Let’s say you’re a large company that has just shipped an employee a brand-new replacement laptop. And let’s say it comes preconfigured to use all the latest best security practices, including full-disk encryption using a trusted platform module, password-protected BIOS settings, UEFI SecureBoot, and virtually all other recommendations from the National Security Agency and NIST for locking down federal computer systems. And let’s say an attacker manages to intercept the machine. Can the attacker use it to hack your network?
Research published last week shows the answer is a resounding yes. Not only that, but a hacker who has done her homework needs a surprisingly short stretch of time alone with the machine to carry out the attack. With that, the hacker can gain the ability to write not only to the stolen laptop, but to the fortified network it was configured to connect to.
Researchers at the security consultancy Dolos Group, hired to test the security of one client’s network, received a new Lenovo computer preconfigured to use the standard security stack for the organization. They received no test credentials, configuration details, or other information about the machine. An analysis of the BIOS settings, boot operation, and hardware quickly revealed that the security measures in place were going to preclude the usual hacks, including:
- pcileech/DMA attacks because Intel’s VT-d BIOS protection was enabled
- Authentication bypasses using tools such as Kon-boot
- Use of tools such as LAN turtle, Responder to exfiltrate data from USB ethernet adapters
Fort Knox and the not-so-armored car
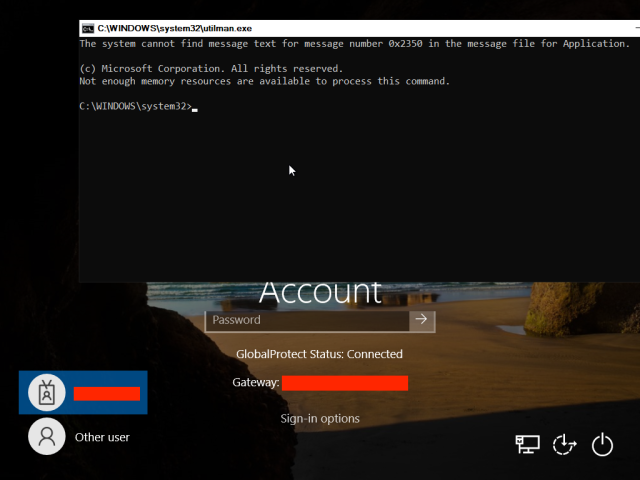
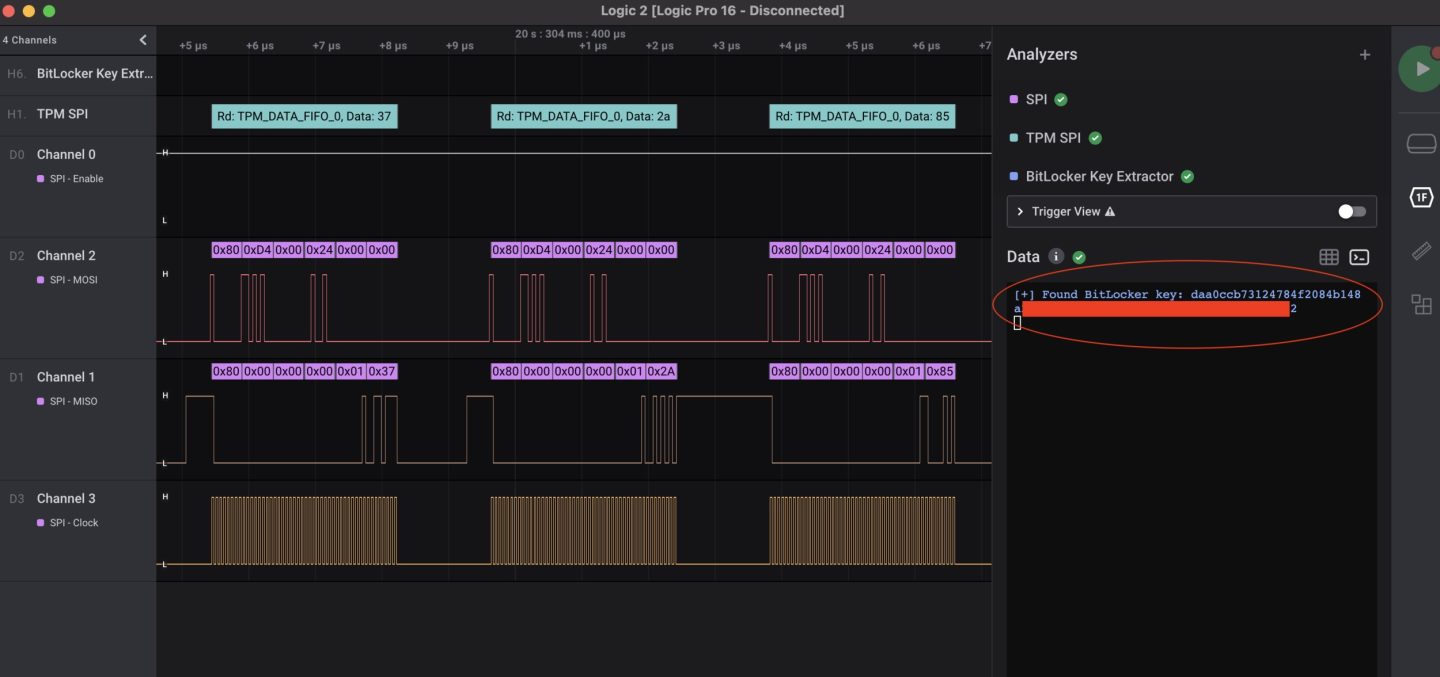
With little else to go on, the researchers focused on the trusted platform module, or TPM, a heavily fortified chip installed on the motherboard that communicates directly with other hardware installed on the machine. The researchers noticed that, as is the default for disk encryption using Microsoft’s BitLocker, the laptop booted directly to the Windows screen, with no prompt for entering a PIN or password. That meant that the TPM was where the sole cryptographic secret for unlocking the drive was stored.
Microsoft recommends overriding the default and using a PIN or password only for threat models that anticipate an attacker with enough skill and time alone with an unattended target machine to open the case and solder motherboard devices. After completing their analysis, the researchers said that the Microsoft advice is inadequate because it opens devices to attacks that can be performed by abusive spouses, malicious insiders, or other people who have fleeting private access.
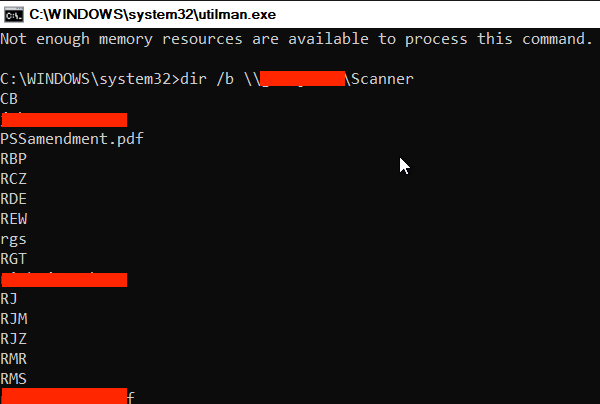
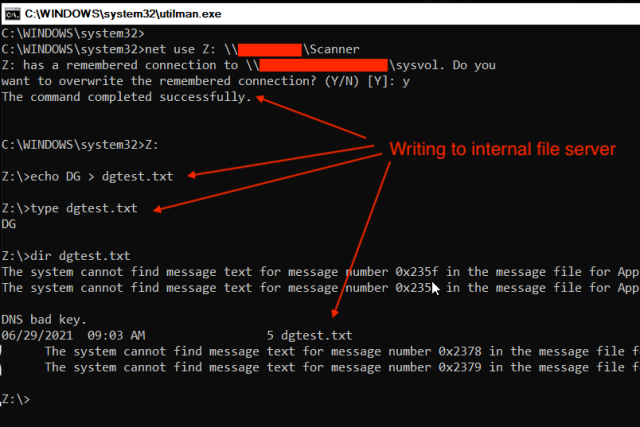
“A pre-equipped attacker can perform this entire attack chain in less than 30 minutes with no soldering, simple and relatively cheap hardware, and publicly available tools,” the Dolos Group researchers wrote in a post, “a process that places it squarely into Evil-Maid territory.”
TPMs have multiple layers of defenses that prevent attackers from extracting or tampering with the data they store. For instance, an analysis more than 10 years ago by reverse-engineer Christopher revealed that a TPM chip made by Infineon was designed to self-destruct in the event it was physically penetrated. Optical sensors, for instance, detected ambient light from luminous sources. And a wire mesh that covered the microcontroller was aimed at disabling the chip should any of its electrical circuits be disturbed.
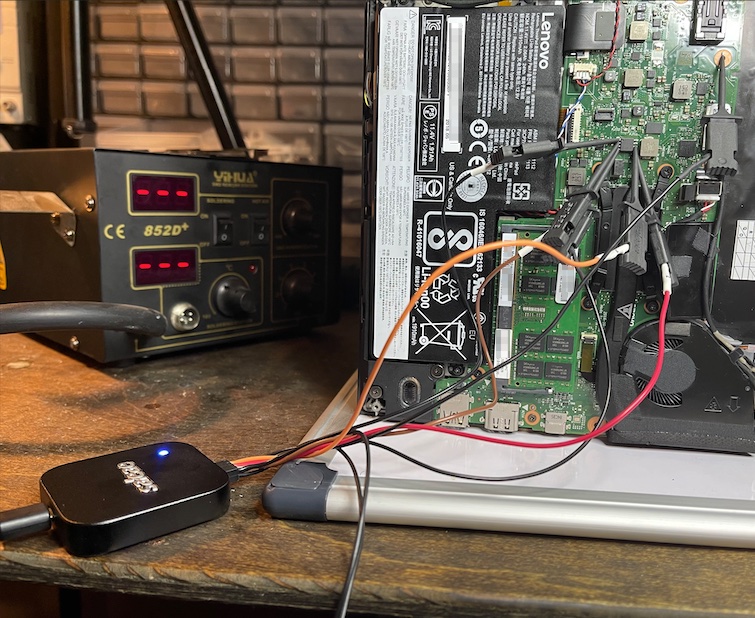
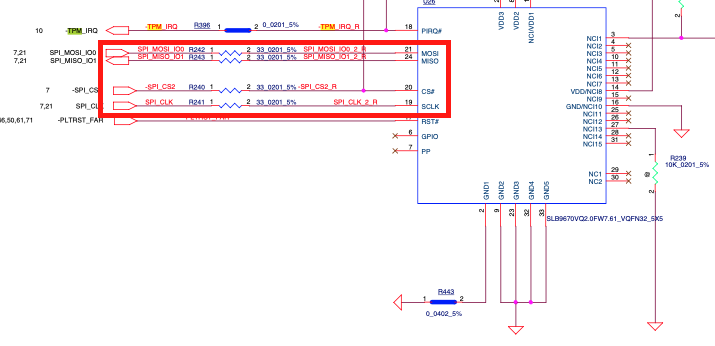
With little hope of cracking the chip inside the Lenovo laptop, the Dolos researchers sought other ways they might be able to extract the key that decrypted the hard drive. They noticed that the TPM communicated with the CPU using serial peripheral interface, a communications protocol for embedded systems.
Abbreviated as SPI, the firmware provides no encryption capabilities of its own, so any encryption must be handled by the devices the TPM is communicating with. Microsoft’s BitLocker, meanwhile, doesn’t use any of the encrypted communications features of the latest TPM standard. That meant if the researchers could tap into the connection between the TPM and the CPU, they might be able to extract the key.
They wrote:
Getting around the TPM in this manner is akin to ignoring Fort Knox and focusing on the not-so-armored car coming out of it.
In order to sniff the data moving over the SPI bus, we must attach leads or probes to the pins (labeled above as MOSI, MISO, CS, and CLK) on the TPM. Normally that is simple but there is a practical problem in this case. This TPM is on a VQFN32 footprint, which is very tiny. The “pins” are actually only 0.25mm wide and spaced 0.5mm apart. And those “pins” aren’t actually pins, they are flat against the wall of the chip so it’s physically impossible to attach any sort of clip. You could solder “fly leads” to the solder pads but that’s a hassle and tends to be a very physically unstable connection. Alternatively a common tactic is to locate in-series resistors to solder to, but they were just as small, and even more fragile. This was not going to be easy.
But before we got started we figured there might be another way. Many times SPI chips share the same “bus” with other SPI chips. It’s a technique hardware designers use to make connections simpler, save on cost, and make troubleshooting/programming easier. We started looking throughout the board for any other chip that might be on the same bus as the TPM. Maybe their pins would be larger and easier to use. After some probing and consulting the schematics, it turned out that the TPM shared a SPI bus with a single other chip, the CMOS chip, which definitely had larger pins. In fact, the CMOS chip had just about the largest pin size you can find on standard motherboards, it was a SOP-8 (aka SOIC-8).



3175x175(CURRENT).thumb.jpg.b05acc060982b36f5891ba728e6d953c.jpg)





Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.