Ukraine's premier law enforcement and counterintelligence agency on Thursday disclosed the real identities of five individuals allegedly involved in cyberattacks attributed to a cyber-espionage group named Gamaredon, linking the members to Russia's Federal Security Service (FSB).
Calling the hacker group "an FSB special project, which specifically targeted Ukraine," the Security Service of Ukraine (SSU) said the perpetrators "are officers of the 'Crimean' FSB and traitors who defected to the enemy during the occupation of the peninsula in 2014."
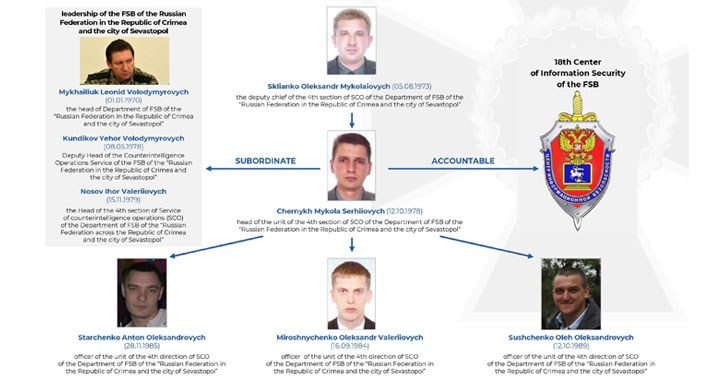
The names of the five individuals the SSU alleges are part of the covert operation are Sklianko Oleksandr Mykolaiovych, Chernykh Mykola Serhiiovych, Starchenko Anton Oleksandrovych, Miroshnychenko Oleksandr Valeriiovych, and Sushchenko Oleh Oleksandrovych.
Since its inception in 2013, the Russia-linked Gamaredon group (aka Primitive Bear, Armageddon, Winterflounder, or Iron Tilden) has been responsible for a number of malicious phishing campaigns, primarily aimed at Ukrainian institutions, with the goal of harvesting classified information from compromised Windows systems for geopolitical gains.
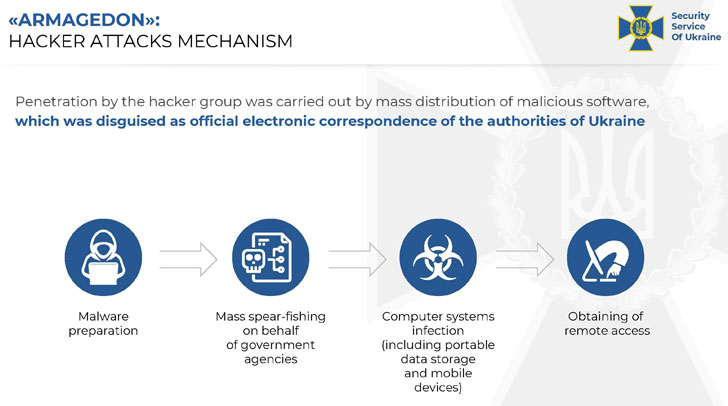
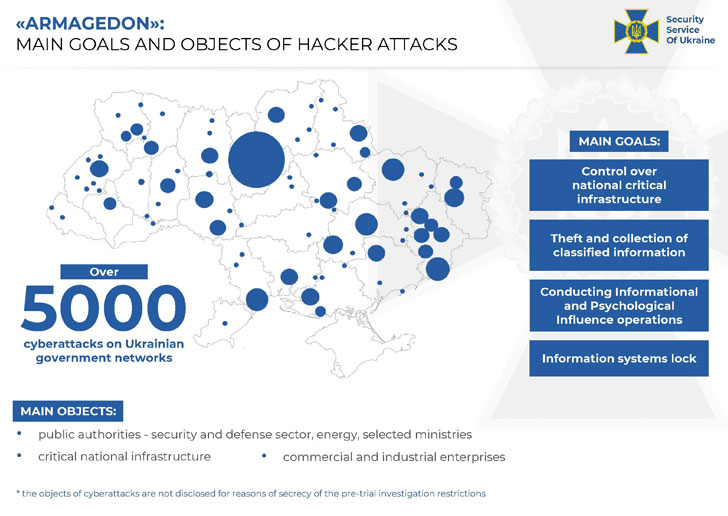
The threat actor is believed to have carried out no fewer than 5,000 cyberattacks against public authorities and critical infrastructure located in the country, and attempted to infect over 1,500 government computer systems, with most attacks directed at security, defense, and law enforcement agencies to obtain intelligence information.
"Contrary to other APT groups, the Gamaredon group seems to make no effort in trying to stay under the radar," Slovak cybersecurity firm ESET noted in an analysis published in June 2020. "Even though their tools have the capacity to download and execute arbitrary binaries that could be far stealthier, it seems that this group's main focus is to spread as far and fast as possible in their target's network while trying to exfiltrate data."
Besides its heavy reliance on social engineering tactics as an intrusion vector, Gamaredon is known to have invested in a range of tools for scything through organizations' defenses that are coded in a variety of programming languages such as VBScript, VBA Script, C#, C++, as well as using CMD, PowerShell, and .NET command shells.
"The group's activities are characterized by intrusiveness and audacity," the agency pointed out in a technical report.
Chief among its malware arsenal is a modular remote administration tool named Pterodo (aka Pteranodon) that comes with remote access capabilities, keystroke logging, the ability to take screenshots, access microphone, and also download additional modules from a remote server. Also put to use is a .NET-based file stealer that's designed to collect files with the following extensions: *.doc, *.docx, *.xls, *.rtf, *.odt, *.txt, *.jpg, and *.pdf.
A third tool concerns a malicious payload that's engineered to distribute the malware through connected removable media, in addition to collecting and siphoning data stored in those devices.
"The SSU is continuously taking steps to contain and neutralize Russia's cyber aggression against Ukraine," the agency said. "Established as a unit of the so-called 'FSB Office of Russia in the Republic of Crimea and the city of Sevastopol,' this group of individuals acted as an outpost […] from 2014 purposefully threatening the proper functioning of state bodies and critical infrastructure of Ukraine."
- Karlston and Mutton
-

 2
2


Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.