It's been a quiet week, with even threat actors appearing to take some time off for the holidays. We did not see much research released on ransomware this week, with most of the news focusing on new attacks and LockBit affiliates increasingly targeting hospitals.
These attacks include ones against Yakult Australia and the Ohio Lottery by the new DragonForce ransomware operation.
The most concerning news is that LockBit affiliates increasingly target hospitals in attacks, even though the ransomware operation says it's against the rules.
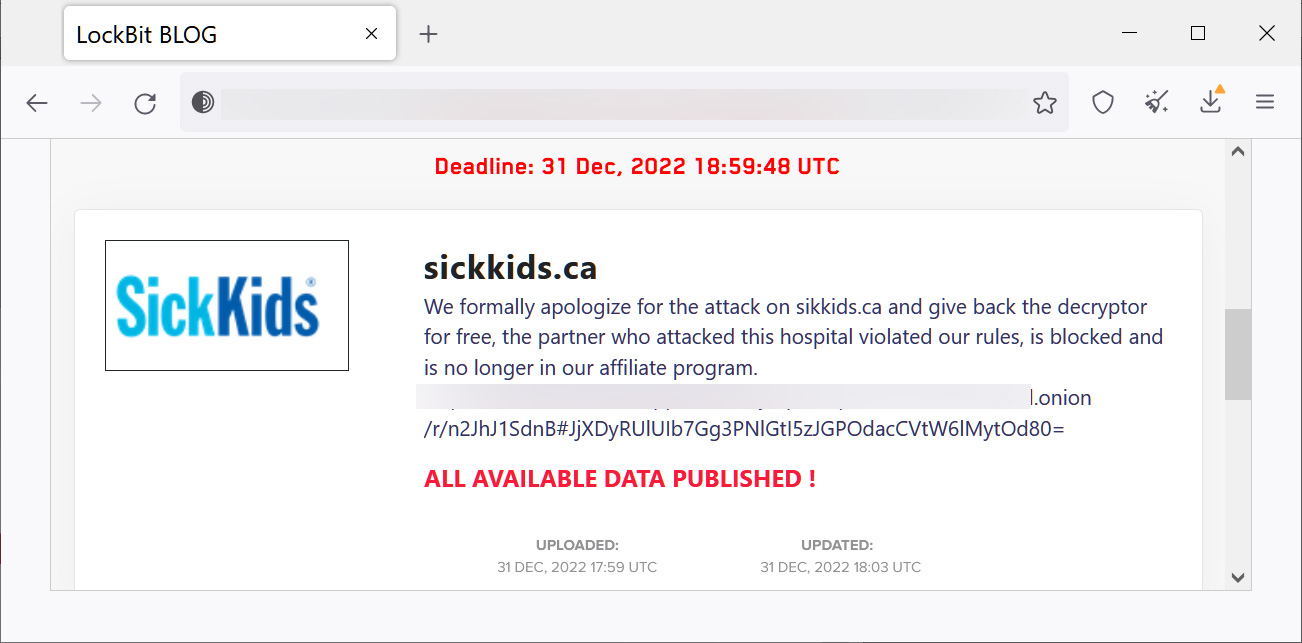
In December 2022, one week before Christmas, a LockBit affiliate attacked the Hospital for Sick Children (SickKids) in Toronto, causing diagnostic and treatment delays. The ransomware operation said this was against the rules and issued a free decryptor.
However, this week, we learned that LockBit attacked three hospitals in Germany, disrupting emergency room services.
We also learned about two New York hospitals seeking a court order to have Boston cloud storage company Wasabi Technologies return stolen data stored on one of its servers by the LockBit ransomware gang.
According to a court order, the Carthage Area Hospital and Claxton-Hepburn Medical Center were attacked in September, with the LockBit affiliate renting cloud storage at Wasabi to store stolen data.
The two hospitals now request that the courts force Wasabi to provide and delete the data from their servers. The court documents indicate that Wasabi is already working with the FBI and has shared a copy of the stolen data with them.
Finally, Microsoft once again disabled the MSIX ms-appinstaller protocol handler after deactivating it in February 2022 and then enabling it again in 2023 for some unknown reason.
However, as malware campaigns continue to abuse this feature, which could lead to ransomware attacks, the feature has again been disabled.
Contributors and those who provided new ransomware information and stories this week include: @malwrhunterteam, @serghei, @demonslay335, @BleepinComputer, @Ionut_Ilascu, @Seifreed, @fwosar, @LawrenceAbrams, @billtoulas, @MsftSecIntel, @DarkWebInformer, @BrettCallow, @pcrisk, and @Fortinet.
December 27th 2023
Yakult Australia confirms 'cyber incident' after 95 GB data leak
Yakult Australia, manufacturer of a probiotic milk drink, has confirmed experiencing a "cyber incident" in a statement to BleepingComputer. Both the company's Australian and New Zealand IT systems have been affected.
Ohio Lottery hit by cyberattack claimed by DragonForce ransomware
The Ohio Lottery was forced to shut down some key systems after a cyberattack affected an undisclosed number of internal applications on Christmas Eve.
Lockbit ransomware disrupts emergency care at German hospitals
German hospital network Katholische Hospitalvereinigung Ostwestfalen (KHO) has confirmed that recent service disruptions at three hospitals were caused by a Lockbit ransomware attack.
New STOP ransomware variant
PCrisk found a new STOP ransomware variant that appends the .cdmx extension.
New ransomware variant
PCrisk found a new ransomware variant that appends the .Tisak extension and drops a ransom note named Tisak_Help.txt.
December 28th 2023
Microsoft disables MSIX protocol handler abused in malware attacks
Microsoft has again disabled the MSIX ms-appinstaller protocol handler after multiple financially motivated threat groups abused it to infect Windows users with malware.
New Live Team ransomware
PCrisk found a new Live Team ransomware that appends the .LIVE and drops a ransom note named FILE RECOVERY_ID_[victim's_ID].txt.
New SNet ransomware
PCrisk found a new ransomware variant that appends the .SNet extension and drops a ransom note named DecryptNote.txt.
Ransomware Roundup - 8base
8base is a financially motivated ransomware variant most likely based on the Phobos ransomware. Per our FortiRecon information, the 8base ransomware first appeared in May 2023.
December 29th, 2023
Hospitals ask courts to force cloud storage firm to return stolen data
Two not-for-profit hospitals in New York are seeking a court order to retrieve data stolen in an August ransomware attack that's now stored on the servers of a Boston cloud storage company.
That's it for this week! Hope everyone has a nice weekend!
- aum
-

 1
1



3175x175(CURRENT).thumb.jpg.b05acc060982b36f5891ba728e6d953c.jpg)
Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.