TrickBot Botnet Found Deploying A New Ransomware Called Diavol
Threat actors behind the infamous TrickBot malware have been linked to a new ransomware strain named "Diavol," according to the latest research.
Diavol and Conti ransomware payloads were deployed on different systems in a case of an unsuccessful attack targeting one of its customers earlier this month, researchers from Fortinet's FortiGuard Labs said last week.
TrickBot, a banking Trojan first detected in 2016, has been traditionally a Windows-based crimeware solution, employing different modules to perform a wide range of malicious activities on target networks, including credential theft and conduct ransomware attacks.
Despite efforts by law enforcement to neutralize the bot network, the ever-evolving malware has proven to be a resilient threat, what with the Russia-based operators — dubbed "Wizard Spider" — quickly adapting new tools to carry out further attacks.
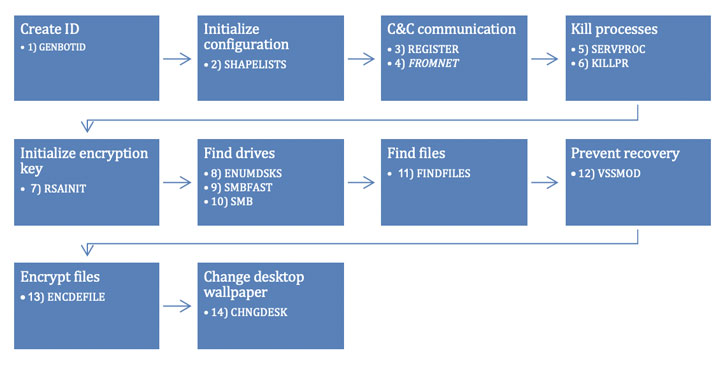
Diavol is said to have been deployed in the wild in one incident to date. The source of intrusion remains unknown as yet. What's clear, though, is that the payload's source code shares similarities with that of Conti, even as its ransom note has been found to reuse some language from Egregor ransomware.
"As part of a rather unique encryption procedure, Diavol operates using user-mode Asynchronous Procedure Calls (APCs) without a symmetric encryption algorithm," the researchers said. "Usually, ransomware authors aim to complete the encryption operation in the shortest amount of time. Asymmetric encryption algorithms are not the obvious choice as they [are] significantly slower than symmetric algorithms."
Another aspect of the ransomware that stands out is its reliance on an anti-analysis technique to obfuscate its code in the form of bitmap images, from where the routines are loaded into a buffer with execute permissions.
Prior to locking files and changing the desktop wallpaper with a ransom message, some of the major functions carried out by Diavol include registering the victim device with a remote server, terminating running processes, finding local drives and files in the system to encrypt, and preventing recovery by deleting shadow copies.
Wizard Spider's nascent ransomware effort also coincides with "new developments to the TrickBot webinject module," as detailed by Kryptos Logic Threat Intelligence team, indicating that the financially motivated cybercrime group is still actively retooling its malware arsenal.
"TrickBot has brought back their bank fraud module, which has been updated to support Zeus-style webinjects," cybersecurity researcher Marcus Hutchins tweeted. "This could suggest they are resuming their bank fraud operation, and plan to expand access to those unfamiliar with their internal webinject format."
- Karlston
-

 1
1



Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.