A previously unnamed ransomware has rebranded under the name 'Trigona,' launching a new Tor negotiation site where they accept Monero as ransom payments.
Trigona has been active for some time, with samples seen at the beginning of the year. However, those samples utilized email for negotiations and were not branded under a specific name.
As discovered by MalwareHunterTeam, starting in late October 2022, the ransomware operation launched a new Tor negotiation site where they officially named themselves 'Trigona.'
As Trigona is the name of a family of large stingless bees, the ransomware operation has adopted a logo showing a person in a cyber bee-like costume, shown below.

Trigona ransomware operation's logo
Source: BleepingComputer
BleepingComputer is aware of numerous victims of the new ransomware operation, including a real estate company and what appears to be a village in Germany.
The Trigona Ransomware
BleepingComputer analyzed a recent sample of Trigona and found it supports various command line arguments that determine whether local or network files are encrypted, if a Windows autorun key is added, and whether a test victim ID (VID) or campaign ID (CID) should be used.
The command line arguments are listed below:
/full
/!autorun
/test_cid
/test_vid
/path
/!local
/!lan
/autorun_only
When encrypting files, Trigona will encrypt all files on a device except those in specific folders, such as the Windows and Program Files folders. In addition, the ransomware will rename encrypted files to use the ._locked extension.
For example, the file 1.doc would be encrypted and renamed to 1.doc._locked, as shown below.
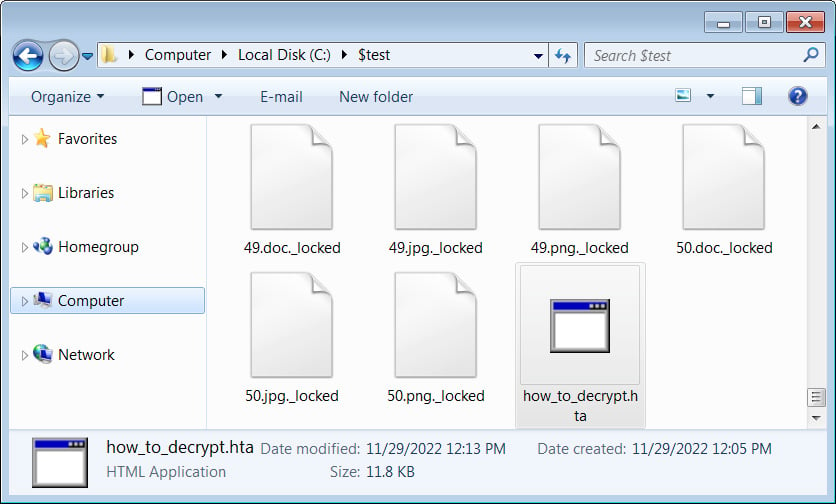
Files encrypted by Trigona
Source: BleepingComputer
The ransomware will also embed the encrypted decryption key, the campaign ID, and the victim ID (company name) in the encrypted files.
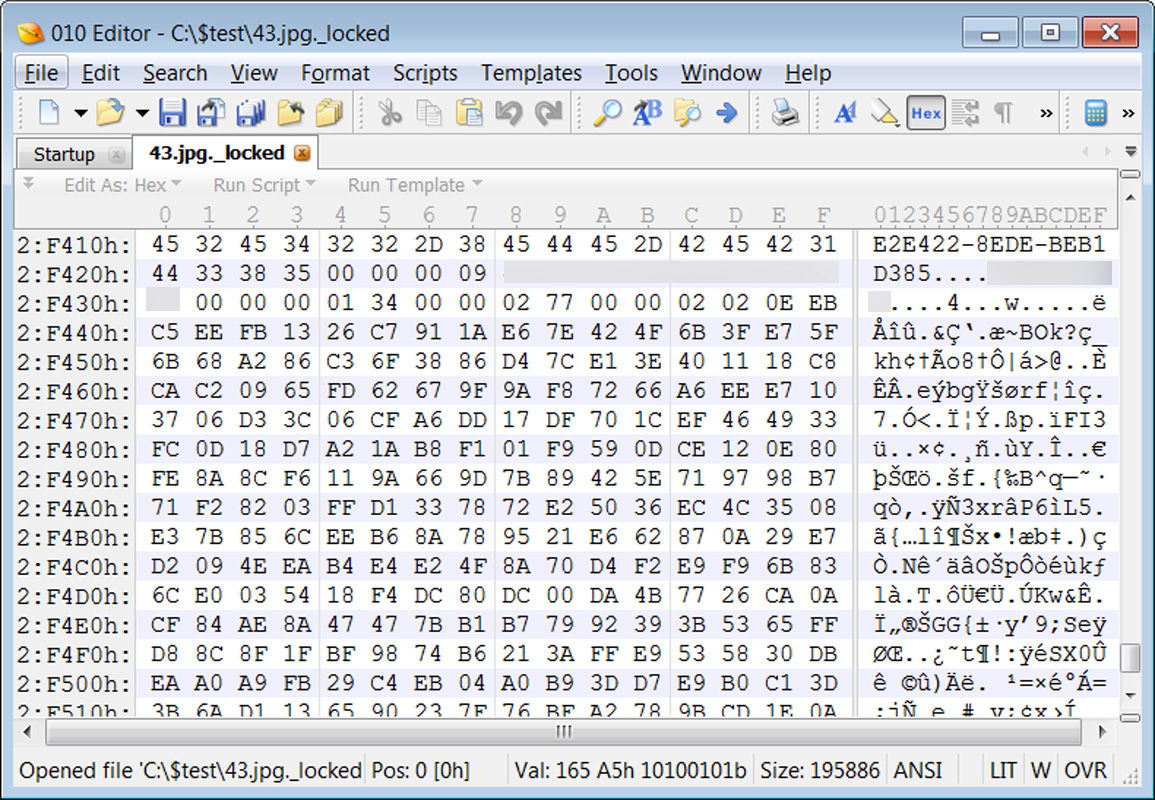
Encrypted file with file markers
Source: BleepingComputer
A ransom note named how_to_decrypt.hta will be created in each scanned folder. This note displays information about the attack, a link to the Tor negotiation site, and a link that copies an authorization key into the Windows clipboard needed to log in to the Tor negotiation site.
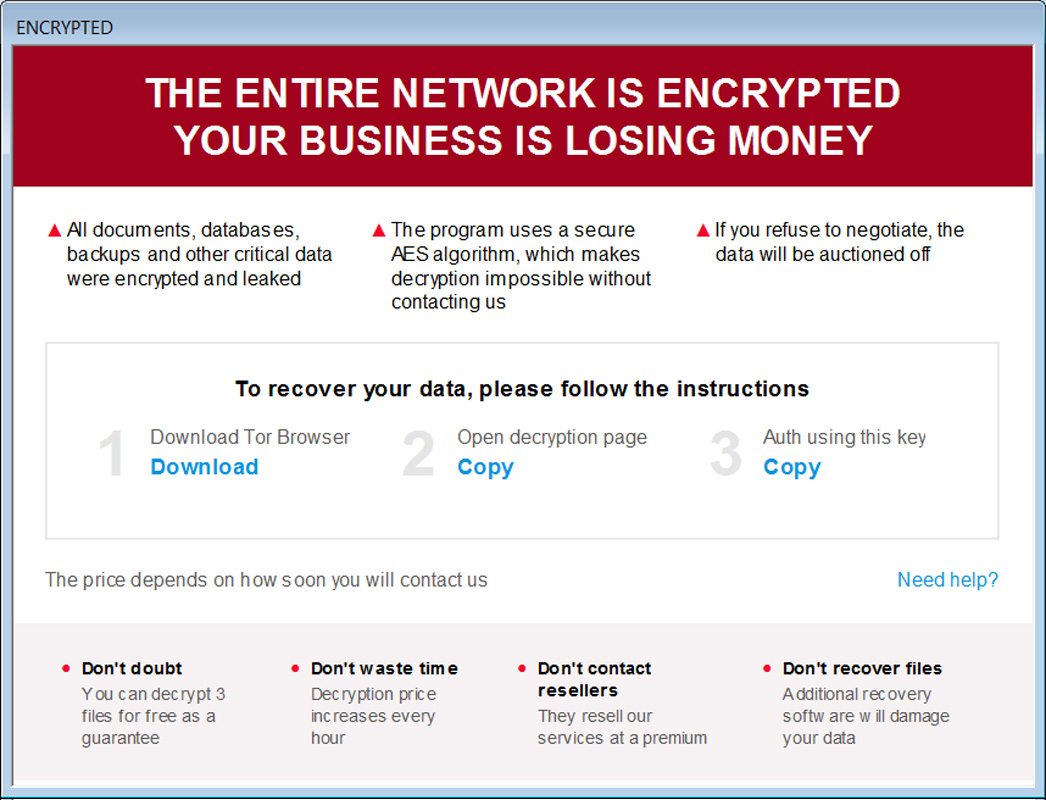
Trigona ransom note
Source: BleepingComputer
After logging into the Tor site, the victim will be shown information on how to buy Monero to pay a ransom and a support chat that they can use to negotiate with the threat actors. The site also offers the ability to decrypt five files, up to 5MB each, for free.
BleepingComputer has not seen any active negotiations, and it is not known how much money the threat actors are demanding from victims.
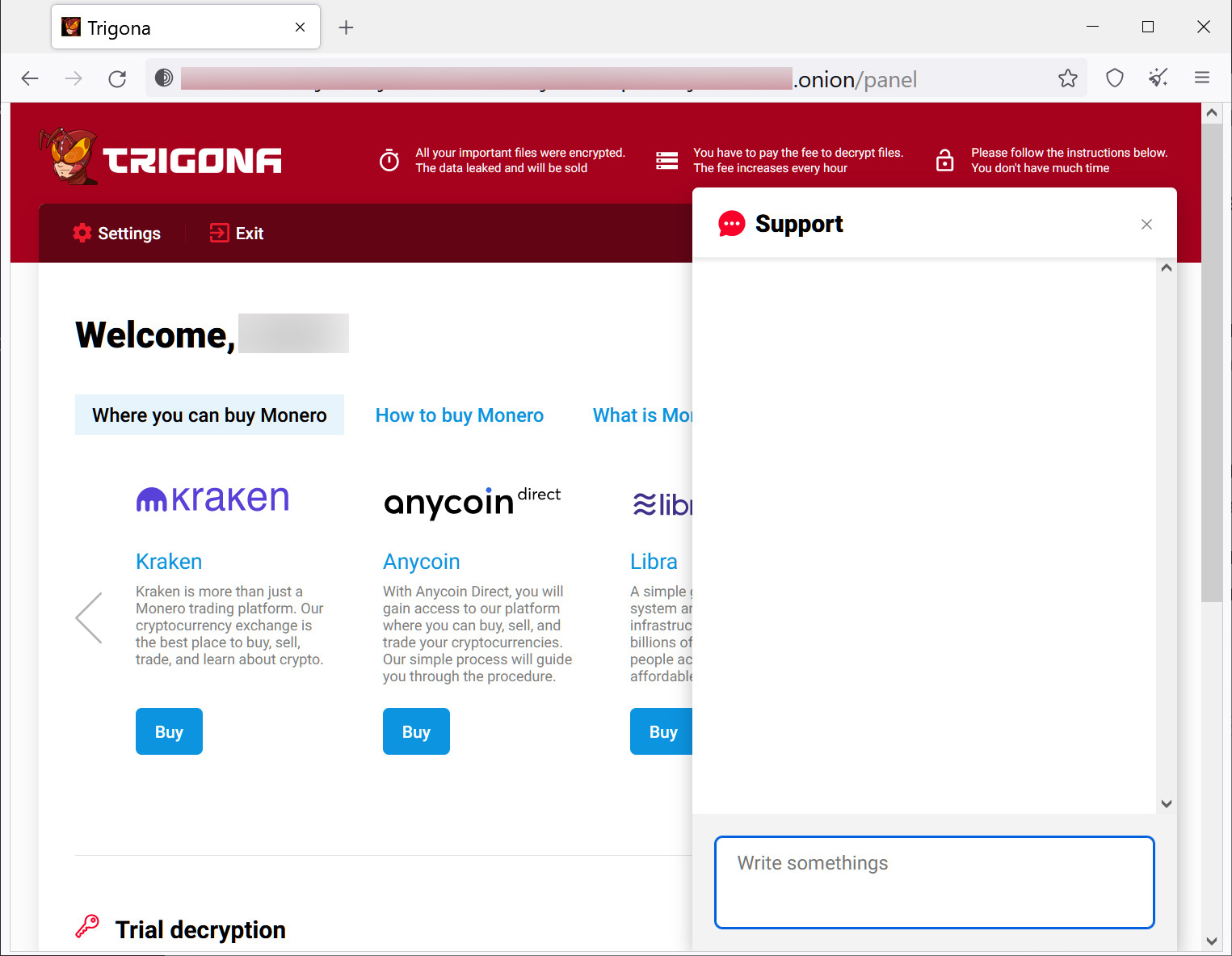
Trigona Tor negotiation site
Source: BleepingComputer
When a ransom is paid, the victims will receive a link to a decryptor and a keys.dat file, which contains the private decryption key.
The decryptor allows you to decrypt individual files or folders on the local device and network shares.
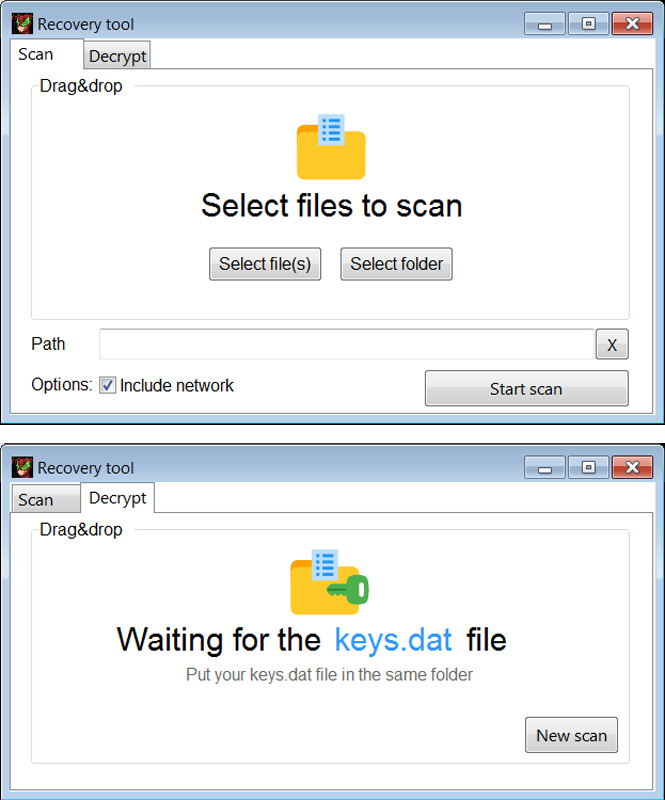
Scan and decrypt screens of the Trigona decryptor
Source: BleepingComputer
It is unclear how the operation breaches networks or deploy ransomware. Furthermore, while their ransom notes claim they steal data during attacks, BleepingComputer has not seen any proof of this.
However, their attacks have been increasing worldwide, and with the investment into a dedicated Tor platform, they will likely continue to expand their operations.
- Karlston
-

 1
1




Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.