A surge of trojanized Tor Browser installers targets Russians and Eastern Europeans with clipboard-hijacking malware that steals infected users' cryptocurrency transactions.
Kaspersky analysts warn that while this attack is not new or particularly creative, it's still effective and prevalent, infecting many users worldwide.
While these malicious Tor installers target countries worldwide, Kaspersky says that most are targeting Russia and Eastern Europe.
"We relate this to the ban of Tor Project's website in Russia at the end of 2021, which was reported by the Tor Project itself," explains Kaspersky.
"According to the latter, Russia was the second largest country by number of Tor users in 2021 (with over 300,000 daily users, or 15% of all Tor users)."
Malicious Tor Browser installers
Tor Browser is a specialized web browser that allows users to browse the web anonymously by hiding their IP address and encrypting their traffic.
Tor may also be used for accessing special onion domains, otherwise known as the "dark web," which are not indexed by standard search engines or accessible through regular browsers.
Cryptocurrency holders may use the Tor browser either to enhance their privacy and anonymity while transacting with cryptocurrencies or because they want to access illegal dark web market services, which are paid in crypto.
Trojanized Tor installations are typically promoted as "security-strengthened" versions of the official vendor, Tor Project, or pushed to users in countries where Tor is prohibited, making it harder to download the official version.
Kaspersky says that these installers contain a standard version of the Tor browser, albeit outdated in most cases, along with an extra executable hidden inside a password-protected RAR archive set to self-extract on the user's system.
The installers are also localized with names like 'torbrowser_ru.exe,' and contain language packs allowing users to select their preferred language.
Malicious Tor Browser language pack
Source: Kaspersky
While the standard Tor browser is launched in the foreground, the archive extracts the malware in the background and runs it as a new process while also registering it on the system autostart. Additionally, the malware uses a uTorrent icon to hide on the breached system.
.jpg)
Trojanized Tor infection diagram
Source: Kaspersky
Kaspersky has detected 16,000 variants of these Tor installers between August 2022 and February 2023 in 52 countries, based on data from users of its security products.
While the majority are targeting Russia and Eastern Europe, they have also been seen targeting the United States, Germany, China, France, the Netherlands, and the UK.
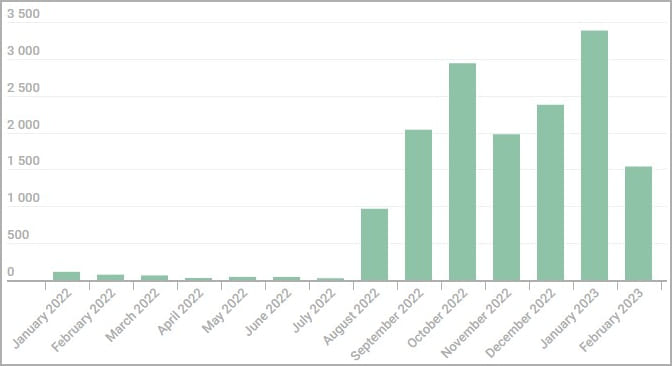
Number of monthly infections detected by Kaspersky
Source: Kaspersky
Clipboard hijacking
As cryptocurrency addresses are long and complicated to type, it is common to copy them first to the clipboard and then paste them into another program or website.
The malware monitors the clipboard for recognizable crypto wallet addresses using regular expressions, and when one is detected, replaces it with an associated cryptocurrency address owned by the threat actors.
When the user pastes the cryptocurrency address, the threat actor's address will be pasted instead, allowing the attackers to steal the sent transaction.
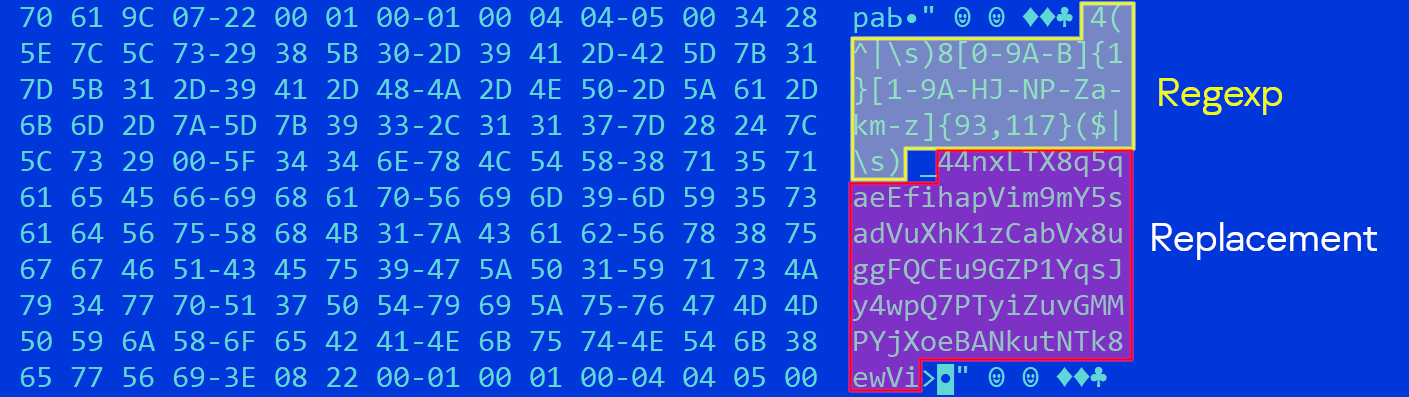
Regex detecting a wallet address and replacing it
Source: Kaspersky
Kaspersky says the threat actor uses thousands of addresses on each malware sample, selected randomly from a hardcoded list. This makes wallet tracking, reporting, and banning hard.
The cybersecurity company unpacked hundreds of malware samples it had collected to extract the replacement addresses and found that they stole almost $400,000, excluding Monero, which cannot be traced.
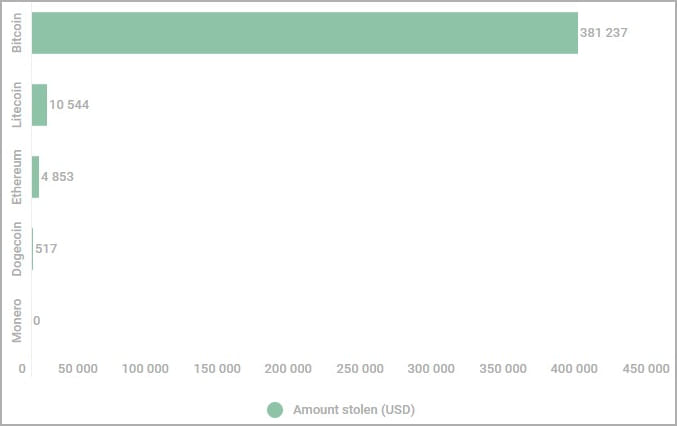
Confirmed stolen amounts
Source: Kaspersky
This is the money stolen only from a single campaign operated by a specific malware author, and there are almost certainly other campaigns using trojanized installers for different software.
To stay safe from clipboard hijackers, only install software from trustworthy/official sources, in this case, the Tor Project website.
A simple test to check if a clipper has infected you is to copy and paste this address to your Notepad: bc1heymalwarehowaboutyoureplacethisaddress.
If it is changed, it means your system is compromised.




Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.