A vulnerability in the domain name system (DNS) component of a popular C standard library that is present in a wide range of IoT products may put millions of devices at DNS poisoning attack risk.
A threat actor can use DNS poisoning or DNS spoofing to redirect the victim to a malicious website hosted at an IP address on a server controlled by the attacker instead of the legitimate location.
The library uClibc and its fork from the OpenWRT team, uClibc-ng. Both variants are widely used by major vendors like Netgear, Axis, and Linksys, as well as Linux distributions suitable for embedded applications.
According to researchers at Nozomi Networks, a fix is not currently available from the developer of the developer of uClibc, leaving products of up to 200 vendors at risk.
Vulnerability details
The uClibc library is a C standard library for embedded systems that offers various resources needed by functions and configuration modes on these devices.
The DNS implementation in that library provides a mechanism for performing DNS-related requests like lookups, translating domain names to IP addresses, etc.
Nozomi reviewed the trace of DNS requests performed by a connected device using the uClibc library and found some peculiarities caused by an internal lookup function.
After investigating further, the analysts discovered that the DNS lookup request's transaction ID was predictable. Because of this, DNS poisoning might be possible under certain circumstances.
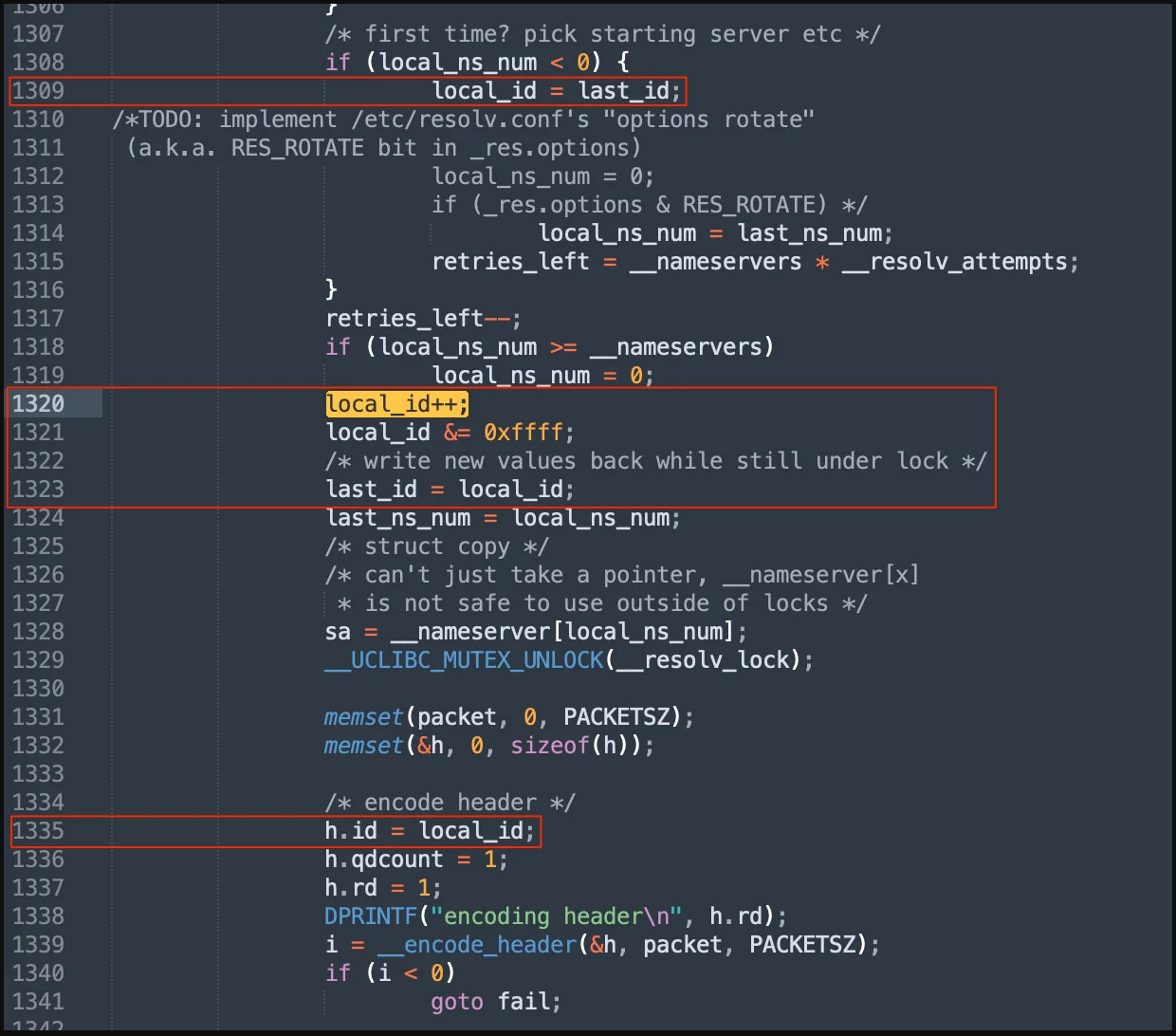
Flaw implications
If the operating system doesn't use source port randomization, or if it does but the attacker is still capable of brute-forcing the 16-bit source port value, a specially-crafted DNS response sent to devices using uClibc could trigger a DNS poisoning attack.
DNS poisoning is practically tricking the target device into pointing to an arbitrarily defined endpoint and engaging in network communications with it.
By doing that, the attacker would be able to reroute the traffic to a server under their direct control.
"The attacker could then steal or manipulate information transmitted by users and perform other attacks against those devices to completely compromise them. The main issue here is how DNS poisoning attacks can force an authenticated response," - Nozomi Networks
Mitigation and fixing
Nozomi discovered the flaw in September 2021 and informed CISA about it. Then, in December, it reported to the CERT Coordination Center, and finally, in January 2022, it disclosed the vulnerability to over 200 potentially impacted vendors.
As mentioned above, there's currently no fix available for the flaw, which is now tracked under ICS-VU-638779 and VU#473698 (no CVE yet).
Currently, all stakeholders are coordinating to develop a viable patch and the community is expected to play a pivotal role in this, as this was precisely the purpose of the disclosure.
As the affected vendors will have to apply the patch by implementing the new uClibc version on firmware updates, it will take a while for the fixes to reach end consumers.
Even then, end-users will have to apply the firmware updates on their devices, which is another choke point that causes delays in fixing critical security flaws.
"Because this vulnerability remains unpatched, for the safety of the community, we cannot disclose the specific devices we tested on," says Nozomi
"We can, however, disclose that they were a range of well-known IoT devices running the latest firmware versions with a high chance of them being deployed throughout all critical infrastructure."
Users of IoT and router devices should keep an eye on new firmware releases from vendors and apply the latest updates as soon as they become available.
Unpatched DNS bug affects millions of routers and IoT devices
- aum
-

 1
1


3175x175(CURRENT).thumb.jpg.b05acc060982b36f5891ba728e6d953c.jpg)
Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.