On October 7th, Toyota revealed a partial copy of their T-Connect source code had been accidentally exposed for 5 years, including access to data for over 290,000 customers.
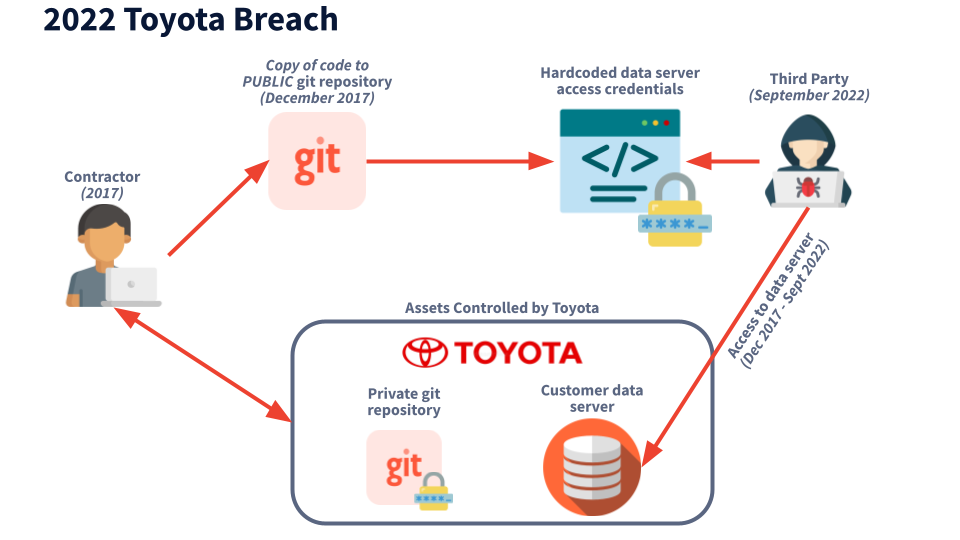
On October 7, 2022 Toyota, the Japanese-based automotive manufacturer, revealed they had accidentally exposed a credential allowing access to customer data in a public GitHub repo for nearly 5 years. The code was made public from December 2017 through September 2022. While Toyota says they have invalidated the key, any exposure this long could mean multiple malicious actors had already acquired access.
This incident adds Toyota to the list of companies that have had similar exposures; a list that includes Samsung, Nvidia, and Twitch, just to name a few. While this breach at Toyota is currently understood as fairly limited, compared to the 6,695 secrets exposed in the Samsung case, the growing number of companies experiencing such issues is still a very disturbing trend.
Data exposures on public Git repositories are a particularly troubling topic. Code intended for tightly controlled private repos are very often pushed to public repos owned by employees or contractors, outside the security control of their GitHub organizations.
What Happened
Toyota Data Breach Graphic
T-Connect
In 2014, Toyota introduced a new telematics service called T-Connect to customers, offering interactive voice response and allowing drivers to connect to third-party apps. Toyota advertises it as their “connected services that provide safe, secure, comfortable, and convenient services through vehicle communication.”
T-Connect enables features like remote starting, in-car Wi-Fi, digital key access, full control over dashboard-provided metrics, as well as a direct line to the My Toyota service app. The servers that control these options contain unique customer identification numbers and customer emails.
A Subcontractor And A Public Repo
In December 2017, while working with an unnamed (so far) subcontractor, a portion of the source code for T-Connect was uploaded to a public GitHub repository. Inside the repo there was a hardcoded access key for the data server that manages customer info. Anyone who found that credential could access the server, gaining access for 296,019 customers.
It was not until September 15, 2022, that anyone noticed this repo was public and that customer data was potentially exposed. Toyota has since made the repo private and has invalidated and replaced any affected connection credentials.
How Bad Is this Security Breach?
While customer identification numbers and emails have potentially been exposed, customer names, credit card data, and phone numbers were not stored in the exposed database, and are therefore not at risk. Toyota has begun outreach to affected customers. As part of this outreach, the company has set up a special form on its site to let customers check to see if their data was part of the exposure.
As of now, there is no sign that this breach would allow bad actors to do more than just harvest emails and the associated customer management numbers. Toyota has not been able to confirm any abuse or attacks have occurred using harvested data.
How can people protect themselves
Toyota does warn customers that although there has not been any unauthorized use of their personal information detected, all affected users should be on the lookout for spam emails and phishing attacks.
The notice from Toyota states: “If you receive a suspicious e-mail with an unknown sender or subject, there is a risk of virus infection or unauthorized access, so please do not open the file attached to the e-mail and delete the e-mail itself immediately.”
This incident serves as a good reminder that with all emails it is important to only follow links in emails from trusted sources. When in doubt about the validity of an email, you should inspect the header to make sure the email domain is legitimate and use the hover preview for any link to ensure the URL is not redirecting you to a potentially dangerous site.
Attackers can use context along with stolen emails to create more convincing phishing campaigns. For example, knowing they are a Toyota customer can make them appear more trustworthy.
How can devs prevent this from happening again?
There are two security missteps at the heart of this latest incident at Toyota:
- Code intended to be private was pushed to a public repository.
- A credential for a DB server holding customer data was hardcoded into the repo.
Git is an awesome version control system, used by over 93% of developers, and is at the heart of modern CI/CD pipelines. One of the benefits of Git is that everyone has a complete copy of the project they are working on. That full copy access also means each developer can, in turn, push their copy to unauthorized places, such as public repositories. While it might not be possible to prevent a contractor from pushing code wherever they want, it is possible to detect when code or IP has been pushed somewhere it should not be. This is a serious issue affecting the software industry that we have previously reported on.
GitGuardian has made available a free tool, HasMyCodeLeaked, to help companies identify potential source code leaks. Our free tool can perform an exact lookup of code "fingerprints" in GitHub's public history, helping you quickly identify repositories that contain private code or data.
Hardcoding secrets is a serious issue affecting the software industry today. In 2021, we discovered over 6 Million secrets in public GitHub repos alone. As security in DevOps ‘shifts left’ on the shoulders of developers pressed for time, it is critical that they leverage tools and services that prevent secrets from ending up as parts of their repos. A company’s secrets that get hardcoded can be exposed in a number of ways, including pushed to public repos, but also if the code is leaked by a disgruntled employee or stolen by a malicious actor. This is a real blind spot for companies that do not have secrets detection in place.
- Karlston
-

 1
1



Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.