encrypting the ChaCha20-Poly1305 symmetric keys, which are unique to each file. Finally, the NTRU key pair is eventually encrypted using the public NTRU key to protect it from retrieval attempts.
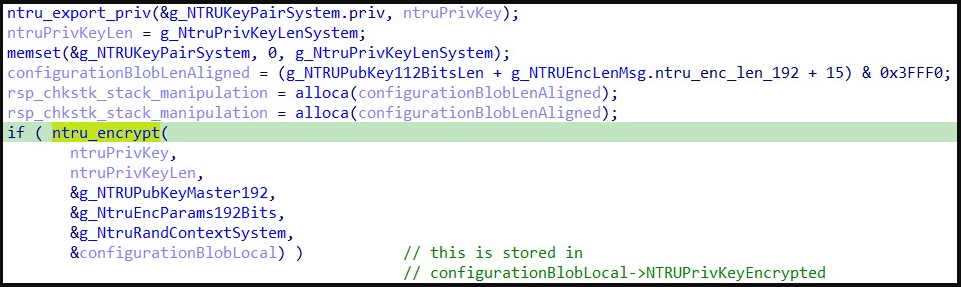
Encryption of NTRU private key pair (SentinelOne)
PolyVice ransomware is a 64-bit binary that uses multi-threading for parallel symmetric data encryption, utilizing the victim's processor in full to speed up the encryption process.
Moreover, each PolyVice worker reads the file content to determine what speed optimizations can be applied in each case. These optimizations depend on the file size, with PolyVice applying intermittent encryption selectively.
- Files smaller than 5MBs are fully encrypted.
- Files between 5MB and 100MB are encrypted partially, breaking them into 2.5MB chunks and skipping every second chunk.
- Files bigger than 100MB are broken into ten evenly distributed chunks, and 2.5MB of each chunk is encrypted.
After encryption, each PolyVice worker writes the file footer with information necessary for decryption.
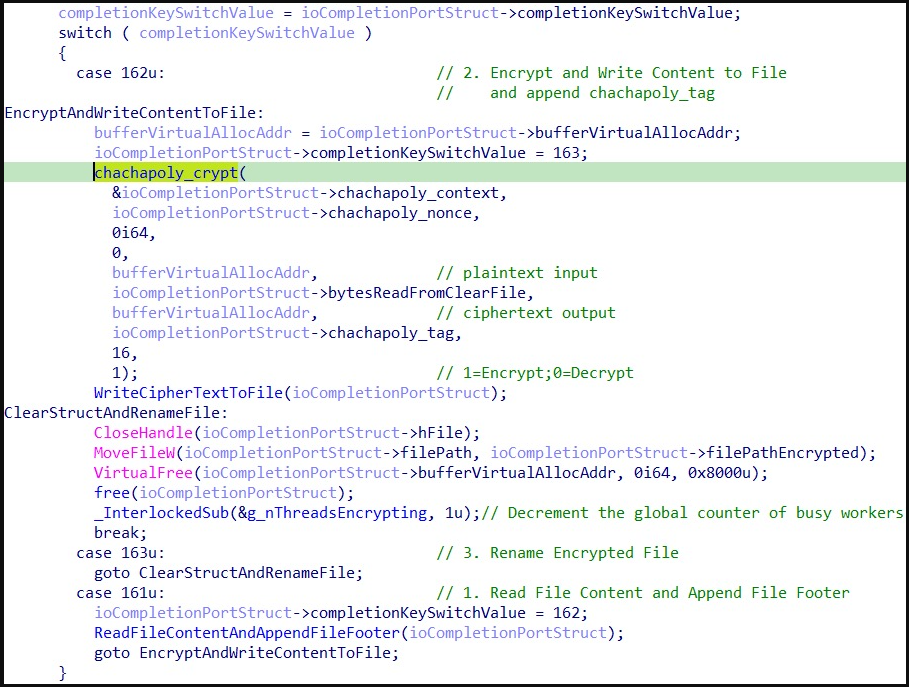
PolyVice worker thread code (SentinelOne)
All these features indicate that whoever develops the new ransomware strains used by Vice Society, Chilly, and SunnyDay ransomware is an experienced and knowledgeable malware creator.
In conclusion, SentinelOne's findings further underline the trend of outsourcing in the space, with ransomware gangs paying specialists to create sophisticated, high-performing tools.
Depending on the level of availability and cost, these tools may make it easier for low-skilled ransomware actors to launch catastrophic attacks and cause significant damage to organizations.
- Karlston
-

 1
1




Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.