The world of cybercrime is moving quickly. Threat actors, ransomware gangs, malware developers, and others are increasingly and rapidly moving off of the "traditional" dark web (Tor sites) and onto illicit Telegram channels specializing in cybercrime.
This Flare article will examine the reasons why threat actors are shifting from Tor and provide detailed guidance for best practices in monitoring Telegram channels.
Why Are Threat Actors Moving from Tor to Telegram?
Today we see a majority of cybercrime activity occurring off of the traditional dark web and on modern social media applications.
There are a myriad of reasons for the switch including the commodification of cybercrime, increasing law enforcement scrutiny on Tor sites, and the general slowness of Tor. We’ll cover each in turn.
Lack of Exit Scams
One of the biggest upsides and downsides to traditional dark web marketplaces is that the marketplace acts as a clearinghouse.
Typically, there is a 14 day hold on transactions in which the marketplace holds onto cryptocurrency and in which the buyer can request recourse if they are scammed.
The challenge becomes that in many cases marketplace owners may be holding millions of dollars in crypto at any given time, creating a strong incentive to exit scam and steal the money being held.
Amenities of Modern Social Media
Compared to Tor sites, Telegram has an advantage in these following areas:
- Telegram is fast, and has many of the amenities that modern social media applications have such as emojis, direct private chats, a phone application, and other nice to haves
- Level of technical proficiency to find cybercrime channels and successfully make purchases is even lower than Tor, creating a democratization of cybercrime data
- Many channels exist which provide free "samples" of credentials, stealer logs, data from breaches, and other data which can provide an easy way for users to "validate" the effectiveness of the vendors offerings
Perceived Anonymity
It’s no secret that Tor marketplaces, forums, and sites are heavily monitored by law enforcement organizations. Users know when they make a forum post or marketplace listing will likely be seen by enterprise security teams, dozens of law enforcement agencies, and many others.
Conversely Telegram provides perceived anonymity given the thousands of channels specializing in cybercrime, the lack of IP tracking available to security and LE professionals, and the seeming ephemeral nature of messages.
Types of Cybercrime Telegram Channels
Compared to legacy dark web marketplaces, Telegram channels tend to specialize in one particular type of criminal activity. A dark web marketplace may offer a criminal the ability to buy drugs, guns, credit card numbers, combolists and dozens of other illicit goods.
Telegram channels by contract act as a single shop for a single type of goods and can be classified based on what they are offering.
The following categories we’ve identified are not exhaustive:
Stealer Log Distribution
Stealer logs represent data from devices infected with infostealer malware. They typically include the browser fingerprint, saved passwords in the browser, clipboard data, credit card data saved in the browser, cryptocurrency wallet information, and relevant information.
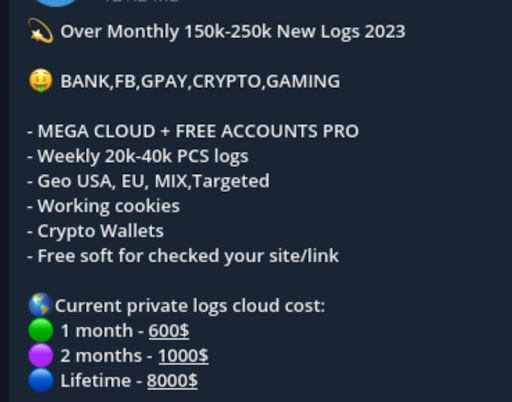
An individual log ›represents data from one computer. Stealer log channels on Telegram come in two types:
Open Access Stealer Log Channels
These channels routinely distribute megabyte-gigabyte sized files that contain hundreds, thousands, or in some cases hundreds of thousands of individual stealer logs.
These can be seen as an extended advertisement for private, invite only log channels and as a way for the vendors to prove that the logs they are providing are high-quality and contain valuable credentials.
VIP Stealer Log Channels
VIP stealer logs channels provide a limited number of threat actors access to "premium" logs which are supposedly directly from the source and untouched by other threat actors. Typically the price for access to these channels ranges from $200-$400 a month paid in Monero.
We suspect that many initial access brokers sift through logs posted in these channels to identify specific logs that have corporate access, validate the access, and then resell the access on top-tier cybercrime forums such as Exploit or XSS.
Financial Fraud
Another type of channel we commonly see are financial fraud channels in which bank account, credit card, and refund information is given out in bulk. These channels typically sub-specialize in their particular "type" of crime for example.
- Credit Card Numbers
- Bank Accounts
- Refunding Guides
- SIM Swapping
- Gift Card Fraud
Combolists & Credentials
Another common and critical type of channel to monitor are channels providing combolists. Combolists are "curated" lists of stolen usernames and passwords, sometimes accompanied by names, emails and other identifying information that criminals use to attempt account takeover attacks.
Combolists can be created based on geography, industry, account access and other features that make them high-value for threat actors.
In many cases usernames, emails, and passwords are pasted directly into the Telegram chat. In other cases threat actors may provide files that contain thousands or tens of thousands of data points (and often are accompanied by malware).
Nation State Hacktivism
The last category of channels that is particularly relevant for cybersecurity teams are nation-state hacktivist channels. Channels such as Bloodnet, Killnet, Noname47, Anonymous Sudan, and others have exploded in popularity, particularly since the beginning of the war in Ukraine.
These channels typically pick specific targets, often critical infrastructure in NATO countries and attempt to deface websites, DDoS vital services, and leak data from companies.
- Mutton
-

 1
1



3175x175(CURRENT).thumb.jpg.b05acc060982b36f5891ba728e6d953c.jpg)
Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.