A massive, malicious campaign is underway using over 200 typosquatting domains that impersonate twenty-seven brands to trick visitors into downloading various Windows and Android malware.
Typosquatting is an old method of tricking people into visiting a fake website by registering a domain name similar to that used by genuine brands.
The domains used in this campaign are very close to the authentic ones, featuring a single letter position swap or an additional "s," making them easy for people to miss.
In terms of appearance, in most cases seen by BleepingComputer, the malicious websites are clones of the originals or at least convincing enough, so there's not much to give away the fraud.
Victims typically end up on these sites by mistyping the website name they want to visit in the browser's URL bar, which is not uncommon when typing on mobile.
However, users could also be led on these sites via phishing emails or SMS, direct messages, malicious social media and forum posts, and other ways.
A vast network of fake sites
Some of the malicious sites were discovered by cyber-intelligence firm Cyble, which published a report this week focusing on domains mimicking popular Android app stores like Google Play, APKCombo, and APKPure, as well as download portals for PayPal, VidMate, Snapchat, and TikTok.
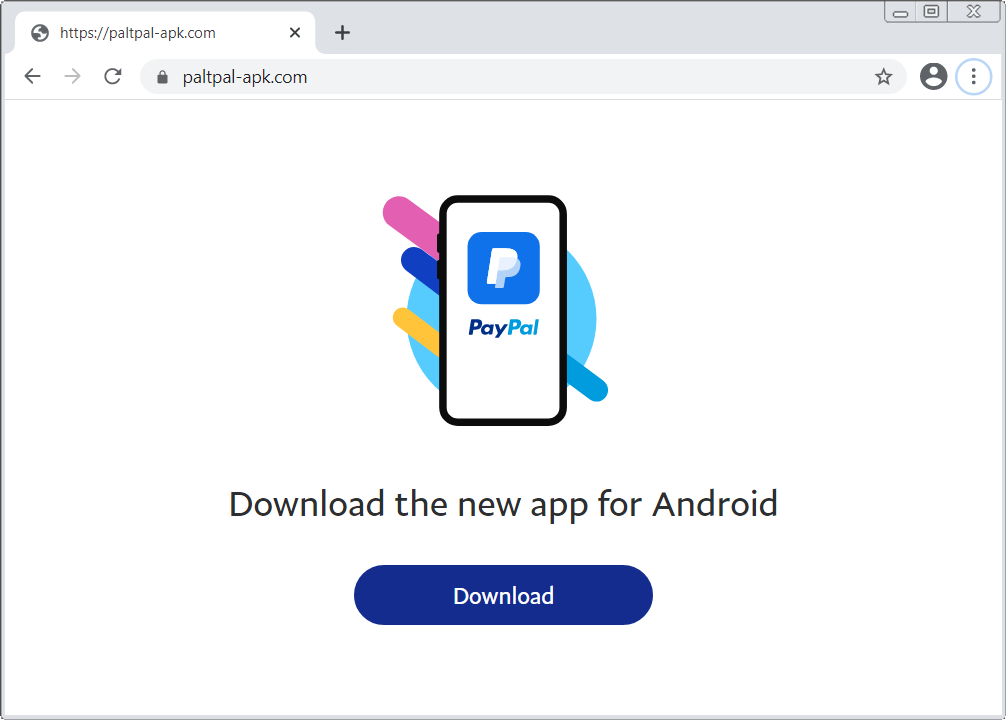
Malicious site impersonating PayPal
Some of the domains used for this purpose are:
- payce-google[.]com – impersonates Google Wallet
- snanpckat-apk[.]com – impersonates Snapchat
- vidmates-app[.]com – impersonates VidMate
- paltpal-apk[.]com – impersonates PayPal
- m-apkpures[.]com – impersonates APKPure
- tlktok-apk[.]link – impersonates download portal for TikTok app
In all these cases, the malware delivered to users attempting to download the APKs is ERMAC, a banking trojan targeting banking accounts and cryptocurrency wallets from 467 apps.
Part of a much larger campaign
While Cyble's report focused on the campaign's Android malware, BleepingComputer found a much larger typosquatting campaign from the same operators, distributing Windows malware.
This campaign consists of over 90 websites created to impersonate over twenty-seven popular brands to distribute Windows malware, steal cryptocurrency recovery keys, and, as described above, push Android malware.
| Category | Impersonated Brands |
| Mobile Apps & Services |
TikTok Vidmate SnapChat Paypal APK Pure APKCombo Google Wallet |
| Software |
Microsoft Visual Studio Brave Browser ThunderBird Notepad+ Tor Browser |
| Cryptocurrency |
TronLink MetaMask Phantom Cosmos Wallet Mintable Ethermine GenoPets |
| Crypto and Stock trading |
Trading View IQ Option NinjaTrader Tiger.Trade |
| Web sites |
Figma Quatro Casinos Big Time CS:Money |
A notable example of one of these typosquat sites is for the very popular Notepad++ text editor. This fake site uses the domain "notepads-plus-plus[.]org", which is only a character away from the authentic at "notepad-plus-plus.org".
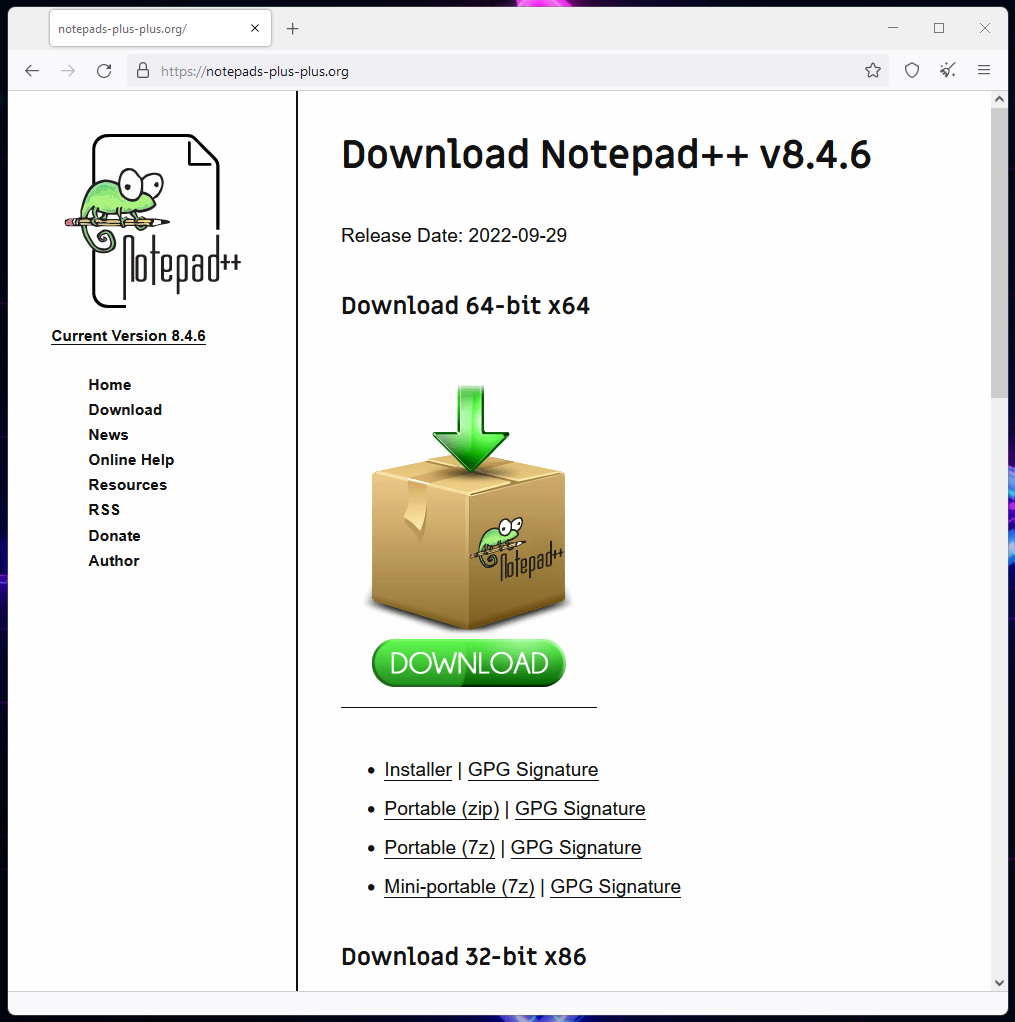
Fake Notepad++ site delivering Vidar Stealer
The files from this site install the Vidar Stealer information-stealing malware, which has had its size inflated to 700MB to evade analysis.
Another site discovered by BleepingComputer impersonates the Tor Project using the "tocproject.com" domain. In this case, the website drops the Agent Tesla keylogger and RAT.
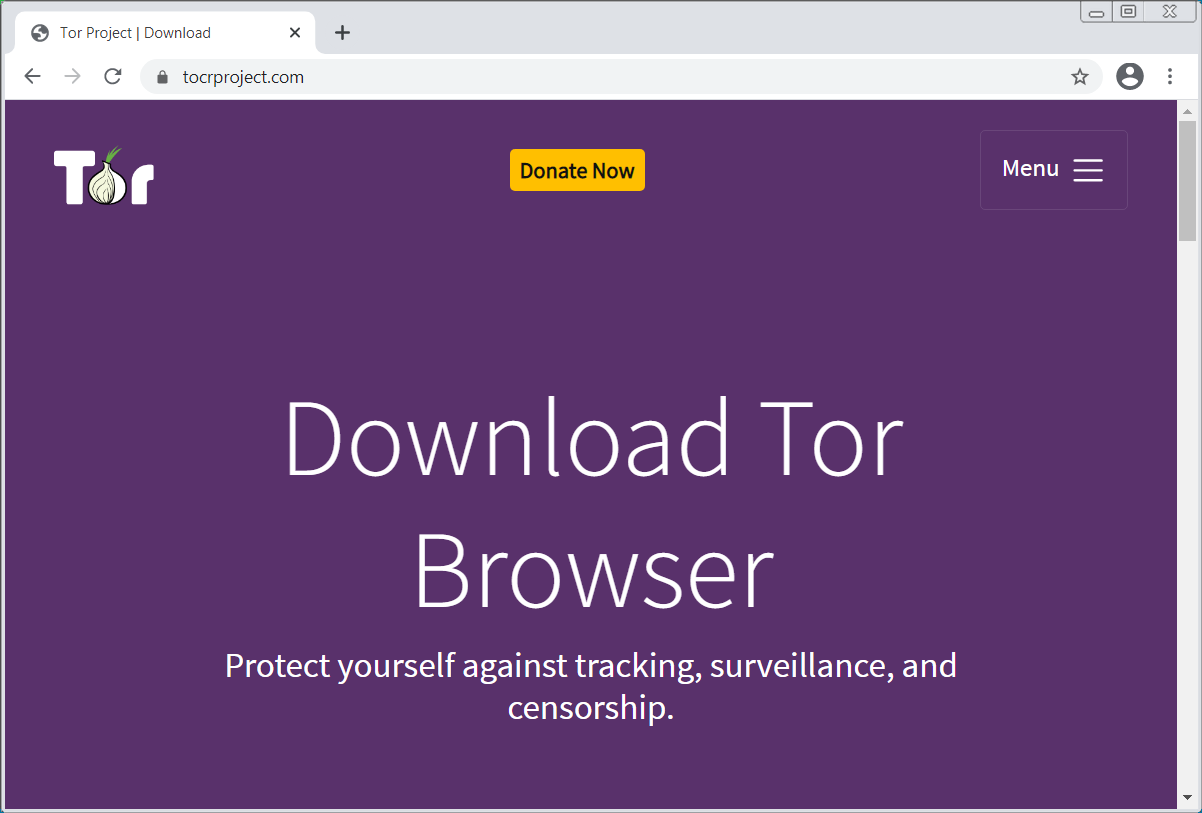
Fake Tor site dropping Agent Tesla
By digging deeper into the long list of the domains, we've found several targeting popular software like:
- thundersbird[.]org – Impersonates the popular Thunderbird open-source email suite, dropping Vidar Stealer
- codevisualstudio[.]org – Impersonates Microsoft’s Visual Studio Code to drop Vidar
- braves-browsers[.]org – Impersonates the Brave web browser to drop Vidar
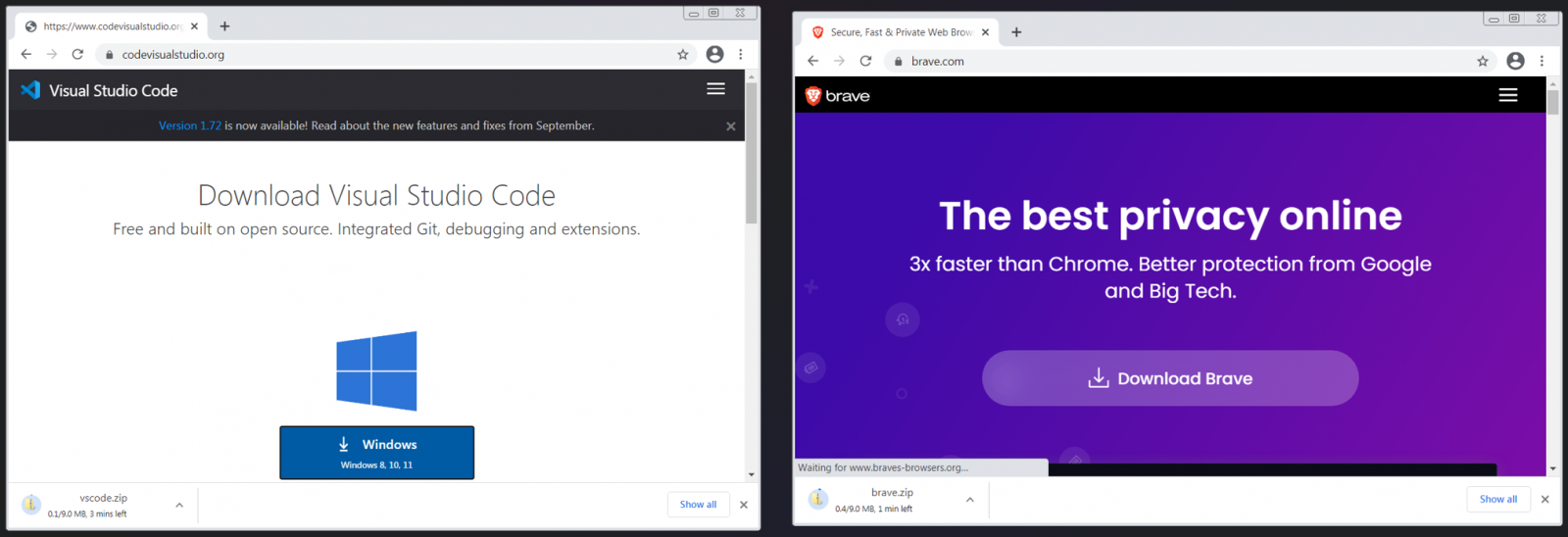
More fake sites dropping Windows malware
The variety in the malware families delivered to victims may indicate that the campaign operators experiment with various strains to see what works best.
Another portion of these sites target cryptocurrency wallets and seed phrases, a very profitable activity for threat actors.
For example, BleepingComputer found "ethersmine[.]com", which attempts to steal the visitor's Ethereum wallet seed phrase.
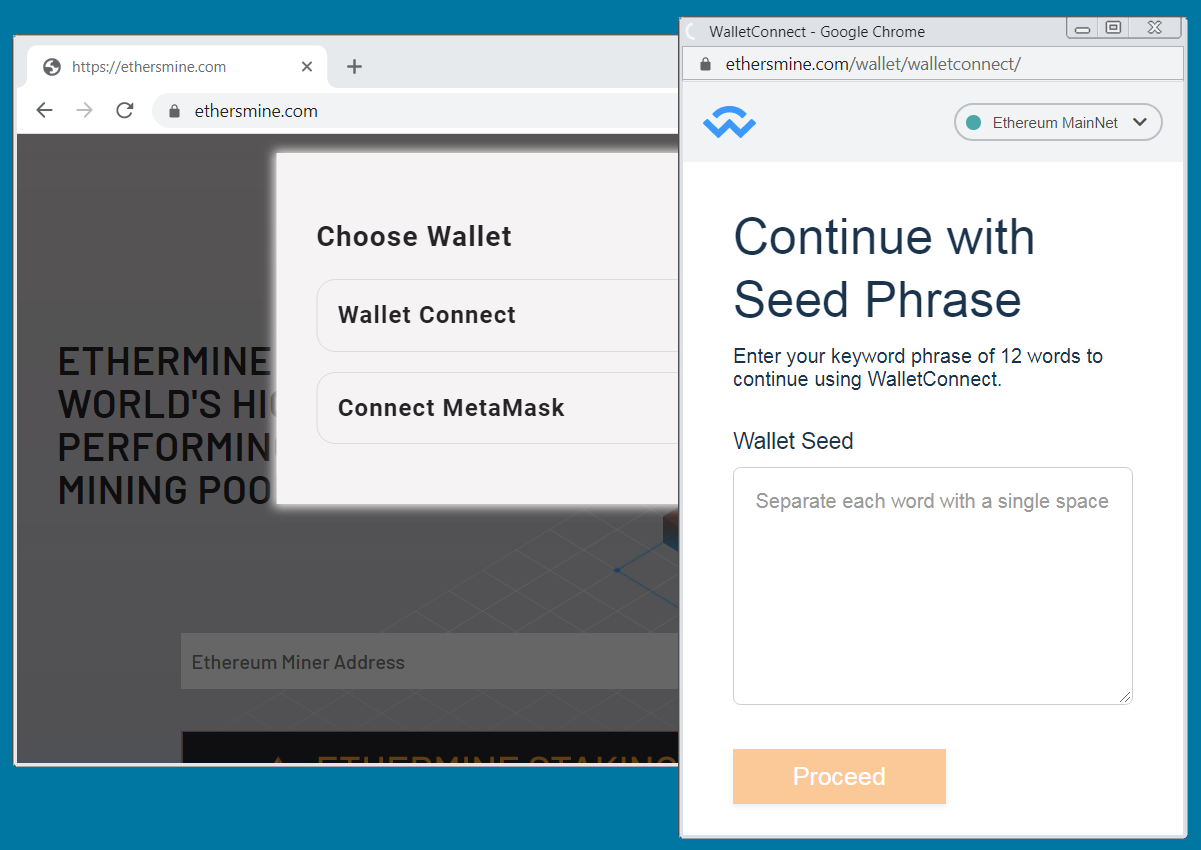
Site impersonating the Ethermine mining pool
Other sites in the campaign target cryptocurrency holders and digital asset investors impersonating popular crypto wallets, trading apps, and NFT sites.
Of course, the threat actors use multiple variants of each domain to cover as many mistypes as possible, so these domains are only a small sample of the entire network of domains used in the campaign.
Some browsers like Google Chrome and Microsoft Edge include typosquatting protection. However, in our tests, the browsers did not block any of the domains we tested.
To protect yourself from typosquatting domains, the best method to find a legitimate site is to search for a particular brand in a search engine.
However, you should avoid clicking on ads shown in search results, as there have been many cases where malicious ads are created to impersonate a real site.
- Lexionline
-

 1
1




Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.