When a London man discovered the front left-side bumper of his Toyota RAV4 torn off and the headlight partially dismantled not once but twice in three months last year, he suspected the acts were senseless vandalism. When the vehicle went missing a few days after the second incident, and a neighbor found their Toyota Land Cruiser gone shortly afterward, he discovered they were part of a new and sophisticated technique for performing keyless thefts.
It just so happened that the owner, Ian Tabor, is a cybersecurity researcher specializing in automobiles. While investigating how his RAV4 was taken, he stumbled on a new technique called CAN injection attacks.
The case of the malfunctioning CAN
Tabor began by poring over the “MyT” telematics system that Toyota uses to track vehicle anomalies known as DTCs (Diagnostic Trouble Codes). It turned out his vehicle had recorded many DTCs around the time of the theft.
The error codes showed that communication had been lost between the RAV4’s CAN—short for Controller Area Network—and the headlight’s Electronic Control Unit. These ECUs, as they’re abbreviated, are found in virtually all modern vehicles and are used to control a myriad of functions, including wipers, brakes, individual lights, and engine. Besides controlling the components, ECUs send status messages over the CAN to keep other ECUs apprised of current conditions.
This diagram maps out the CAN topology for the RAV4:
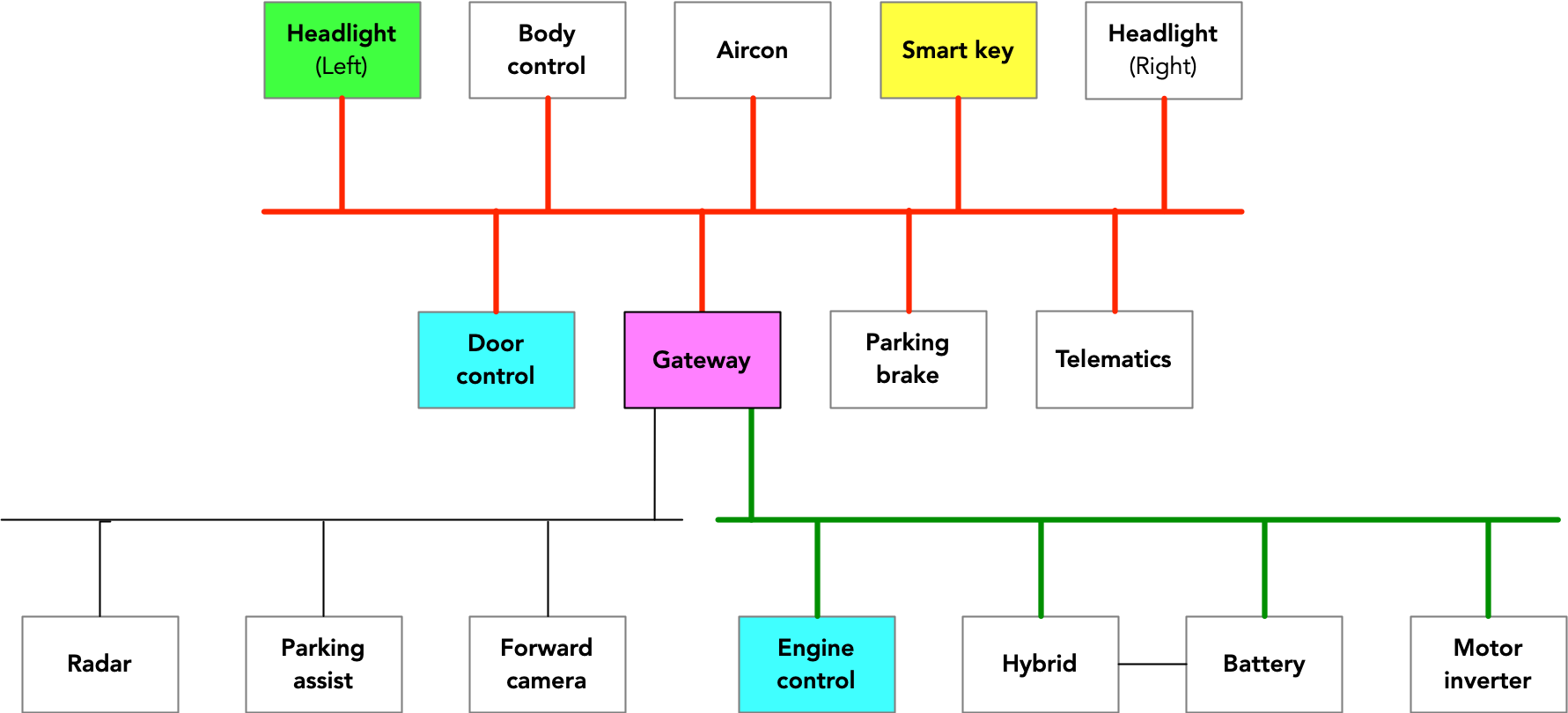
The DTCs showing that the RAV4’s left headlight lost contact with the CAN wasn’t particularly surprising, considering that the crooks had torn off the cables that connected it. More telling was the failure at the same time of many other ECUs, including those for the front cameras and the hybrid engine control. Taken together, these failures suggested not that the ECUs had failed but rather that the CAN bus had malfunctioned. That sent Taber searching for an explanation.
The researcher and theft victim next turned to crime forums on the dark web and YouTube videos discussing how to steal cars. He eventually found ads for what were labeled “emergency start” devices. Ostensibly, these devices were designed for use by owners or locksmiths to use when no key is available, but nothing was preventing their use by anyone else, including thieves. Taber bought a device advertised for starting various vehicles from Lexus and Toyota, including the RAV4. He then proceeded to reverse engineer it and, with help from friend and fellow automotive security expert Ken Tindell, figure out how it worked on the CAN of the RAV4.
Inside this JBL speaker lies a new form of attack
The research uncovered a form of keyless vehicle theft neither researcher had seen before. In the past, thieves found success using what’s known as a relay attack. These hacks amplify the signal between the car and the keyless entry fob used to unlock and start it. Keyless fobs typically only communicate over distances of a few feet. By placing a simple handheld radio device near the vehicle, thieves amplify the normally faint message that cars send. With enough amplification, the messages reach the nearby home or office where the key fob is located. When the fob responds with the cryptographic message that unlocks and starts the vehicle, the crook's repeater relays it to the car. With that, the crook drives off.
“Now that people know how a relay attack works … car owners keep their keys in a metal box (blocking the radio message from the car) and some car makers now supply keys that go to sleep if motionless for a few minutes (and so won’t receive the radio message from the car),” Tindell wrote in a recent post. “Faced with this defeat but being unwilling to give up a lucrative activity, thieves moved to a new way around the security: bypassing the entire smart key system. They do this with a new attack: CAN Injection.”



3175x175(CURRENT).thumb.jpg.b05acc060982b36f5891ba728e6d953c.jpg)

Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.