Researchers detail an attack technique combining thermal imaging and AI - and warn that increased access to innovative technologies will be abused by cyber criminals.
Computer security researchers say they've developed an AI-driven system that can guess computer and smartphone passwords in seconds by examining the heat signatures that fingertips leave on keyboards and screens when entering data.
Called ThermoSecure, researchers at the University of Glasgow's School of Computing Science developed the system to show how the falling price of thermal-imaging cameras and increasing access to machine-learning and artificial intelligence (AI) algorithms are creating new opportunities for what they describe as thermal attacks.
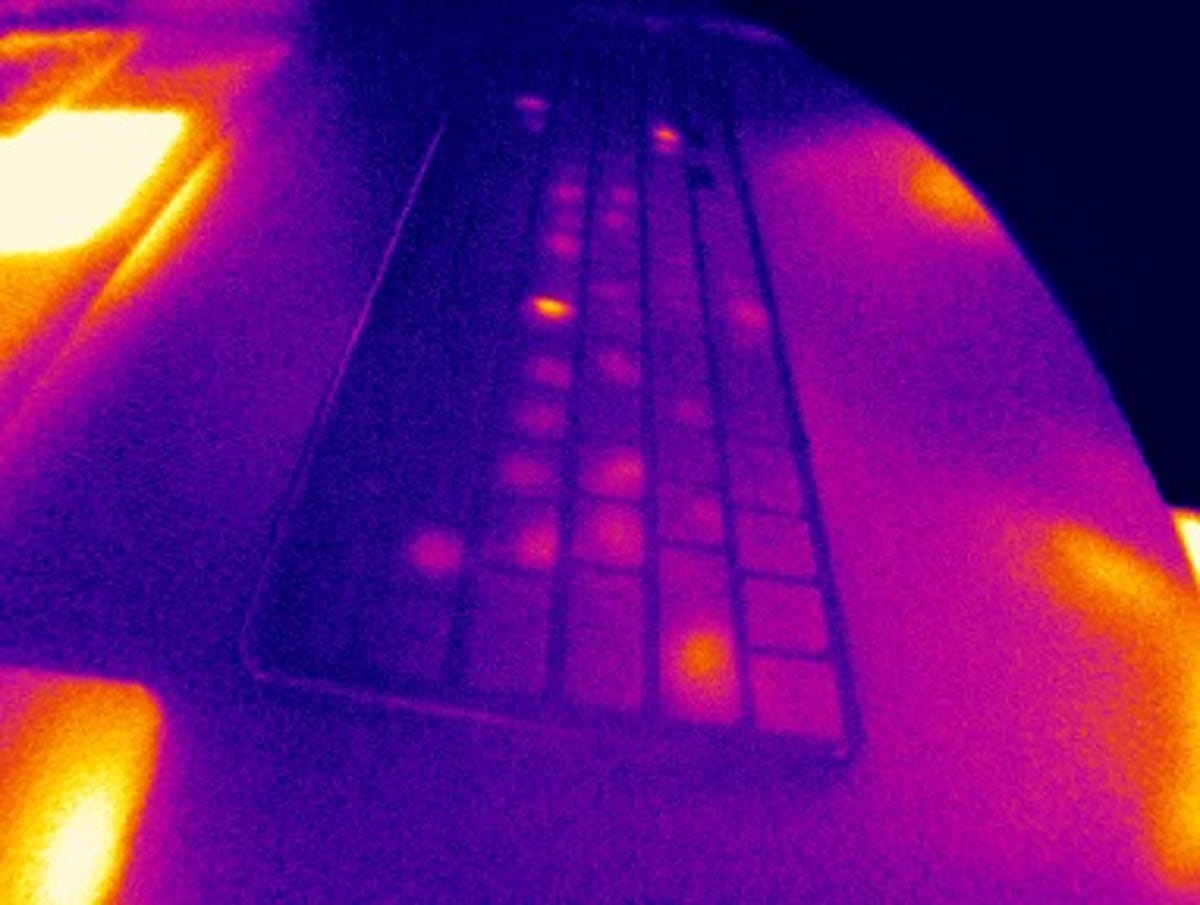
By using a thermal-imaging camera to look at a computer keyboard, smartphone screen or ATM keypad, it's possible to take a picture that reveals the recent heat signature from fingers touching the device.
The brighter the area appears in the thermal image, the more recently it was touched – meaning that the image could be used to crack a password or pin code by analyzing where the keyboard or screen was touched, and when.
Earlier research by the University of Glasgow into thermal attacks has suggested that humans without expertise can guess passwords by looking at thermal images, and now – by adding artificial intelligence – passwords could be cracked even faster by specialist attackers.
Using ThermoSecure to analyse images using AI, 86% of passwords were revealed when thermal images were taken within 20 seconds, 76% could be guessed using images within 30 seconds, and 62% could be discovered after 60 seconds.
The longer the password, the more difficult it was to reveal, but it still proved possible in the majority of cases. ThermoSecure could crack two-thirds of passwords of up to 16 characters and, as passwords get shorter, the more success the system had – 12-character passwords were guessed up to 82% of the time and eight-character passwords were guessed up to 93% of the time.
Passwords made up of six characters or less were successfully cracked 100% of the time – something that could make ATM PIN codes or shorter codes that are used to protect smartphones particularly vulnerable to attacks.
By using this clever technique, a malicious attacker observing potential victims could take a thermal photo of a keyboard, smartphone or ATM and use that to guess passwords. In some cases, they'd also need to physically access the device themselves – but it's also possible that the target could leave their computer unattended.
There's also the possibility that an attacker could already know the username of their target's online account – or they could potentially use the thermal attack to uncover that, too.
The paper on ThermoSecure – authored by the University of Glasgow's Dr Mohamed Kham, Dr John Williamson and Norah Alotaibi – has been released in the hope that it shows the potential risk posed by thermal imaging attacks as the technology used to power them becomes cheaper and more widely available.
"Access to thermal-imaging cameras is more affordable than ever – they can be found for less than £200 – and machine learning is becoming increasingly accessible, too. That makes it very likely that people around the world are developing systems along similar lines to ThermoSecure in order to steal passwords," said Dr Mohamed Khamis, reader in computer science at the University of Glasgow, who led the development of ThermoSecure.
"It's important that computer security research keeps pace with these developments to find new ways to mitigate risk, and we will continue to develop our technology to try to stay one step ahead of attackers," he added.
But while the research demonstrates some advanced techniques that could be used to crack passwords, for users, protecting their accounts is possible by doing one relatively simple thing – using stronger passwords.
"Longer passphrases take longer to type, which also makes it more difficult to get an accurate reading on a thermal camera, particularly if the user is a touch typist," said Dr Khamis, who also suggested that biometric verification also adds protection.
"Users can help make their devices and keyboards more secure by adopting alternative authentication methods, like fingerprint or facial recognition, which mitigate many of the risks of thermal attack."
- Karlston and alf9872000
-

 2
2


Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.