What do Boeing, an Australian shipping company, the world’s largest bank, and one of the world’s biggest law firms have in common? All four have suffered cybersecurity breaches, most likely at the hands of teenage hackers, after failing to patch a critical vulnerability that security experts have warned of for more than a month, according to a post published Monday.
Besides the US jetliner manufacturer, the victims include DP World, the Australian branch of the Dubai-based logistics company DP World; Industrial and Commercial Bank of China; and Allen & Overy, a multinational law firm, according to Kevin Beaumont, an independent security researcher with one of the most comprehensive views of the cybersecurity landscape. All four companies have confirmed succumbing to security incidents in recent days, and China’s ICBC has reportedly paid an undisclosed ransom in exchange for encryption keys to data that has been unavailable ever since.
Citing data allowing the tracking of ransomware operators and people familiar with the breaches, Beaumont said the four companies are among 10 victims he’s aware of currently being extorted by LockBit, among the world’s most prolific and damaging ransomware crime syndicates. All four of the companies, Beaumont said, were users of a networking product known as Citrix Netscaler and hadn’t patched against a critical vulnerability despite a patch being available since October 10.
Dubbed CitrixBleed and carrying a severity rating of 9.4 out of a possible 10, the easy-to-exploit vulnerability exposes session tokens that allow the bypassing of all multifactor authentication controls inside a vulnerable network. Attackers are left with the equivalent of a point-and-click desktop PC within the impacted victim’s internal network, where they’re then free to roam.
Beaumont wrote:
Ransomware groups are often staffed by almost all teenagers and haven’t been taken seriously for far too long as a threat. They are a threat to civil society as long as organizations keep paying.
Focusing on cybersecurity fundamentals for enterprise scale organizations is a challenge, as often people are chasing after the perceived next big thing—metaverse (remember that?), NFTs, generative AI—without being able to do the fundamentals well. Large scale enterprises need to be able to patch vulnerabilities like CitrixBleed quickly.
The cybersecurity reality we live in now is teenagers are running around in organized crime gangs with digital bazookas. They probably have a better asset inventory of your network than you, and they don’t have to wait 4 weeks for 38 people to approve a change request for patching 1 thing.
Know your network boundary and risky products as well as LockBit do. You need to be able to identify and patch something like CitrixBleed within 24 hours—if you cannot, there is a very real possibility it isn’t the ideal product fit for your organization due to the level of risk it poses, and you need to rethink if the architecture of your house is fit for purpose.
Vendors like Citrix need to have clear statements of intent for securing their products, as piling on patch after patch after patch is not sustainable for many organizations—or customers should opt with their wallets for more proven solutions. The reality is many vendors are shipping appliance products with cybersecurity standards worse than when I started my career in the late '90s—while also advertising themselves as the experts. Marketing is a hell of a drug.
Beaumont cited query results returned by the Shodan search service that indicated all four of the organizations had not patched CitrixBleed at the time they were hacked. The vulnerability is tracked as CVE-2023-4966.
-
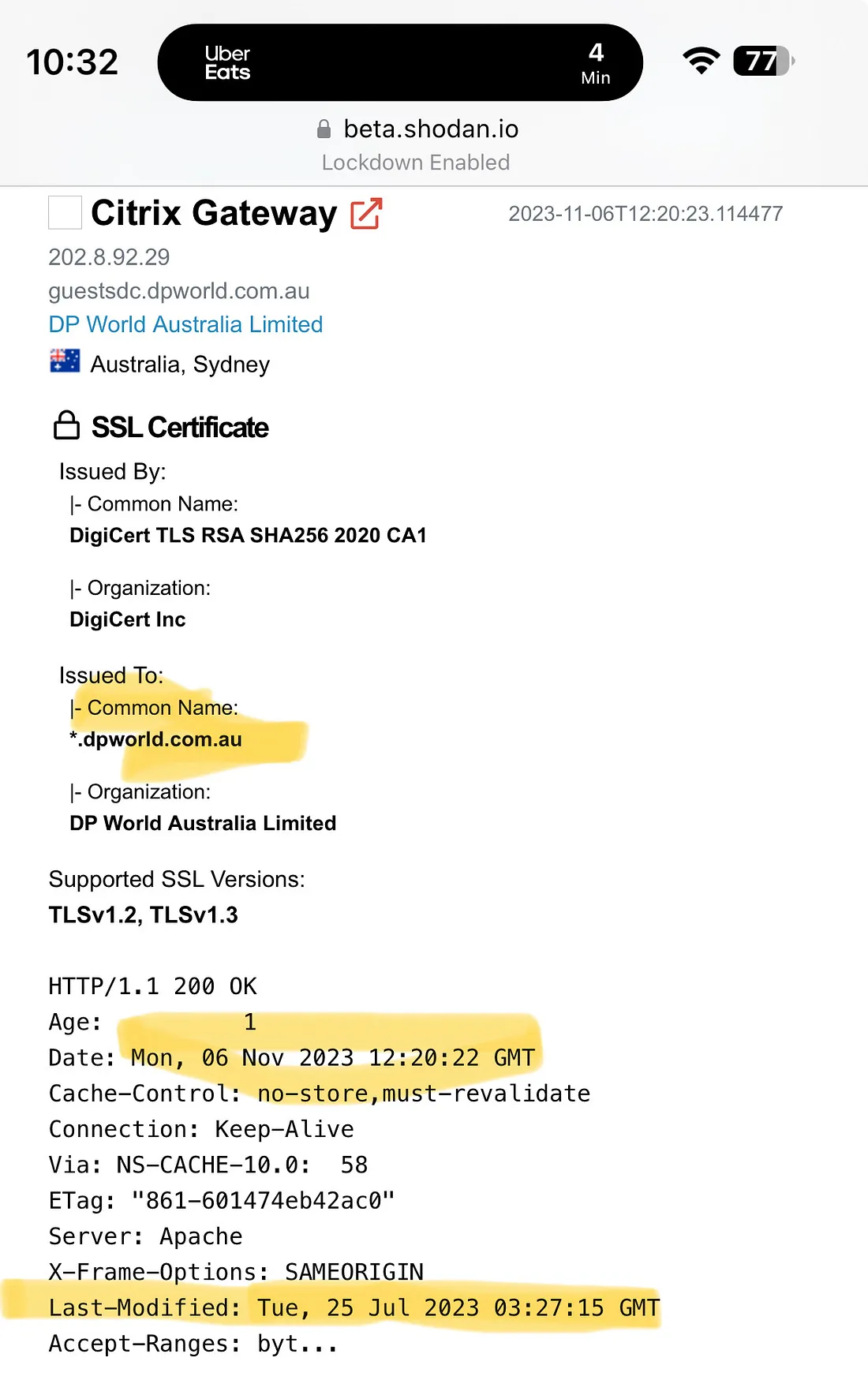 An entry from Shodan indicating DP World wasn't patched against CitrixBleed.Kevin Beaumont
An entry from Shodan indicating DP World wasn't patched against CitrixBleed.Kevin Beaumont -
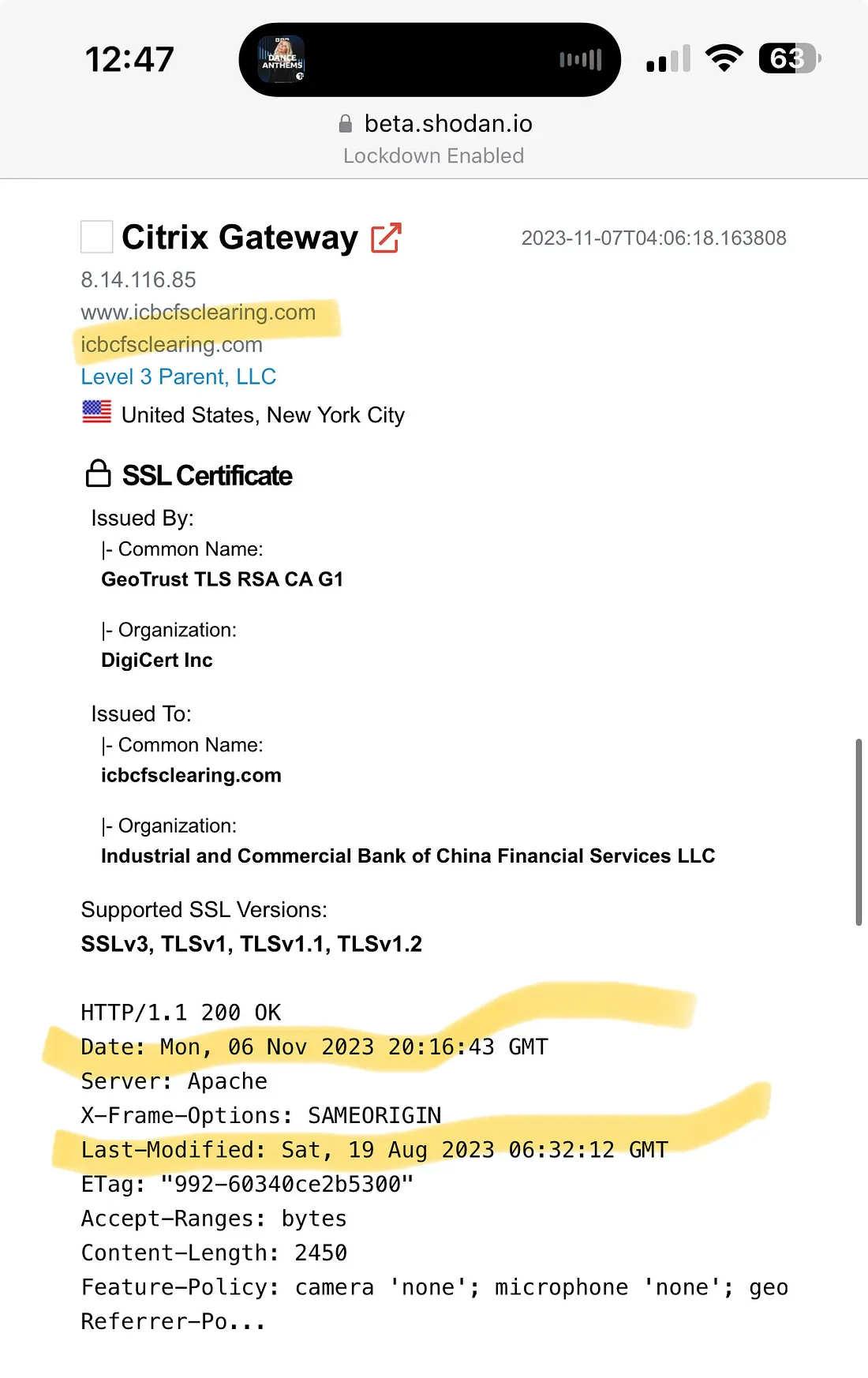 An entry from Shodan indicating ICBC wasn't patched against CitrixBleed.Kevin Beaumont
An entry from Shodan indicating ICBC wasn't patched against CitrixBleed.Kevin Beaumont -
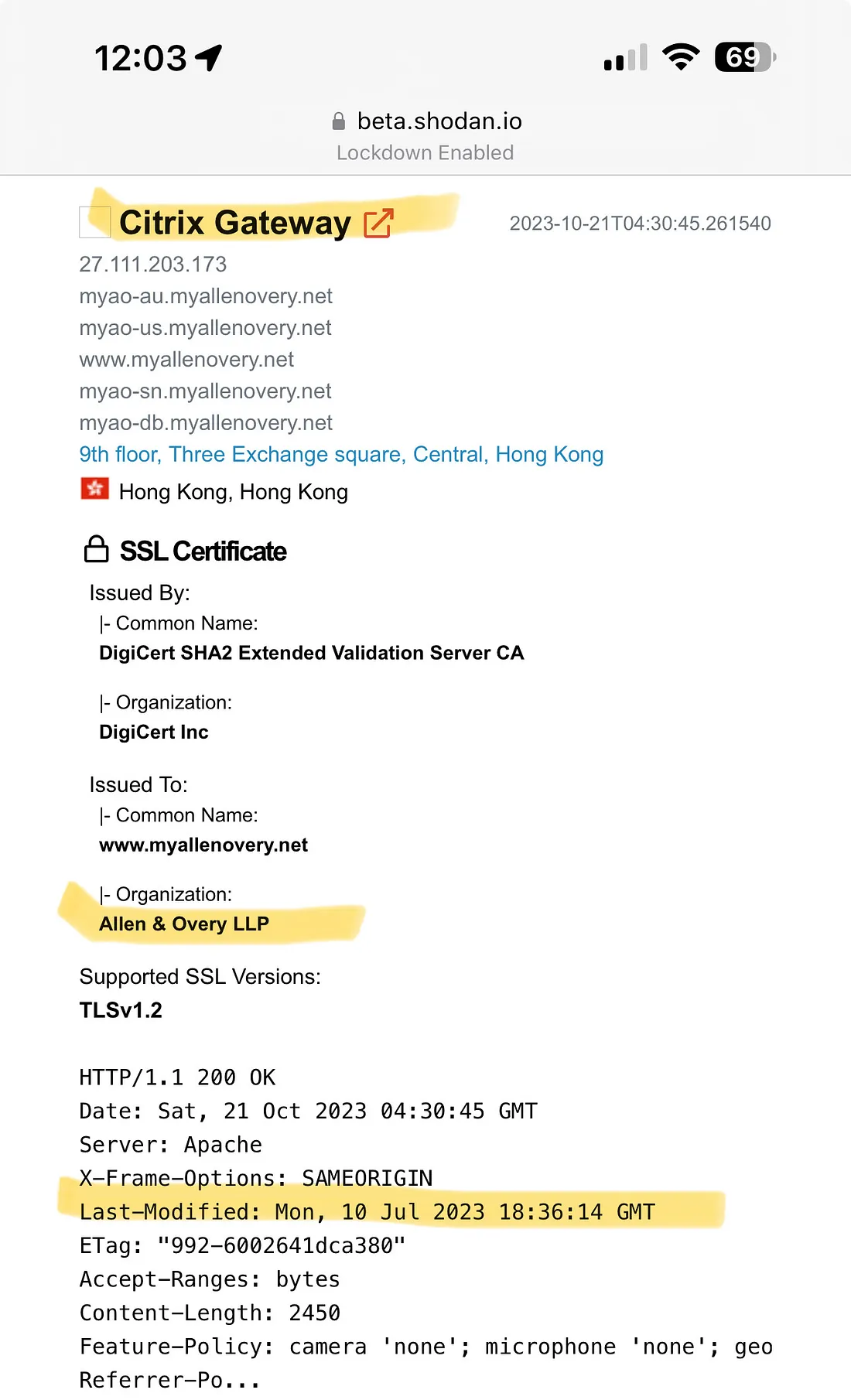 An entry from Shodan indicating Allen & Overy wasn't patched against CitrixBleed.Kevin Beaumont
An entry from Shodan indicating Allen & Overy wasn't patched against CitrixBleed.Kevin Beaumont



3175x175(CURRENT).thumb.jpg.b05acc060982b36f5891ba728e6d953c.jpg)
Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.