2023 was a big year for cybersecurity, with significant cyberattacks, data breaches, new threat groups emerging, and, of course, zero-day vulnerabilities.
Some stories, though, were more impactful or popular with our 22 million readers than others.
Below are fourteen of what BleepingComputer believes are the most impactful cybersecurity stories of 2023, with a summary of each.
14. The 23andMe data breach
Genetic testing provider 23andMe suffered credential stuffing attacks that led to a major data breach, exposing the data of 6.9 million users.
The company states that the attackers only breached a small number of accounts during the credential-stuffing attacks. However, the threat actors were able to abuse other features to scrape millions of individuals' data.
The threat actors attempted to sell the stolen data, but after not receiving buyers, leaked the data for 1 million Ashkenazi Jews and 4,011,607 people living in Great Britain on a hacking forum.
In a recent update, 23andMe told BleepingComputer that the breach impacted 6.9 million people — 5.5 million through the DNA Relatives feature and 1.4 million through the Family Tree feature.
This breach has led to multiple class action lawsuits against the company for not adequately protecting data.
13. Hosting firm says it lost all customer data after ransomware attack
Two Danish hosting providers were forced to shut down after a ransomware attack encrypted the majority of customer data, and data restoration was not successful.
"Since we neither can nor wish to meet the financial demands of the criminal hackers for a ransom, CloudNordic's IT team and external experts have been working intensively to assess the damage and determine what could be recovered," reads CloudNordic's statement (machine translated)
"Sadly, it has been impossible to recover more data, and the majority of our customers have consequently lost all their data with us."
12. Anonymous Sudan hacktivists show that DDoS attacks can impact the largest tech firms
A hacktivist group known as Anonymous Sudan took everyone by surprise when their DDoS attacks took down the websites and services of some of the largest tech firms in the world.
The group's attacks gained wide media attention when they successfully took down login pages for Microsoft's services, including Outlook, OneDrive, and the Azure portal.
Over a week later, Microsoft finally confirmed that DDoS attacks caused these outages.
"Beginning in early June 2023, Microsoft identified surges in traffic against some services that temporarily impacted availability," confirmed Microsoft.
"Microsoft promptly opened an investigation and subsequently began tracking ongoing DDoS activity by the threat actor that Microsoft tracks as Storm-1359."
Anonymous Sudan later targeted numerous other websites, including those for ChatGPT, Cloudflare, and U.S. government services.
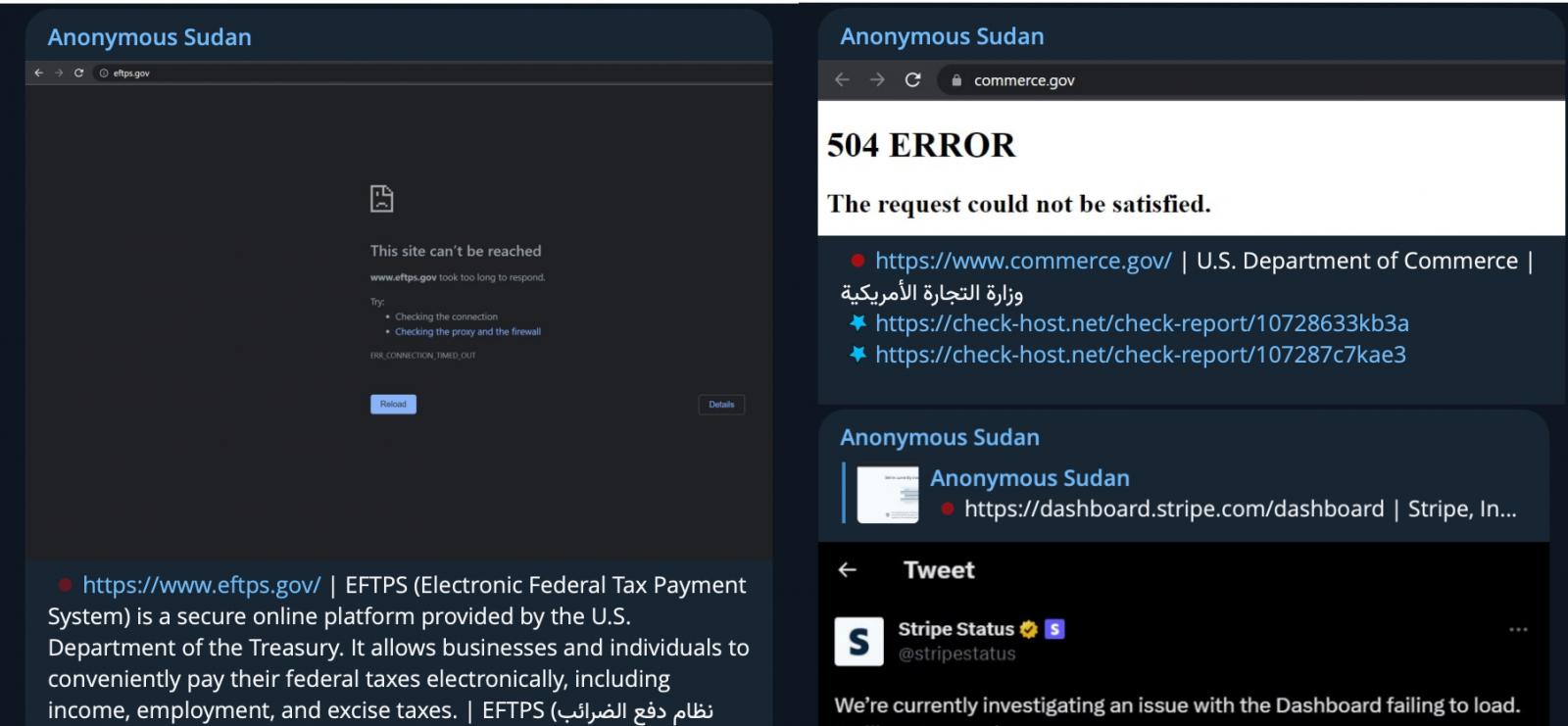
The increasing DDoS attacks and their impact led the U.S. Cybersecurity and Infrastructure Security Agency (CISA) to release an advisory about these incidents.
11. New acoustic attack steals data from keystrokes with 95% accuracy
A team of researchers from British universities trained a deep learning model to steal data from keyboard keystrokes recorded using a microphone with an accuracy of 95%.
When Zoom was used for training the sound classification algorithm, the prediction accuracy dropped to 93%, which is still extremely high.
To mitigate these attacks, the researchers suggest users may try altering typing styles or using randomized passwords. Other defense measures include using software to reproduce keystroke sounds, play white noise, or software-based keystroke audio filters.
10. PayPal accounts breached in large-scale credential stuffing attack
PayPal suffered a credential stuffing attack between December 6 and December 8, 2022, allowing attackers to access 34,942 accounts.
Credential stuffing is an attack where hackers attempt to access an account by trying out username and password pairs sourced from data leaks on various websites.
Hackers had access to account holders' full names, dates of birth, postal addresses, social security numbers, and individual tax identification numbers.
9. Dish Network goes offline after likely cyberattack, employees cut off
American T.V. giant and satellite broadcast provider DISH Network mysteriously went offline earlier this year, with its websites and mobile apps not working for days.

DISH later confirmed that the outage was caused by a ransomware attack, with BleepingComputer first to report that the Black Basta ransomware gang was behind the attack.
Employees told BleepingComputer that the ransomware gang compromised the company's Windows domain controllers and encrypted VMware ESXi servers and backups.
DISH data breach notifications confirmed that data was stolen in the attack and hinted that a ransom was paid not to release the stolen data.
"We are not aware of any misuse of your information, and we have received confirmation that the extracted data has been deleted," read the data breach notification.
8. GoDaddy: Hackers stole source code, installed malware in multi-year breach
Web hosting giant GoDaddy says it suffered a multi-year breach allowing unknown attackers to steal source code and install malware on its servers.
This breach began in 2021 and allowed the threat actors access to the personal information of 1.2 million Managed WordPress customers, including credentials, and also used the access to redirect websites to other domains.
No threat actors ever claimed responsibility for this attack.
7. MGM Resorts cyberattack shuts down IT systems after cyberattack
MGM Resorts International suffered a massive attack that impacted numerous systems, including its main website, online reservations, and in-casino services, like ATMs, slot machines, and credit card machines.
The BlackCat ransomware operation claimed the attack, whose affiliates said they encrypted over 100 ESXi hypervisors during the incident.
Bloomberg reported that the same group also breached Caesars Entertainment's network, providing a strong hint in a Form 8-K SEC filing that they paid the attackers to prevent a leak of customers' stolen data.
While the attack was significant, it also brought wide attention to a loose-knit group of hackers known as Scattered Spider.
Scattered Spider, also known as 0ktapus, Starfraud, UNC3944, and Muddled Libra, is adept at social engineering and relies on phishing, multi-factor authentication (MFA) bombing (targeted MFA fatigue), and SIM swapping to gain initial network access on large organizations.
Members of this collective are affiliates of the BlackCat ransomware gang and include young English-speaking members with diverse skill sets who frequent the same hacking forums and Telegram channels.
While many believe this is a cohesive gang, the group is a network of individuals, with different threat actors participating in each attack. This fluid structure is what makes it challenging to track them.
In November, the FBI released an advisory highlighting the group's tactics, techniques, and procedures (TTPs).
Scattered Spider is behind previous attacks on Reddit, MailChimp, Twilio, DoorDash, and Riot Games.
6. Hackers compromise 3CX desktop app in a supply chain attack
3CX was breached by the North Korean Lazarus hacking group to push malware through a supply chain attack using the company's Voice Over Internet Protocol (VOIP) desktop client.
3CX is a VoIP IPBX software development company whose 3CX Phone System is used by more than 350,000 companies worldwide and has over 12 million daily users.
3CX was breached after an employee installed a trojanized version of Trading Technologies' X_TRADER software, which allowed the threat actors to steal corporate credentials and breach the network.
The attackers pushed out a malicious software update that installed a previously unknown information-stealing malware to steal data and credentials stored in Chrome, Edge, Brave, and Firefox user profiles.
5. Barracuda says hacked ESG appliances must be replaced immediately
In May, Barracuda disclosed that some of their Email Security Gateway (ESG) appliances were hacked using a zero-day vulnerability to install malware and steal data.
We later learned that the attacks were linked to Chinese threat actors, who used the vulnerability since 2022 to infect ESG devices with new malware named 'Saltwater,' 'Seaspy,' and 'Seaside.'
CISA later disclosed that Submarine and Whirlpool malware were also used in the attacks to backdoor ESG devices.
What stood out from these attacks is that instead of using a software fix for impacted ESG devices, Barracuda warned customers they must replace their Email Security Gateway (ESG) appliances, which was done free of charge.
"Impacted ESG appliances must be immediately replaced regardless of patch version level," the company warned at the time.
"Barracuda's remediation recommendation at this time is full replacement of the impacted ESG."
This unusual request led many to believe that the threat actors compromised the devices at a low level, making it impossible to ensure they were completely clean.
Mandiant, who was part of the incident response in these attacks, told BleepingComputer that this was recommended out of caution, as Barracuda could not ensure the complete removal of malware.
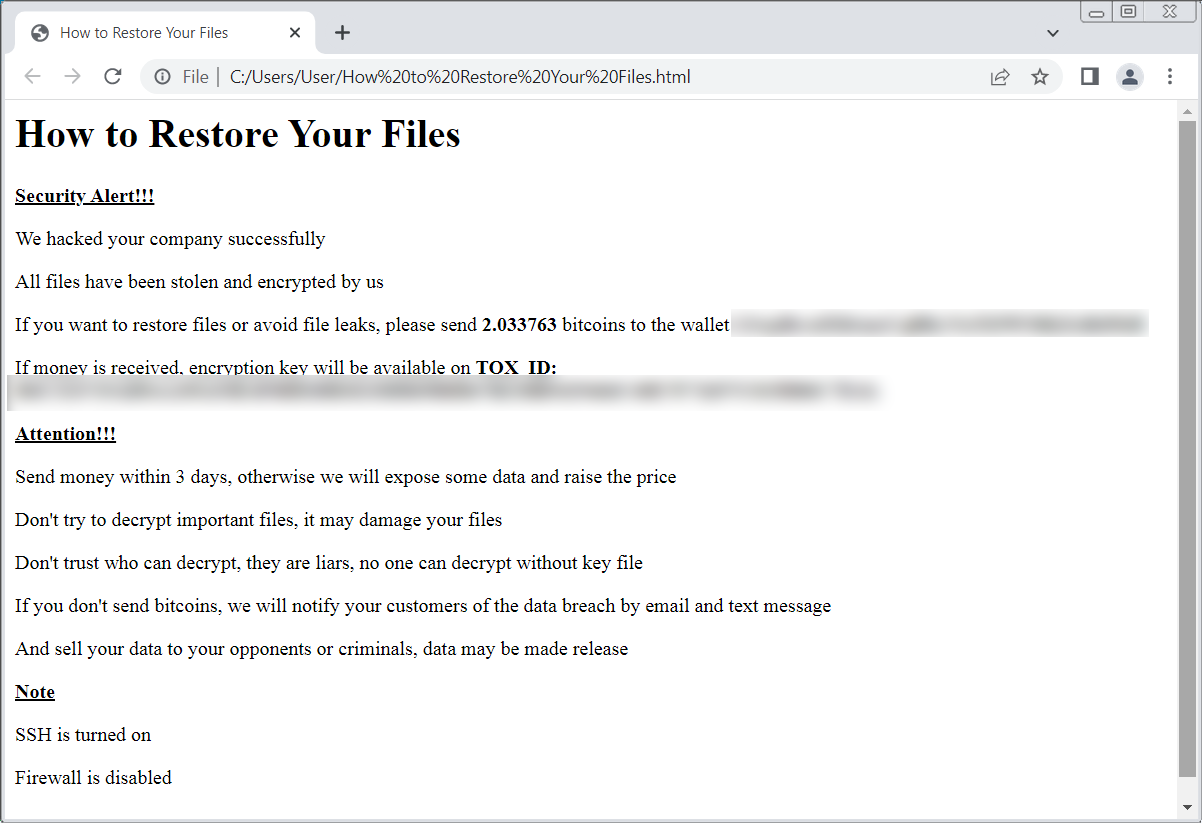
4. Massive ESXiArgs ransomware attack targets VMware ESXi servers worldwide
In February 2023, a massive ransomware campaign targeted exposed VMware ESXi servers worldwide, quickly encrypting the virtual machines for thousands of companies.
Just hours after the attack, victims began reporting in the BleepingComputer's forum that files with vmxf, .vmx, .vmdk, .vmsd, and .nvram, all files associated with VMware ESXi virtual machines, were encrypted.
The ransomware campaign was dubbed ESXiArgs due to an .args file being created for every encrypted file.
The VMware ESXi console home page was modified to show a ransom note demanding 2.0781 bitcoins, worth approximately $49,000 at the time.
3. Brazil seizing Flipper Zero shipments to prevent use in crime
One of BleepingComputer's most-read stories of the year was the news that the Brazilian National Telecommunications Agency seized incoming Flipper Zero purchases for their potential to be used in criminal activity.
Brazilians who purchased the Flipper Zero reported that their shipments were redirected to Brazil's telecommunications agency, Anatel, due to a lack of certification with the country's Radio Frequencies department.
From emails seen by BleepingComputer, Anatel flagged the device as a tool used for criminal purposes.
2. The Operation Triangulation iPhone attacks
In June, researchers from Kaspersky first disclosed a new zero-click iOS attack called "Operation Triangulation" used to install the TriangleDB spyware on iPhones.
Kaspersky discovered the attack on devices within its own network, and Russia's FSB intelligence service accused Apple of providing the NSA with a backdoor. However, the true origins of the attack remain unknown, and there is no proof that the U.S. government is behind the attacks.
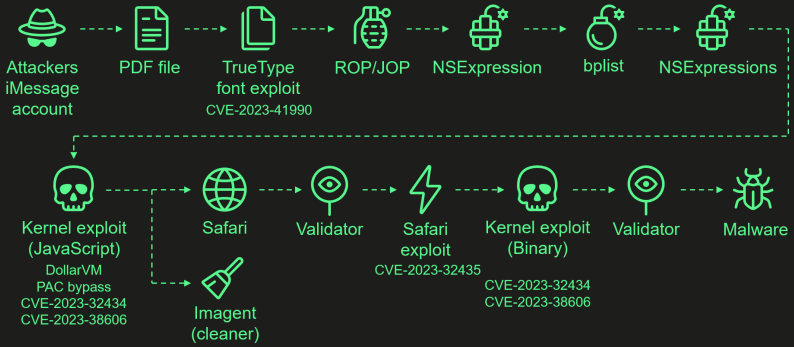
The attacks start with the hackers sending a malicious iMessage attachment that, when processed by iOS, automatically triggers a zero-click exploit chain. A zero-click exploit means it does not require interaction from the user to be triggered.
The attacks chained together four zero-day iOS vulnerabilities listed below to install the spyware:
- CVE-2023-41990: A vulnerability in the ADJUST TrueType font instruction allowing remote code execution through a malicious iMessage attachment.
- CVE-2023-32434: An integer overflow issue in XNU's memory mapping syscalls, granting attackers extensive read/write access to the device's physical memory.
- CVE-2023-32435: Used in the Safari exploit to execute shellcode as part of the multi-stage attack.
- CVE-2023-38606: A vulnerability using hardware MMIO registers to bypass the Page Protection Layer (PPL), overriding hardware-based security protections.
Last week, Kaspersky disclosed that the final zero-day vulnerability, CVE-2023-38606, abused an undocumented feature in Apple chips to bypass hardware-based security protections.
While the Operation Triangulation attacks did not impact many devices, it could be one of the most sophisticated iOS attacks seen to date.
While it's still unknown who is behind the attacks, their sophistication has led cybersecurity researchers to believe that a government-sponsored hacking group is behind them.
1. The MOVEit Transfer data theft attacks
BleepingComputer was the first to report the widespread data-theft attacks exploiting a zero-day vulnerability in the MOVEit Transfer secure file transfer platform.
MOVEit Transfer is a managed file transfer (MFT) solution developed by Ipswitch, a subsidiary of US-based Progress Software Corporation, that allows the enterprise to securely transfer files between business partners and customers using SFTP, SCP, and HTTP-based uploads.
This vulnerability allowed the threat actors to breach MOVEit Transfer servers and download the stored data.
The attacks were soon claimed by the Clop ransomware gang, who previously launched similar attacks through zero-day vulnerabilities in Accellion FTA and GoAnywhere.
According to Emsisoft, 2,706 organizations were breached using this vulnerability, exposing the personal data of over 93 million people.



3175x175(CURRENT).thumb.jpg.b05acc060982b36f5891ba728e6d953c.jpg)


Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.