As many as 29,000 network storage devices manufactured by Taiwan-based QNAP are vulnerable to hacks that are easy to carry out and give unauthenticated users on the Internet complete control, a security firm has warned.
The vulnerability, which carries a severity rating of 9.8 out of a possible 10, came to light on Monday, when QNAP issued a patch and urged users to install it. Tracked as CVE-2022-27596, the vulnerability makes it possible for remote hackers to perform a SQL injection, a type of attack that targets web applications that use the Structured Query Language. SQL injection vulnerabilities are exploited by entering specially crafted characters or scripts into the search fields, login fields, or URLs of a buggy website. The injections allow for the modifying, stealing, or deleting of data or the gaining of administrative control over the systems running the vulnerable apps.
QNAP’s advisory on Monday said that network-attached storage devices running QTS versions before 5.0.1.2234 and QuTS Hero versions prior to h5.0.1.2248 were vulnerable. The post also provided instructions for updating to the patched versions.
On Tuesday, security firm Censys reported that data collected from network scan searches showed that as many as 29,000 QNAP devices may not have been patched against CVE-2022-27596. Researchers found that of the 30,520 Internet-connected devices showing what version they were running, only 557, or about 2 percent, were patched. In all, Censys said it detected 67,415 QNAP devices. The 29,000 figure was estimated by applying the 2 percent patch rate to the total number of devices.
“Given that the Deadbolt ransomware is geared to target QNAP NAS devices specifically, it’s very likely that if an exploit is made public, the same criminals will use it to spread the same ransomware again,” Censys researchers wrote. “If the exploit is published and weaponized, it could spell trouble to thousands of QNAP users.”
In an email, a Censys representative said that as of Wednesday, researchers found 30,475 QNAP devices that showed their version numbers (45 fewer than on Tuesday), and that of those, 29,923 are running versions that are vulnerable to CVE-2022-27596.
Tuesday’s Censys report said that devices vulnerable to CVE-2022-27596 were most common in the US, followed by Italy and Taiwan.
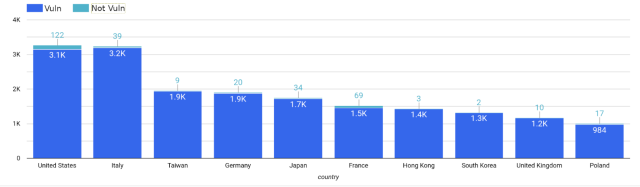
Censys also provided the following breakdown:
| Country | Total Hosts | Non-Vulnerable Hosts | Vulnerable Hosts |
| United States | 3,271 | 122 | 3,149 |
| Italy | 3,239 | 39 | 3,200 |
| Taiwan | 1,951 | 9 | 1,942 |
| Germany | 1,901 | 20 | 1,881 |
| Japan | 1,748 | 34 | 1,714 |
| France | 1,527 | 69 | 1,458 |
| Hong Kong | 1,425 | 3 | 1,422 |
| South Korea | 1,313 | 2 | 1,311 |
| United Kingdom | 1,167 | 10 | 1,157 |
| Poland | 1,001 | 17 | 984 |
In the past, QNAP has also recommended that users follow all of these steps to lower the chances of getting hacked:
- Disable the port forwarding function on the router.
- Set up myQNAPcloud on the NAS to enable secure remote access and prevent exposure to the Internet.
- Update the NAS firmware to the latest version.
- Update all applications on the NAS to their latest versions.
- Apply strong passwords for all user accounts on the NAS.
- Take snapshots and back up regularly to protect your data.
As reported by Bleeping Computer, QNAP devices over the years have been successfully hacked and infected with other ransomware strains, including Muhstik, eCh0raix/QNAPCrypt, QSnatch, Agelocker, Qlocker, DeadBolt, and Checkmate. Users of these devices should take action now.



3175x175(CURRENT).thumb.jpg.b05acc060982b36f5891ba728e6d953c.jpg)

Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.