Cybersecurity researchers on Tuesday disclosed details of an unpatched vulnerability in macOS Finder that could be abused by remote adversaries to trick users into running arbitrary commands on the machines.
"A vulnerability in macOS Finder allows files whose extension is inetloc to execute arbitrary commands, these files can be embedded inside emails which if the user clicks on them will execute the commands embedded inside them without providing a prompt or warning to the user," SSD Secure Disclosure said in a write-up published today.
Park Minchan, an independent security researcher, has been credited with reporting the vulnerability which affects macOS versions of Big Sur and prior.
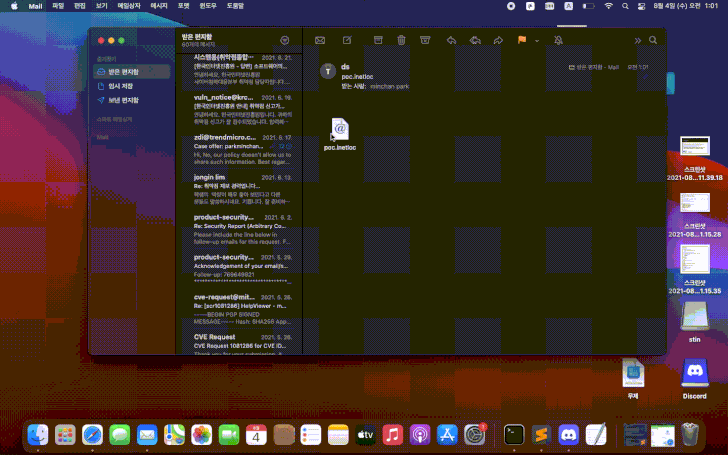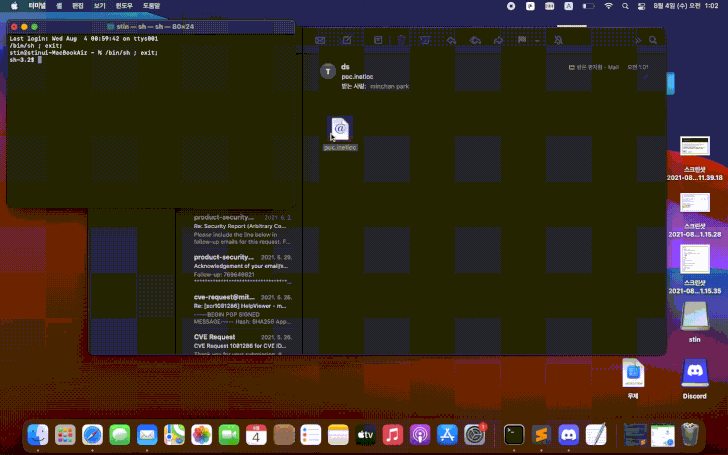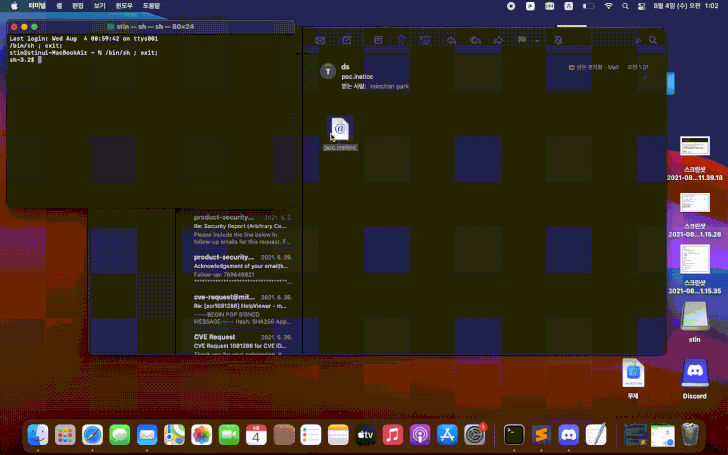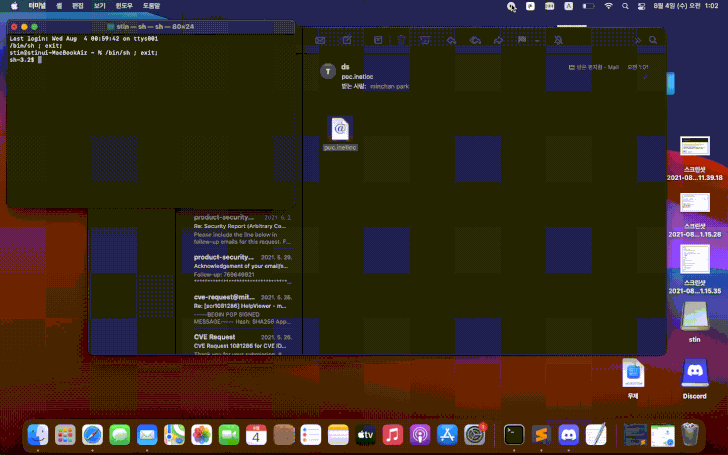
The weakness arises due to the manner macOS processes INETLOC files — shortcuts to internet locations such as RSS feeds or Telnet connections containing username and password for SSH — resulting in a scenario that allows commands embedded in those files to be executed without any warning.
"The case here INETLOC is referring to a 'file://' protocol which allows running locally (on the user's computer) stored files," SSD said. "If the INETLOC file is attached to an email, clicking on the attachment will trigger the vulnerability without warning."
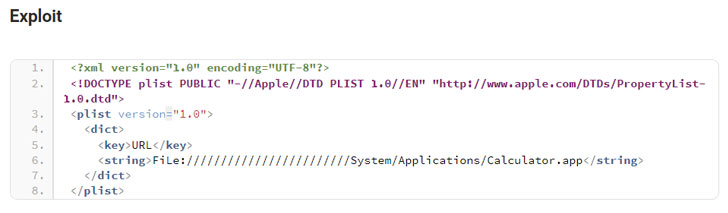
Although newer versions of macOS have blocked the 'file://' prefix, using 'File://' or 'fIle://' has been found to circumvent the check effectively. We have reached out to Apple, and we will update the story if we hear back.
- Karlston
-

 1
1




Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.