According to a new report, almost half of Android-based mobile phones used by U.S. state and local government employees are running outdated versions of the operating system, exposing them to hundreds of vulnerabilities that can be leveraged for attacks.
These statistics come from a report by cybersecurity firm Lookout, based on an analysis of 200 million devices and 175 million applications from 2021 to H2 2022.
The report additionally warns of a rise in all threat metrics, including attempted phishing attacks against government employees, reliance on unmanaged mobile devices, and liability points in mission-critical networks.
Outdated mobile OS
Outdated versions of mobile operating systems allow attackers to exploit vulnerabilities that can be used to breach targets, run code on the device, plant spyware, steal credentials, and more.
For example, last week, Apple released iOS 16.1, fixing an actively exploited zero-day memory corruption flaw used by hackers against iPhone users to achieve arbitrary code execution with kernel privileges.
Lookout reports that ten months after iOS 15 had been made available to users, 5% of federal government employees and 30% of state and local government devices were running older versions of the operating system.
The situation is much worse for Android, as ten months after the release of version 12, approximately 30% of federal devices and almost 50% of state and local government devices still needed to upgrade to the latest versions, thus remaining vulnerable to bugs that can be exploited in attacks.
It should be noted that Android 13 is the latest version of the operating system, but it was released after the first half of 2022, from which this data was collected.
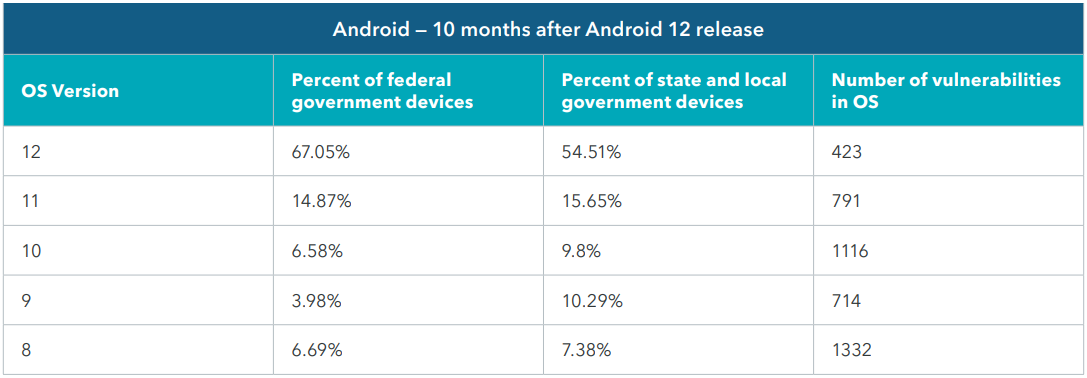
Notably, 10.7% of the federal government and another 17.7% of state and local government devices were running Android 8 and 9, which reached the end of support in November 2021 and March 2022, respectively.
These two OS versions carry over two thousand known vulnerabilities that Google will not fix, and the list only gets longer each month.
Mobile attacks rising
According to Lookout, the most common attack against mobile users is malware delivery, accounting for about 75%, while credential harvesting represents most of the remaining percentage.
While commodity malware usually infects Android mobile devices using fake apps, advanced spyware developers are known to use zero-day vulnerabilities in targeted attacks against journalists, politicians, and activists.
The analysts say when comparing year-over-year stats, malware distribution is gradually dropping, and credential theft attacks are increasing.
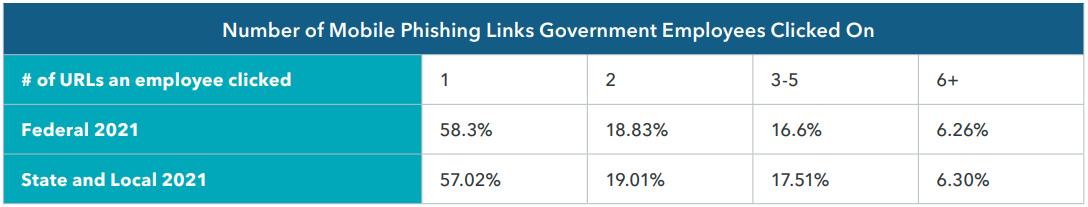
In 2022, 1 out of 11 government employees monitored by Lookout were targeted by a phishing attack, with both managed and unmanaged devices having roughly the same targeting rate.
Of those who clicked on the malicious links and were warned about their error, 57% did not repeat their mistake, 19% clicked again, and 24% clicked over three times.
To aid in securing devices, the U.S. Cybersecurity & Infrastructure Agency (CISA) has created a 'Known Exploited Vulnerabilities Catalog' that contains a list of vulnerabilities actively exploited in attacks and a deadline by which federal agencies must patch them.
However, while CISA advises state, local, and tribal governments to follow the same guidelines, they are not required to do so under this directive.
Furthermore, the report comes mere days before the U.S. midterm elections, with Trellix and the FBI reporting that election workers and election officials are being targeted with phishing campaigns to install malware or steal credentials.
- Karlston
-

 1
1




Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.